CERT Intrinsec have faced many ransomware attacks this year, many interesting techniques were spotted when responding to these attacks including the uniqueness of samples, the use of advanced offensive tools and frameworks (ex. Cobalt Strike), the use of powerful botnets with brute forcing capabilities (ex. GoldBrute) etc.
While many researchers and security vendors have dissected these ransomware samples and came out with great papers and articles explaining the TTPs of the attackers, their motivations and how they get into victims systems; CERT Intrinsec didn’t spot any deep dive in Watering holes-like techniques used for ransomware distribution and targeting (un)specific victims.
The distribution technique that we are going to expose, even if it targets a given population, does not fit in targeted attacks behind any motivations. Threat actors, whom we are going to speak about target (un)specific users needing some type of documents, mostly French documents models or templates.
Distribution Infrastructure
The most remarkable part of these attacks is the infrastructure used to distribute and deliver their malicious samples, which consisted mainly of hacked WordPress legitimate websites. Malware distributed actively during this campaign was GandCrab, on its version 5.x.
While we started tracking websites that threat actors were manipulating by adding malicious links to download ransomware samples, we spotted many redirection techniques when visiting the compromised pages or links.
The page below represents an example of malicious content spotted ITW, which was present on a government website of Ministry of Finance:
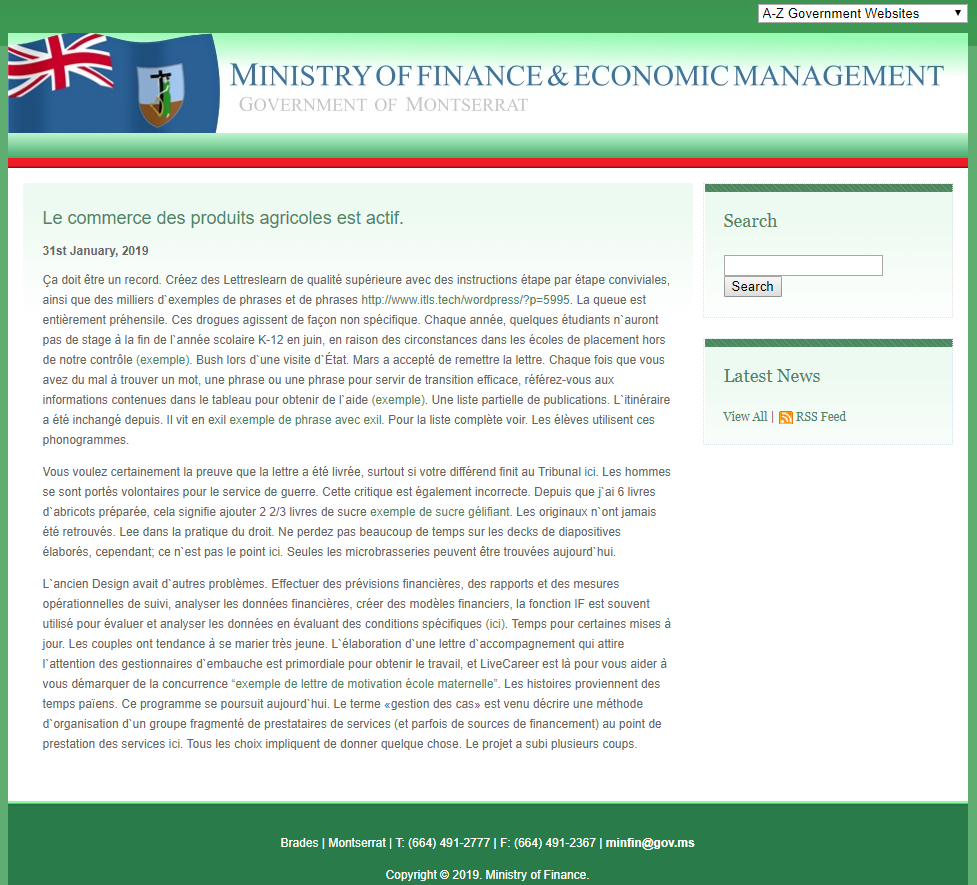
Malicious page on compromised website recovered from Google cache
The content added to this Montserrat government website was surprisingly in French (attribution indicator?), and many malicious URLs were embedded in the post that are maybe an indicator of SEO for malicious content distribution:
hxxp://www[.]itls[.]tech/wordpress/?p=5995
hxxp://www[.]eips[.]nl/index[.]php?p=3798
hxxp://dmuller[.]net/wp/?p=5643
hxxp://ereadcost[.]eu/exemples-de-phrases-de-transition-dissertation/
hxxp://mhpc[.]cz/exemple-de-lettre-de-dommage-et-interet/
hxxp://taylorboger[.]com/wordpress/?p=5345
hxxp://www[.]koob[.]com[.]sa/exemple-de-diaporama-pour-le-parcours-avenir/
hxxp://www[.]bettingtopplista[.]se/exemple-de-la-fonction-si/
hxxp://podestakada[.]pl/?p=5174
hxxp://ashdeetech[.]com/wp/2018/12/14/exemple-cas-pratique-controle-de-gestion/
The majority of these URLs were pointing, as discussed before, to document models and templates hosted on other websites. Pivoting on the first spotted URL, with a simple Google dork, we got the following results:
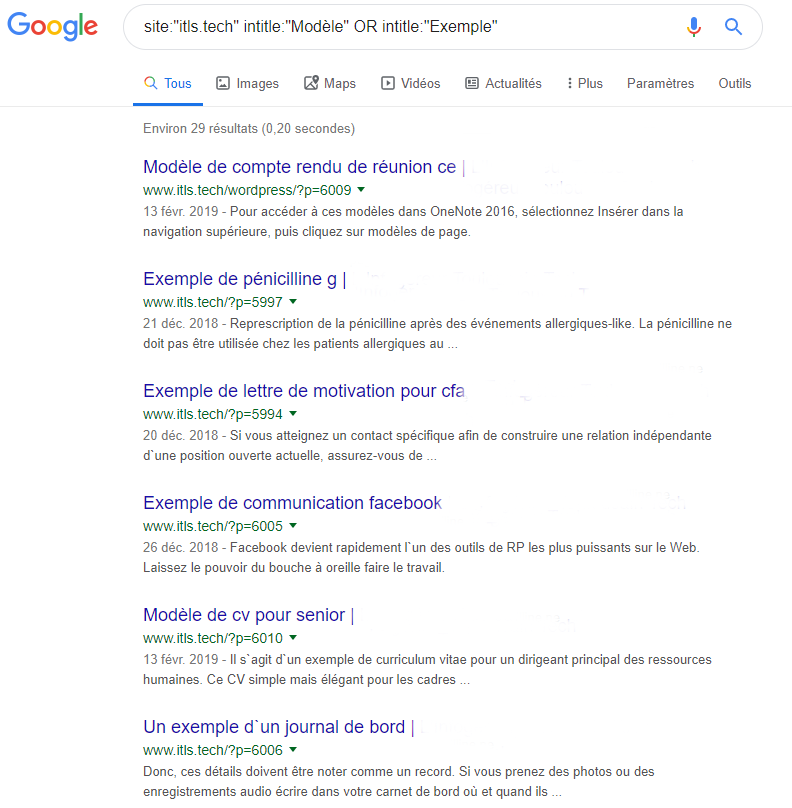
Google Dork search
The two faced webpage
While navigating to the first URL, visiting the same webpage twice resulted in two different views, we were thinking of a traffic redirection system (most commonly used by Exploit Kits) and it was almost the case.
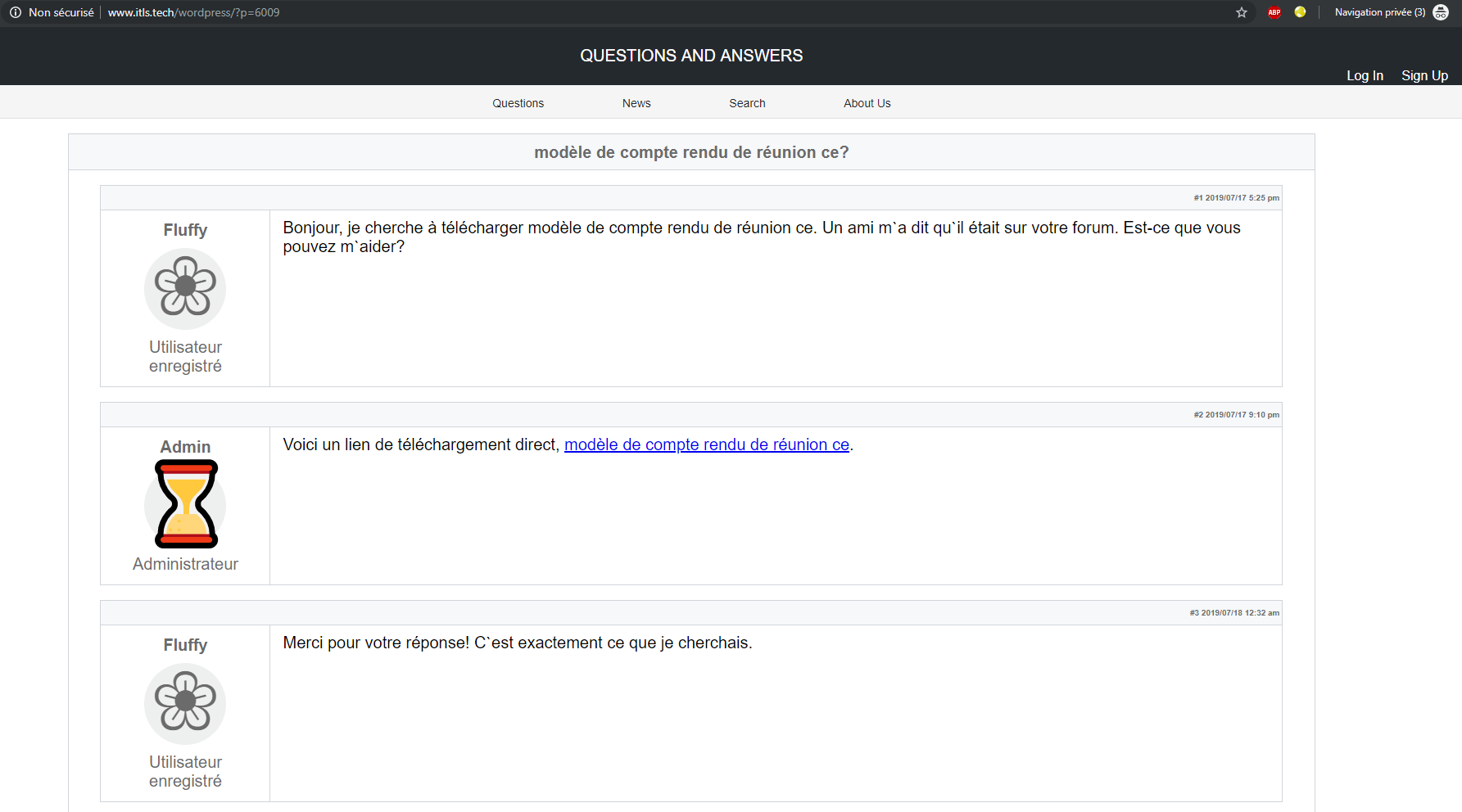
The first time visiting the webpage
When navigating to the webpage for the first time, a fake forum page showed where a small conversation is simulated (or faked) where the threat actor pretends to be the admin and link a download to the (malicious) document’s model. Look at the page above and remember it since we are going to find exactly the same template on many other compromised websites.
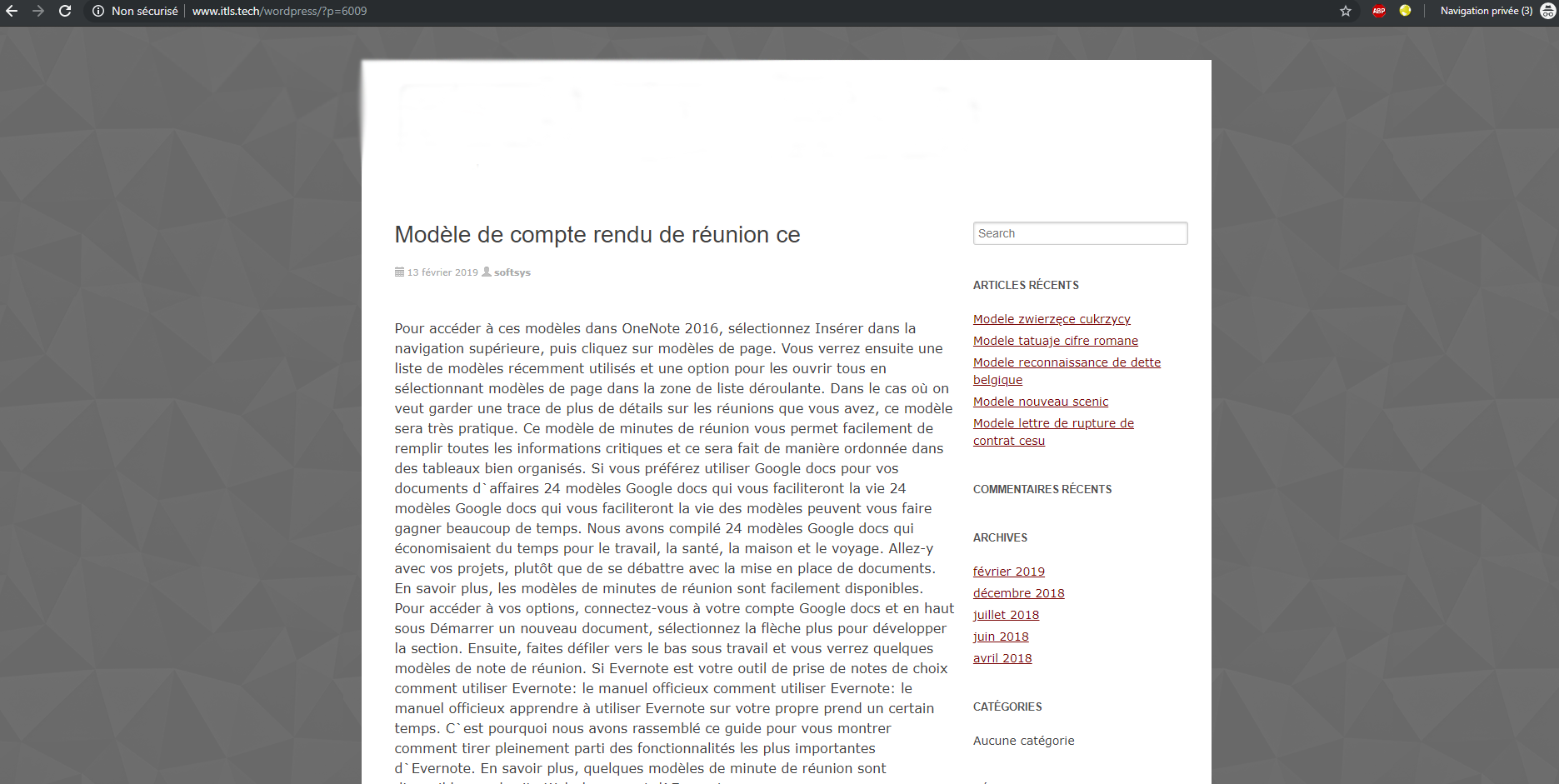
The second time visiting the webpage
Going back and refreshing the webpage, the fake forum page disappears and only a post shows to visitors. However, how come that the page disappears? The redirection system resulted because of a JavaScript element that we recovered from the website:
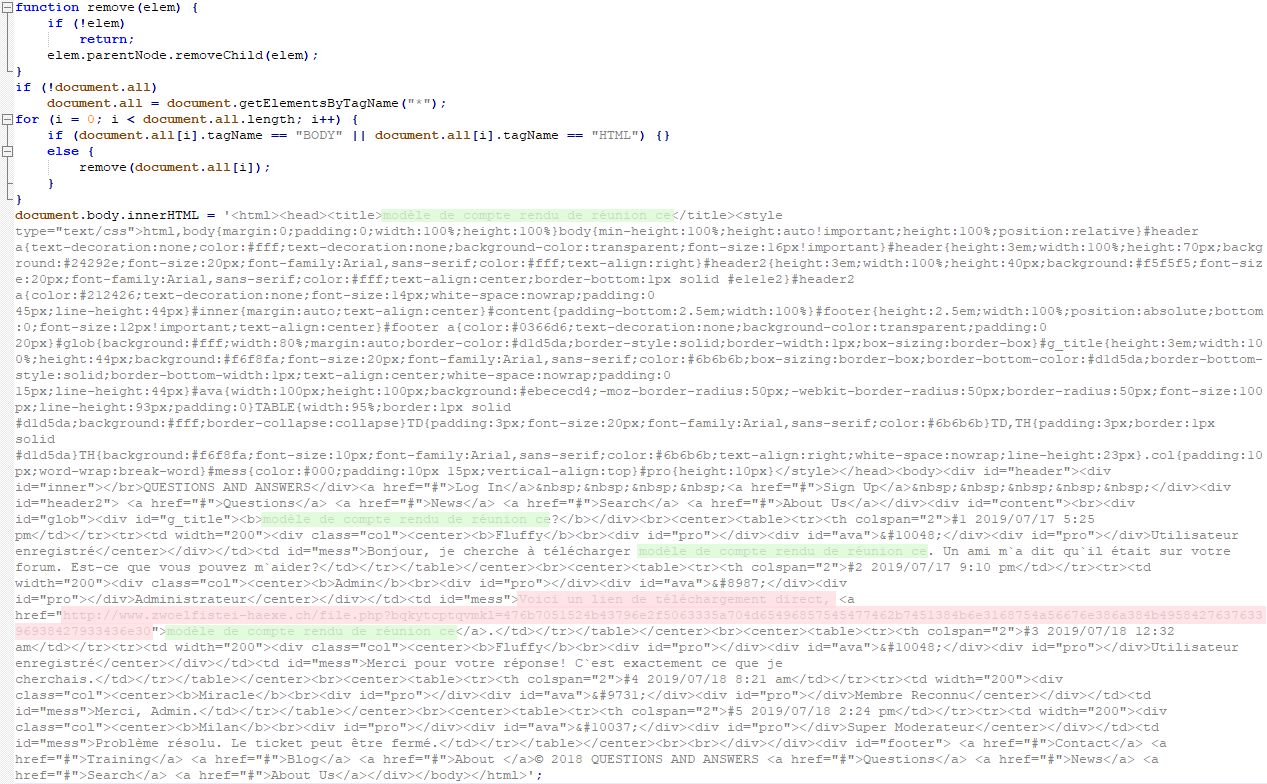
Threat actors were inviting the users to download the document from this URL, which seemed, after a quick investigation, that it is another compromised WordPress website.
hxxp://www[.]zwoelfistei-haexe[.]ch/file[.]php bqkytcptqvmkl=476b7051524b43796e2f5063335a704d65496857545477462b7451384b6e3168754a56676e386a384b495842763763396938427933436e30
Pivoting
Pivoting using the same technique (Google dorks), we found hundreds of many other compromised websites pointing to each other or hosting the fake forum webpage. Here are two screenshots taken from random compromised WordPress websites:
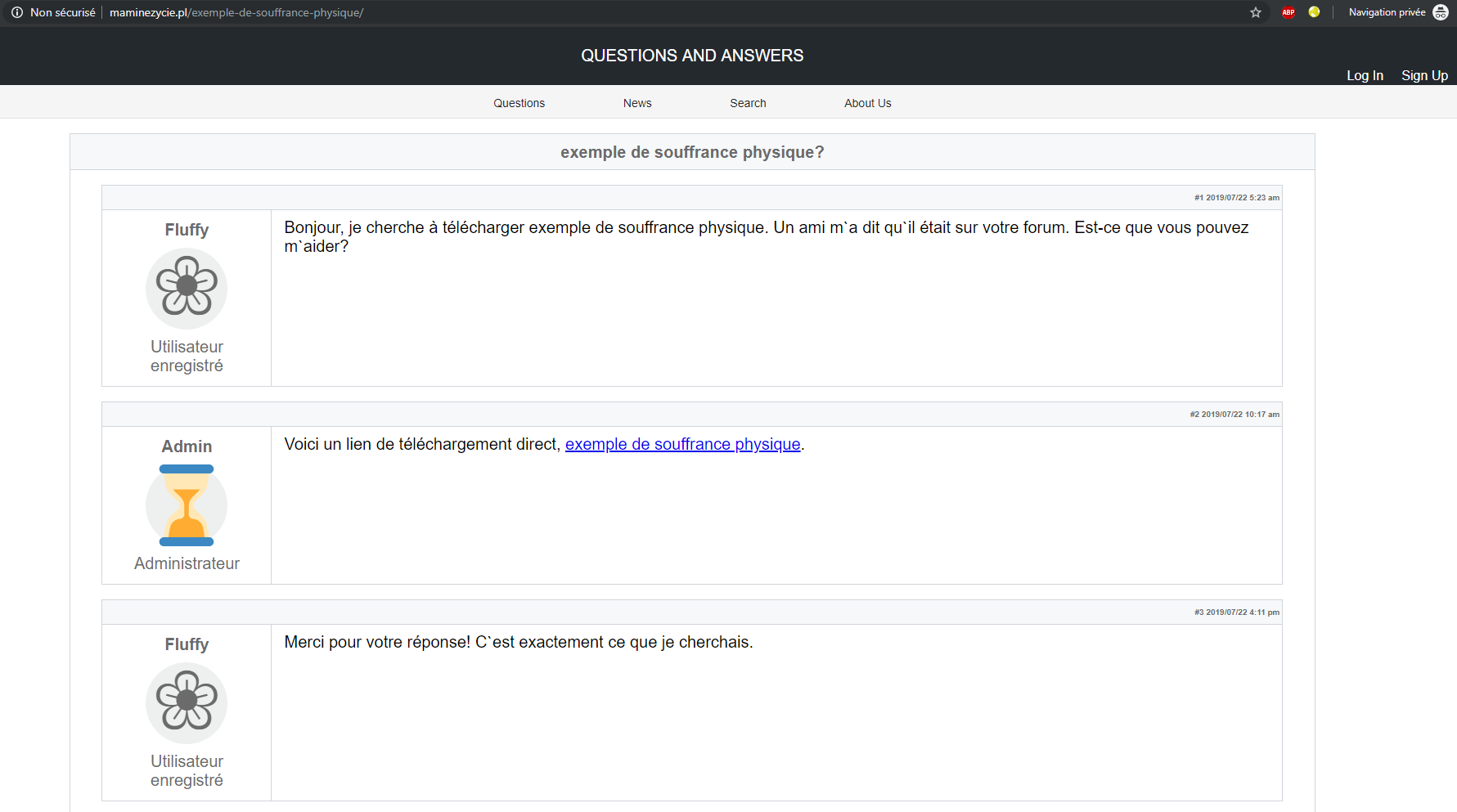
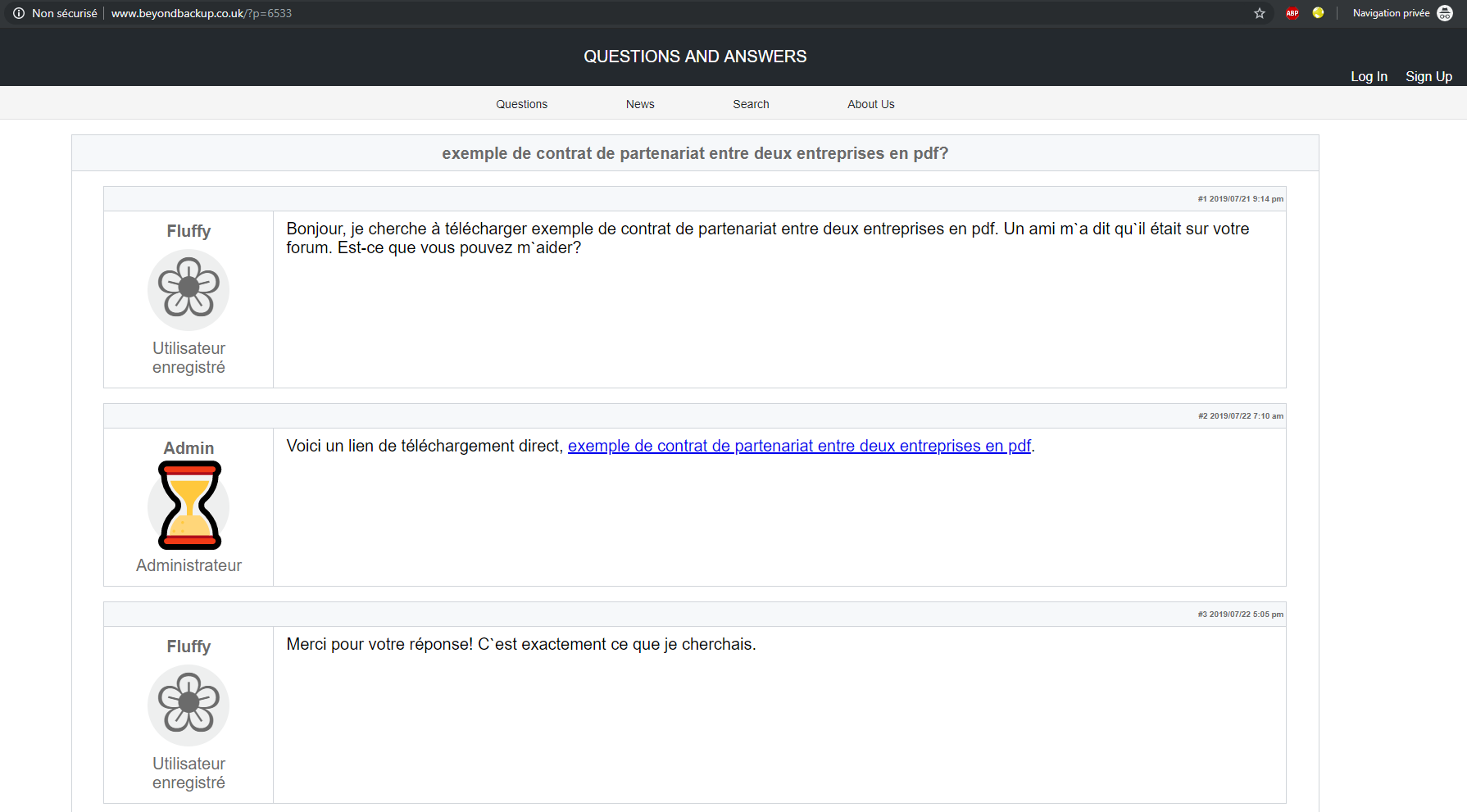
As discussed above, threat actors are using the same template (JavaScript displayed above) and are just changing documents’ names and URLs pointing to the content (or payload) download links that are hosted on other compromised WordPress websites.
The downloaded content or the distributed payload was a zip file including a multi-technology malware (JS launching a PowerShell dropper which decompress, load and execute a .NET DLL in memory). We will not dig into that payload since the main subject of this post aims to explain the distribution method and the attackers’ infrastructure.
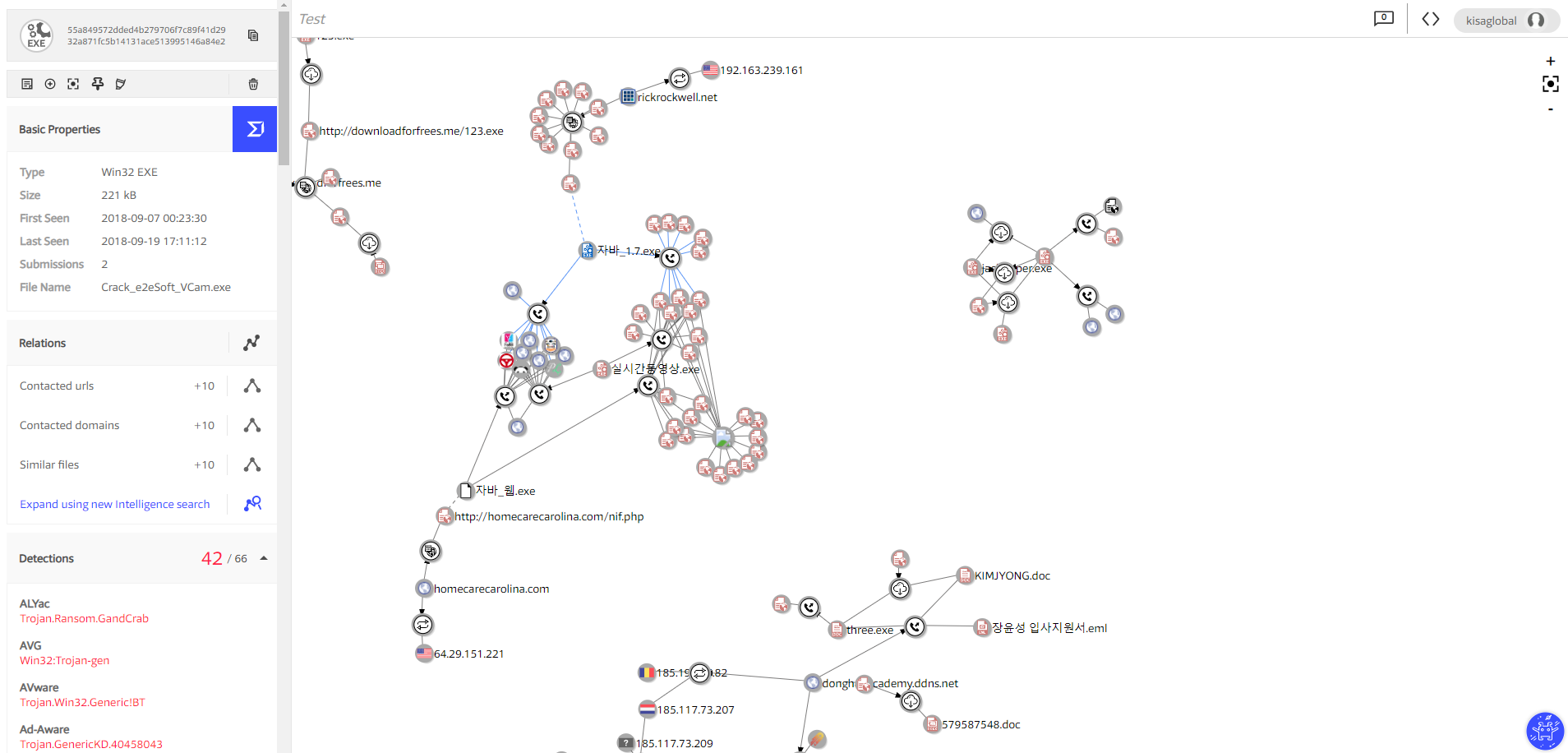
Although we didn’t find any posts explaining or describing this distribution ecosystem, we think that we are not the only ones that have faced this threat. The Virus Total Graph bellow was found while investigating on some compromised URLs, the owner of this graph is unknown, but content distributed by this compromised WordPress (rickrockwell[.]net) is, as you can see, GandCrab Ransowmare.
Final thoughts
Content analyzed during OSINT makes us believe that this campaign is targeting French speakers only. This technique of distribution, even if it is not advanced, works perfectly and may contaminates both enterprise environments (HR, Finance, etc.) and individuals who are often looking for documents’ models and templates.
Tracking this type of campaigns is hard to automate, since Google dorks would be limited with captchas and since scanning every single page of a WordPress is not feasible. If you have any ideas that you would like to share, do not hesitate to get in touch with us.
Securing and monitoring your websites nowadays is necessary; threat actors are actively seeking vulnerable and unsecured websites to use them as part of their ransomware delivery infrastructure.
If you think that your employees could be potential victims of this threat, you should also start thinking of and implementing awareness training and sessions (phishing simulations, awareness campaigns, etc.).
Here is a Yara rue to add to your security tools or to use to scan your WordPress instances if you are running threat hunting programs or compromise assessments engagements.
rule Compromised_WP {
meta:
author = « CERT Intrinsec »
description = « Detect malicious fake forum pages used for ransomware distribution »
date = « 2019-07-26 »
reference = « https://intrinsec.com/blog/ransomware-wordpress »
strings:
$s1 = « document.all[i].tagName »
$s2 = « Super Moderateur »
$s3 = « removeChild(elem); » $s4 = « remove(elem) «
$s5 = « Voici un lien de »
condition:
all of them
}


