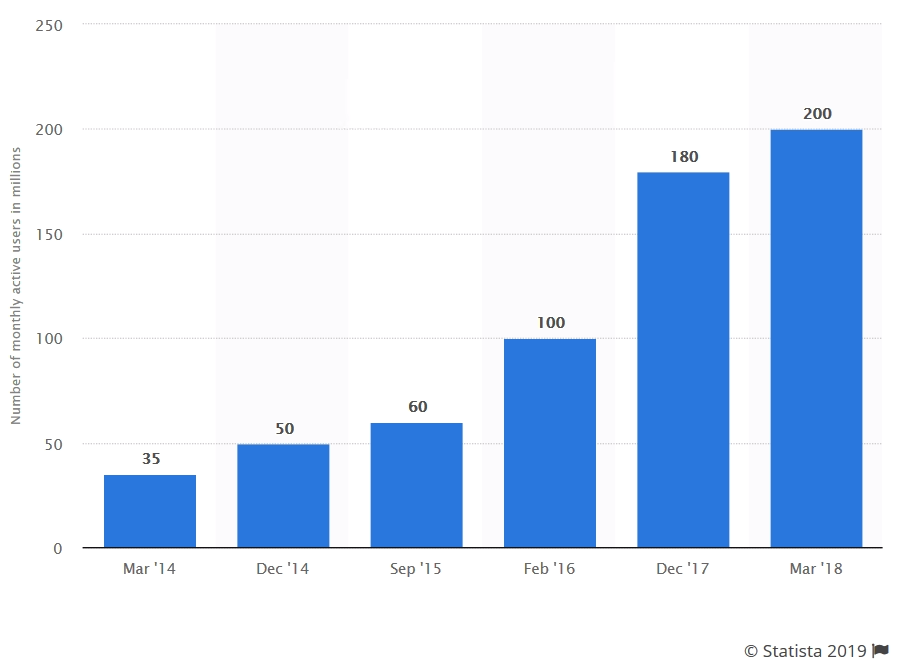
Telegram was founded in 2013 by two Russian brothers, Nikolai and Pavel Dourov, who also founded the social network Vkontakte. Their goal? Provide a secure messaging application that allows users to exchange messages, photos, videos, URLs and other files in complete confidentiality via an encryption system called MTProto. Although there is some criticism of Telegram’s encryption system, the social network has continued to gain visibility and users since its inception to reach, about 200 million regular users (or about 15 billion messages sent every day by the end of 2018). However, this network remains far behind Facebook, which tots 2.2 billion users up, or WhatsApp, with its 1.5 billion users.
The fact that it is free of charge and the promise of end-to-end encryption are part of the reason why users are so keen on Telegram. Indeed, the application offers a secret chat using encryption. These messages are recorded on the device used (smartphone for example) instead of being recorded on the Cloud. The user can thus choose to delete messages, and prevent them from being stored on the server. On the other hand, Telegram seems to be one of the most secure networks in terms of anonymity. A study [1] conducted by the New York-based media Outline gathered the opinions of 13 administrators and/or channel owners which offer illegal content. Most of them agree on one point: Telegram offers a wide variety of options to keep users’ identities private. This is one reason why channel creators and managers distribute their pirated content via this application. Indeed, since 2015, Telegram has been using a “bot” platform for developers. Thanks to the API system, users can therefore manage how interactions take place and how they are protected on the network. In addition, unlike WhatsApp, the user’s telephone number, required at registration, does not appear within the channels.
These privacy options combined with contextual elements are at the root of Telegram’s fast growth. Take for example The events of October 2014 showed a good example when more than 1.5 million Korean users switch from Kakao Talk (Korean messaging application) to the Telegram application. President Park Geun-Hye had just announced that all citizens’ electronic communications would be placed under surveillance, making it possible to arrest any user who had expressed criticism or launched rumours against the regime. Another topical event that has put Telegram on the list of world-famous applications is the Brazilian government’s decision to ban WhatsApp in December 2015. Since then, the messaging service has been available again to citizens but would have been deserted by some of its local users. Indeed, suspicions remain as to the existence of campaigns to disseminate fake news [2] via WhatsApp accounts held by the government and its supporters. In order to strengthen its position as a favourite, Jair Bolsonaro’s campaign team reportedly financed the sending of hundreds of thousands of messages. Despite the closure of some accounts in response to the scandal, the social network WhatsApp has reportedly suffered a certain decline in popularity in Brazil, further strengthening Telegram’s popularity. The email application would have gained an additional 3 million users following the failure that affected WhatsApp and Facebook on March 13.
In addition, increased surveillance of the Tor network by the authorities (see the closure of two very popular black markets: Hansa Market and AlphaBay) promotes the migration of Internet user communities, malicious or not, to other networks more hidden from view. Inevitably, the privacy benefits conferred on the user on Telegram arouse curiosity and often censorship by authoritarian governments. Let’s take the example Russia [3], Iran and China.
In order to understand and analyze the organization of malicious activities of hackers operating from this platform, our Cyber Threat Intelligence team spent several months within Telegram. See the overview of the threats present within this network below :
Research method
Our immersion in the Telegram network began in the second half of 2018 and continued until the first quarter of 2019.
We have focused our research efforts on detecting international Telegram groups focused on fraud, piracy, carding (in its global definition, i.e. the online traffic of bank cards, bank accounts or any other information relating to personal data that is fraudulently obtained), and on sharing of stolen data and malicious tools. In short, we wanted to find out if the threats we detect every day for our customers were also present on Telegram, and in what form(s).
In total, more than 150 Telegram groups gathered around these themes were integrated by our team, in order to collect as much information as possible on the malicious activities carried out by some members of this social network. These groups were identified through OSINT-based research techniques:
Google dorks (some invitation links to channels are indexed by Google): to do this, you just have to take the root of Telegram’s invitation links: https://t.me/joinchat/[ID] and to launch Google requests that potentially detect several thousands of invitation links to Telegram groups:
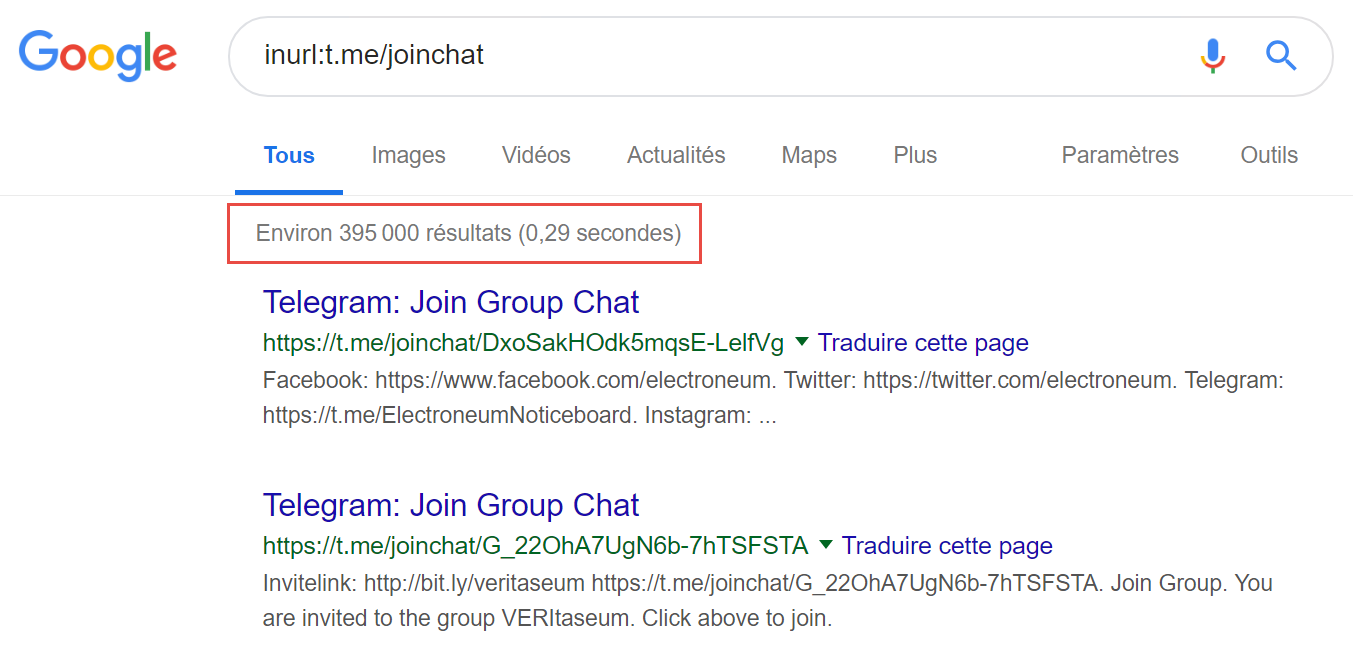
It is then sufficient to contextualize the research according to the target ecosystem to access the desired groups:
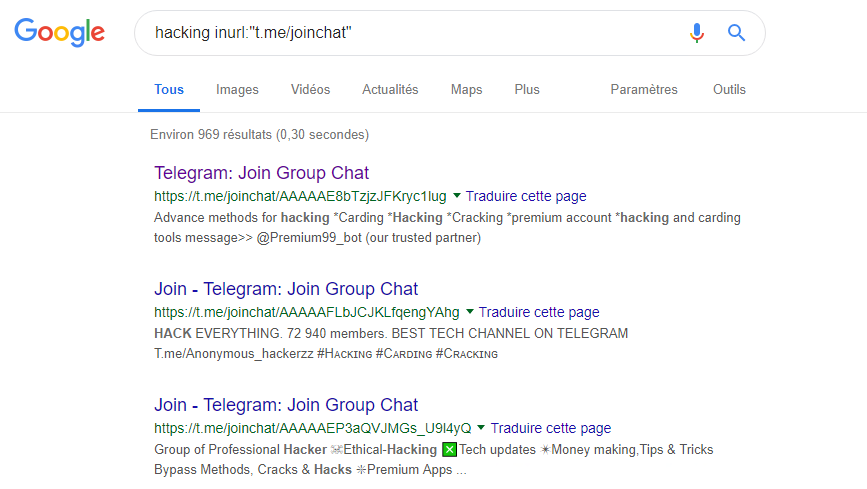
These requests served as a starting point for our sourcing and allowed us to access private or public channels. Other methods have completed our approach:
- Sharing Telegram groups on third party communities (Reddit, forums, pastebin etc.);
- Use of Telegram specific search engines (Telegago, a custom search engine, com etc.): http://cse.google.com/cse?cx=00636858593537057042503:efxu7xprihg#gsc.tab=0
- By pivoting within the integrated channels via the previous methods, following user announcements relaying the publications of other groups.
By doing so, we were able to reach communities with a total of more than 1.2 million English, Arabic and French-speaking users. We analyzed the conversations, data and files shared on the network to determine the type of information passing through it.
During our investigation, we found that the groups formed on Telegram could be very volatile and had a variable lifespan, ranging from a few days or weeks of existence for some, to several months or years for others. As users’ inventiveness leads to the instantaneous nature of the need, subscribers do not hesitate to leave one thread behind and follow another, which they consider more relevant. Besides to competition, the lifespan of Telegram groups can be explained by several concomitant factors: the level of channel activity that allows users to be gathered and retained over time (possibility of hosting up to 200,000 members in a single group), interdependence with other discussion groups: when a Telegram channel is referenced by other channels, this directly contributes to its visibility, credibility and influence. Let’s also mention the willingness of the administrators of a group to complicate the monitoring of their channel by the authorities, by regularly migrating to a new channel with a different name and address:

Within the very heart of this social network, we wanted to answer several questions: how do Internet users organize their malicious activities on this network, what content do they share and what impacts can this have on the users or companies targeted by these activities?
Telegram, an Eldorado for hackers looking for stolen data and new fraud techniques
From our immersion in these Telegram channels, it appears that the network is structured in the same way as the sections present on the malicious forums of the Surface or the Dark Web. There are groups specialized in sharing stolen data (databases, user data, bank data), others in sharing information and documentation on malicious activities (hacking tutorials, fraud techniques, social engineering, etc.). It is also possible to find malicious tools, such as malware for sale or free access on several channels.
User accounts and bank data at your fingertips
What is surprising, unlike some known malicious communities, is the fact that shared information is free and accessible. While some of the products offered are only available for a fee (Bitcoin, PCS, MasterCard, etc.), almost everything is made available to the community through loyalty schemes run by Telegram group administrators in the form of donations (“giveaways”). In addition, unlike other messaging services (Discord for example), there are very few restrictions on access to channels, which allows any user who detect a newsgroup to join it at will. Login credentials and other personal data of online service users are shared in a continuous flow over the various channels we have selected.
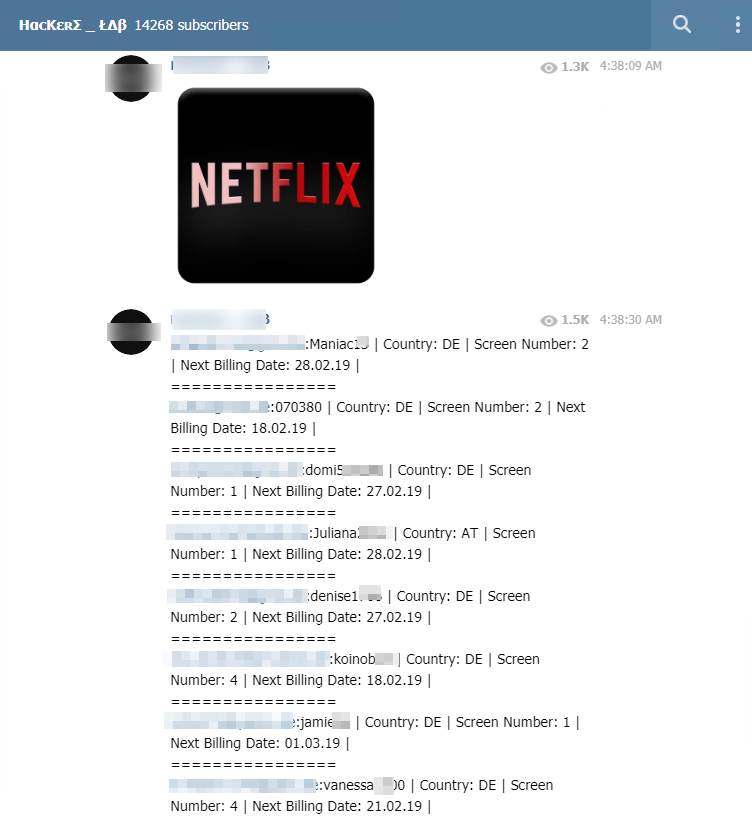
According to our observations, the services with the most popular user accounts are:
- Video on demand services (Netflix is particularly targeted by hackers, but there are also Origin, Hulu etc. accounts)
- Music streaming services (Spotify, Deezer, Apple Music etc.)
- Video games (Fortnite, Minecraft, Steam etc.)
- VPN Services (Express VPN, Nord VPN, Vyper VPN, Hide My Ass ! etc.)
- Services delivering pornographic content

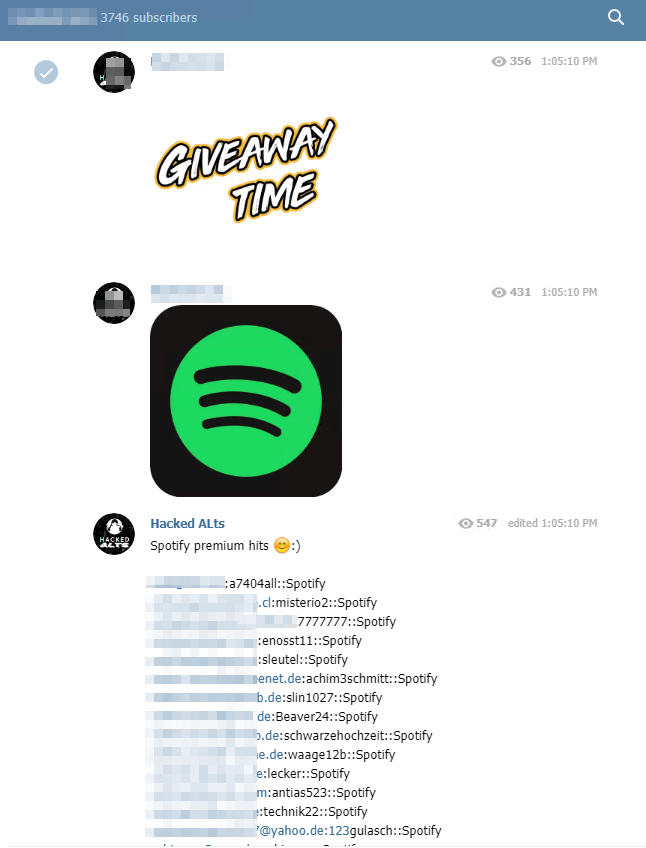
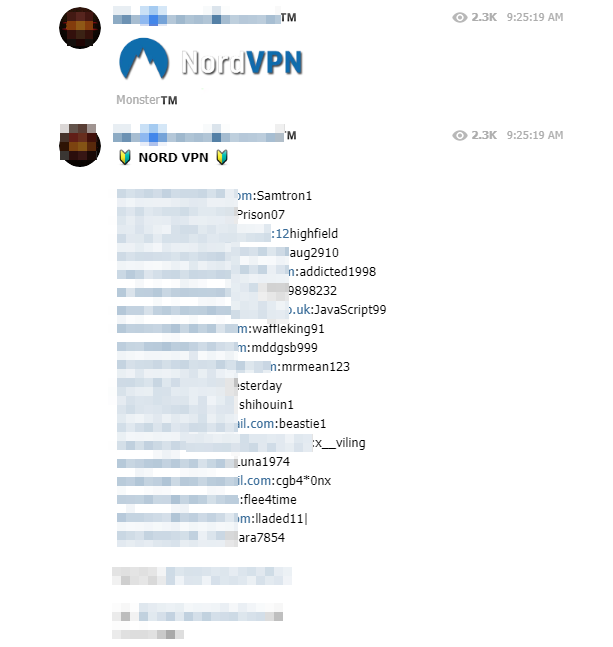
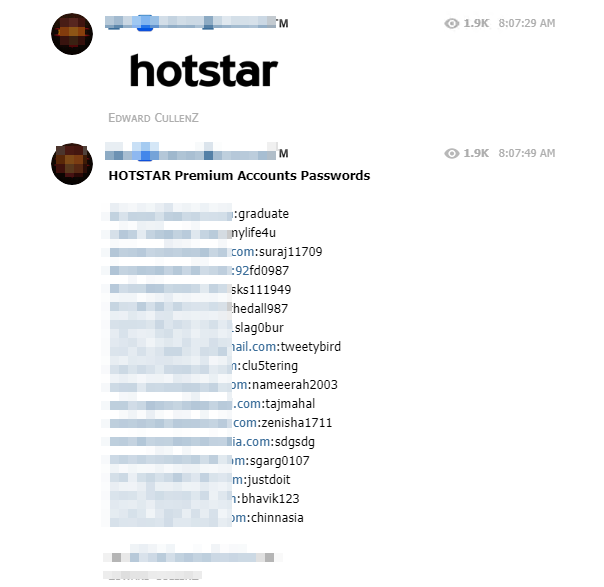
Credit card numbers and PayPal accounts of legitimate users are also published for the community. However, it is possible that these cards may be deliberately shared by experienced hackers with less experienced users, so that they can be used without caution and commit a mistake that would protect those who hacked and exploited them in the first place.
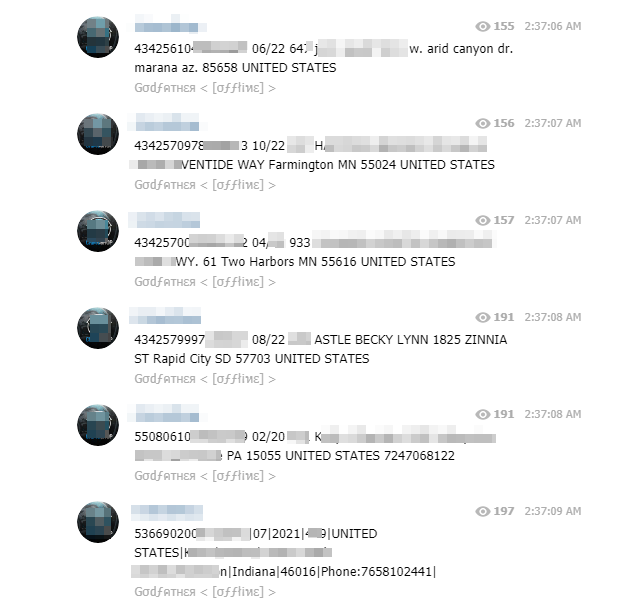
As proof of the phenomenon of hacker migration on this social network, some illegal credit card resale websites have chosen to open their Telegram channel in order to share their latest findings with their community:
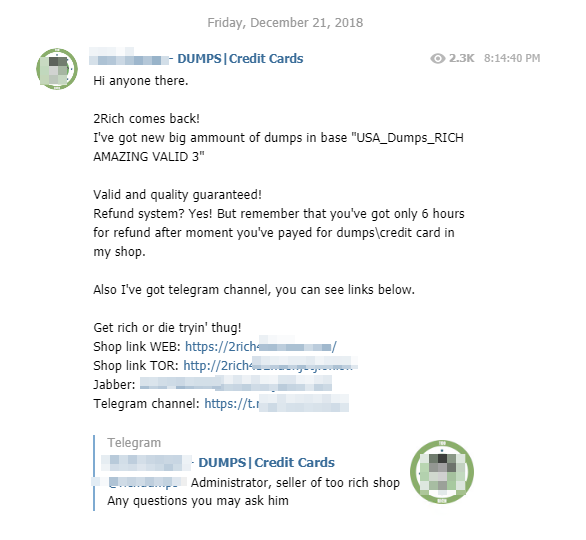
Knowledge for all, everywhere, all the time
Beyond the sharing of stolen data, the other characteristic feature of this network is the sharing of documentation free of charge to all members, in particular to inform them about the latest carding or piracy techniques. These tips take the form of tutorials and can pursue futile objectives – the creation of a bot to improve a video game character for example – or quite malicious: the knowledge of fraud or piracy techniques (see below). The multitude of “trainings” offered by users is impressive and documentation can sometimes reach several tens of gigabytes of content (each file must not exceed 1.5 gigabytes – the equivalent of a complete movie – and it is possible to share as many as you wish):

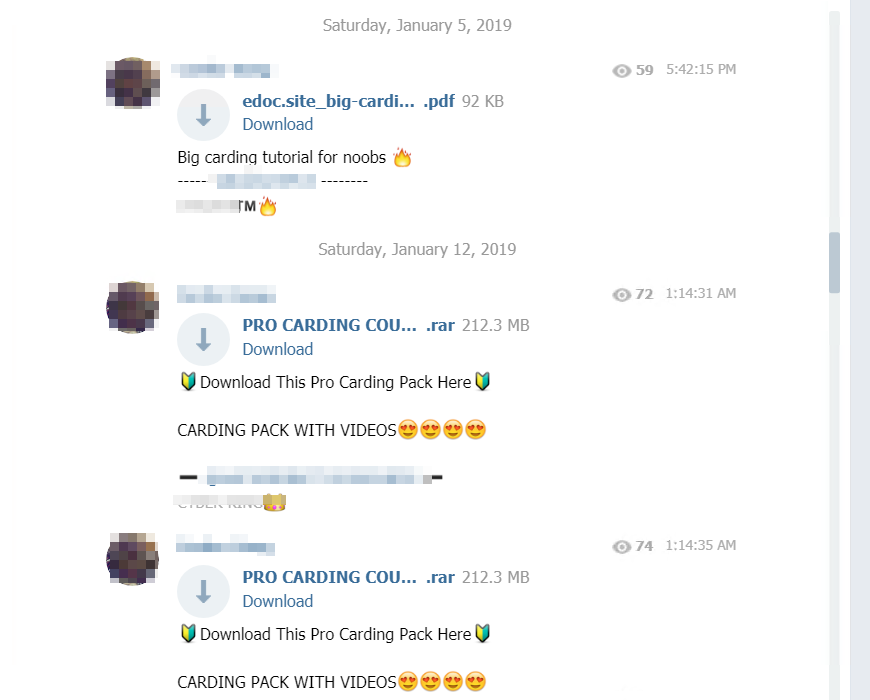
As part of our investigation, we were able to obtain copies of documentation highlighting malicious acts, such as these tutorial sharings which details to the users carding techniques applicable on popular websites (that of a shoe brand and Hi-Fi):
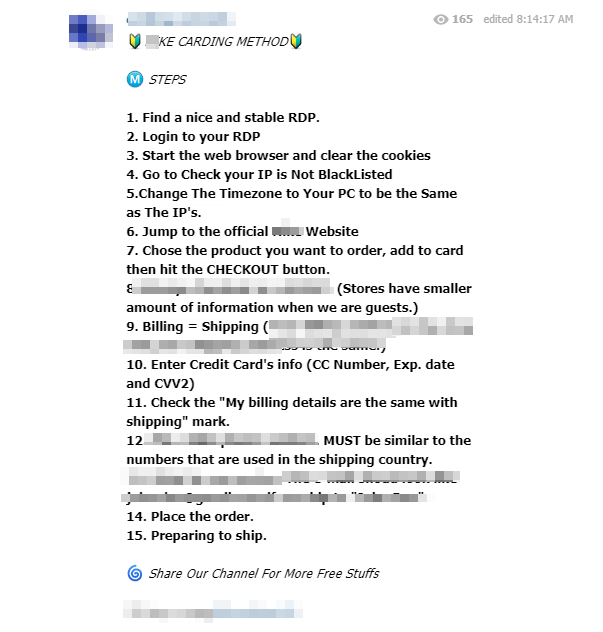
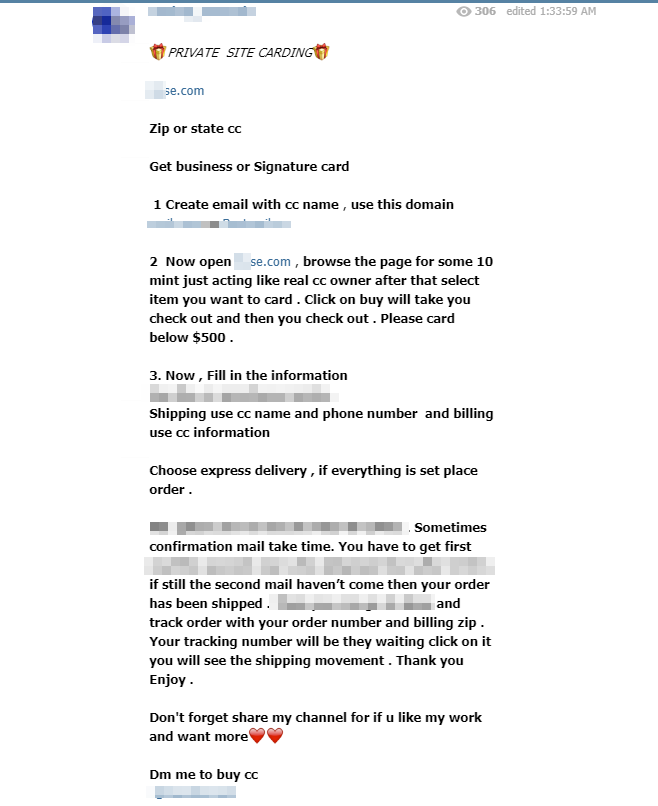
Members can freely obtain tips on fraud techniques and then move on to practice. Other groups have even chosen to focus exclusively on teaching Internet users about these techniques:
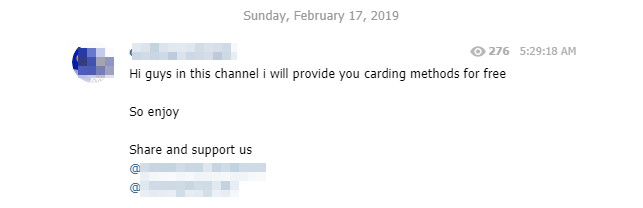
After the initiation, the improvement: sharing attack techniques, malicious tools or databases is common on Telegram
Even more worrying than the sharing of knowledge or stolen data, malicious tools and hacked databases circulate daily within Telegram groups. Some channels have indeed become real black market places for hackers looking for specific attack tools, either free of charge or for a few Bitcoins. Our immersion within the network allowed us to observe that the groups preferred tools dedicated to credentials stuffing, DDoS, bruteforce attacks on specific CMS (content management system) systems, or those facilitating attacks by ransomware, RAT or cryptomers:
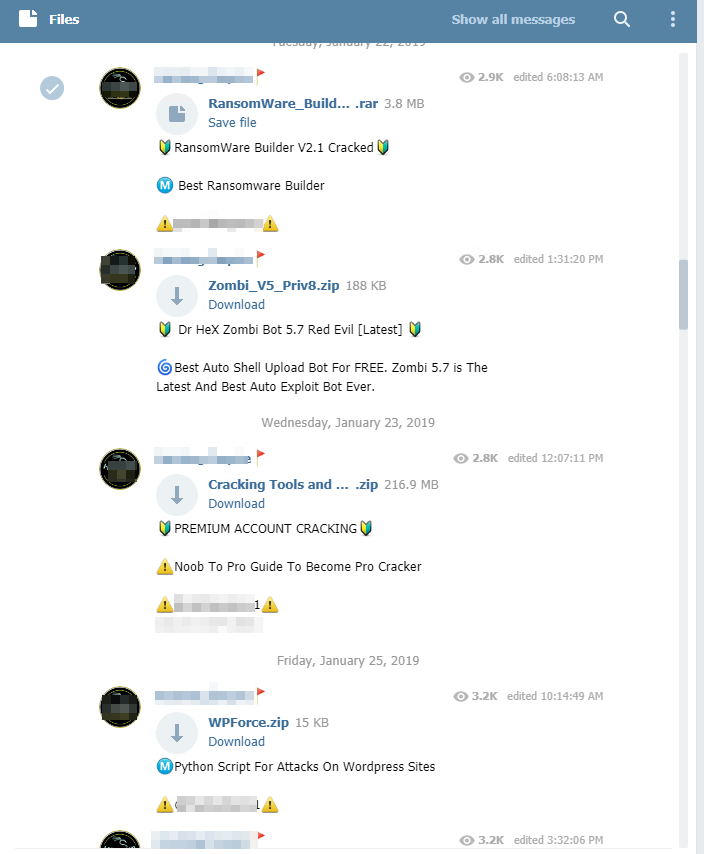
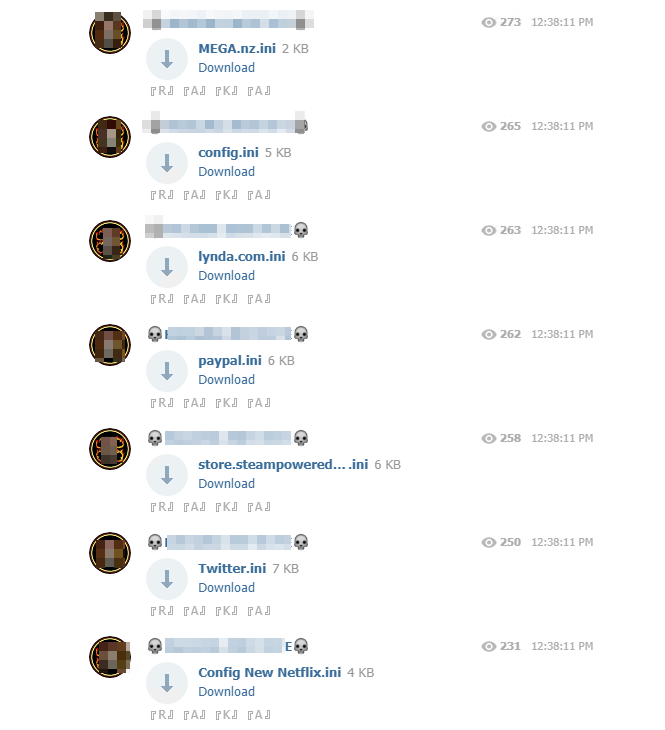
Particularly popular with attackers, configuration files working with stuffing credentials software such as Sentry MBA, STORM or SNIPR are numerous on Telegram. These tools allow hackers to massively test identifiers (username and password) recovered from databases stolen from specific sites until they obtain a valid account. Less experienced users are often looking for this type of file because their ex-nihilo development requires technical skills. The fact that these files can be found freely accessible on the network thus makes it possible to make this type of attack accessible to all users.
We were able to obtain several samples of configuration files targeting known sites and for which user accounts are particularly sought after:
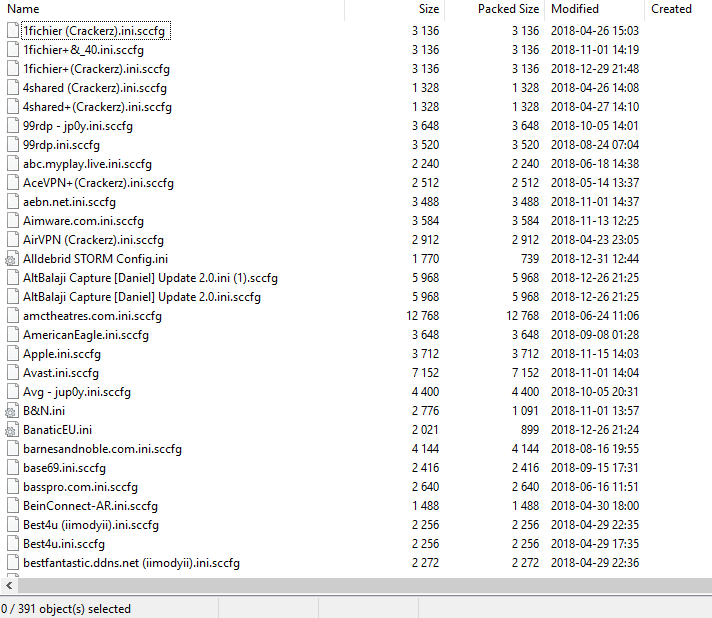
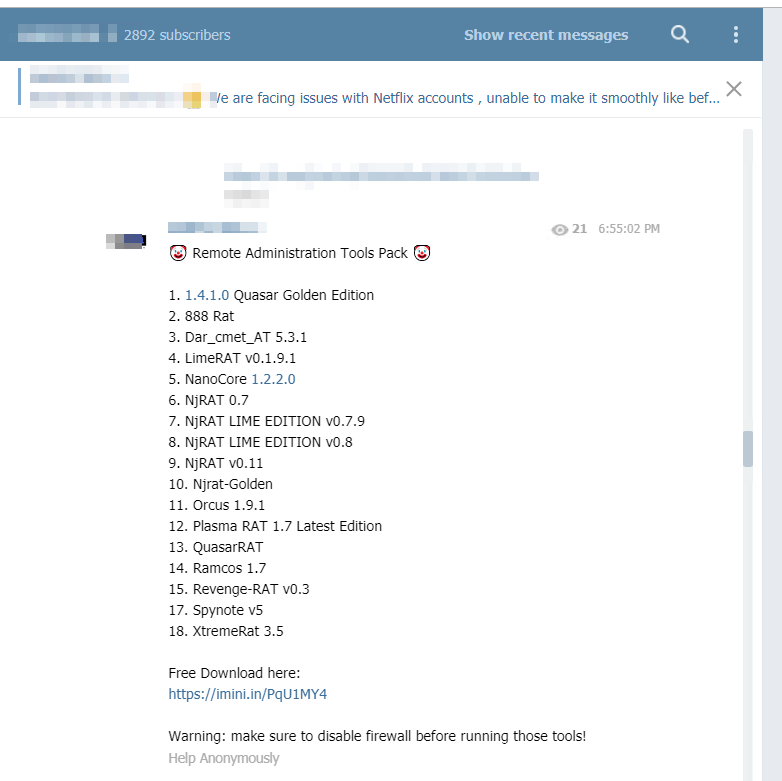
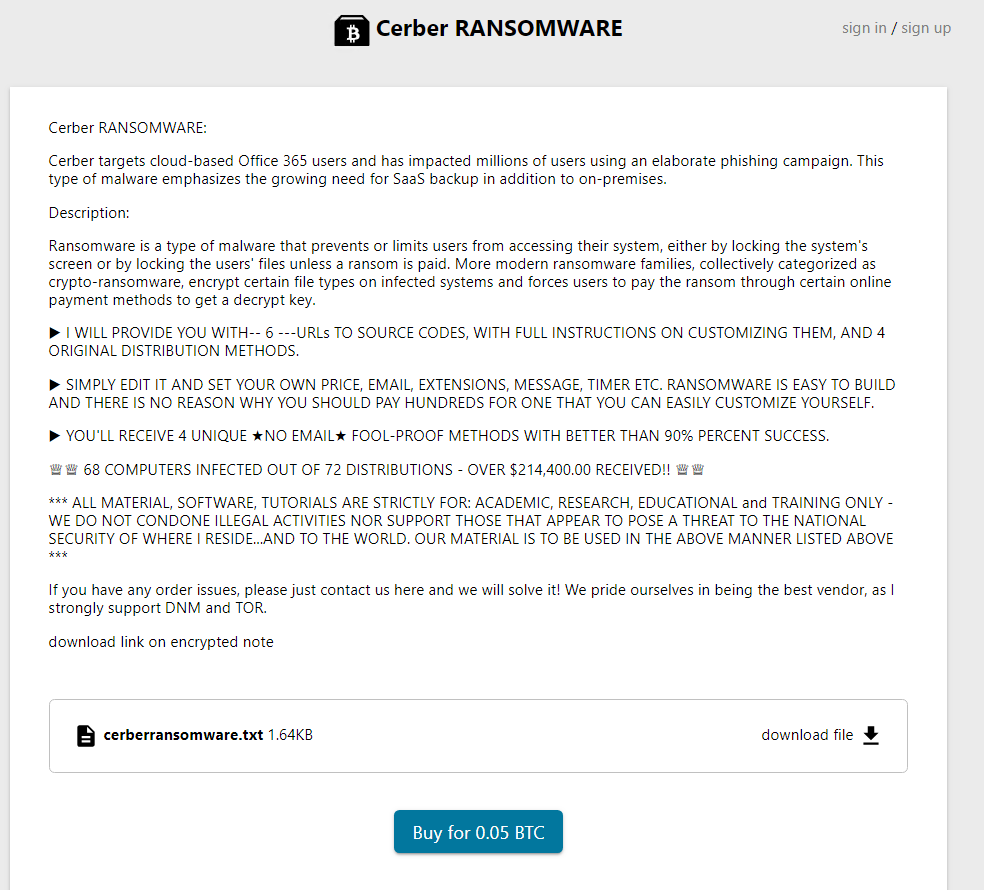
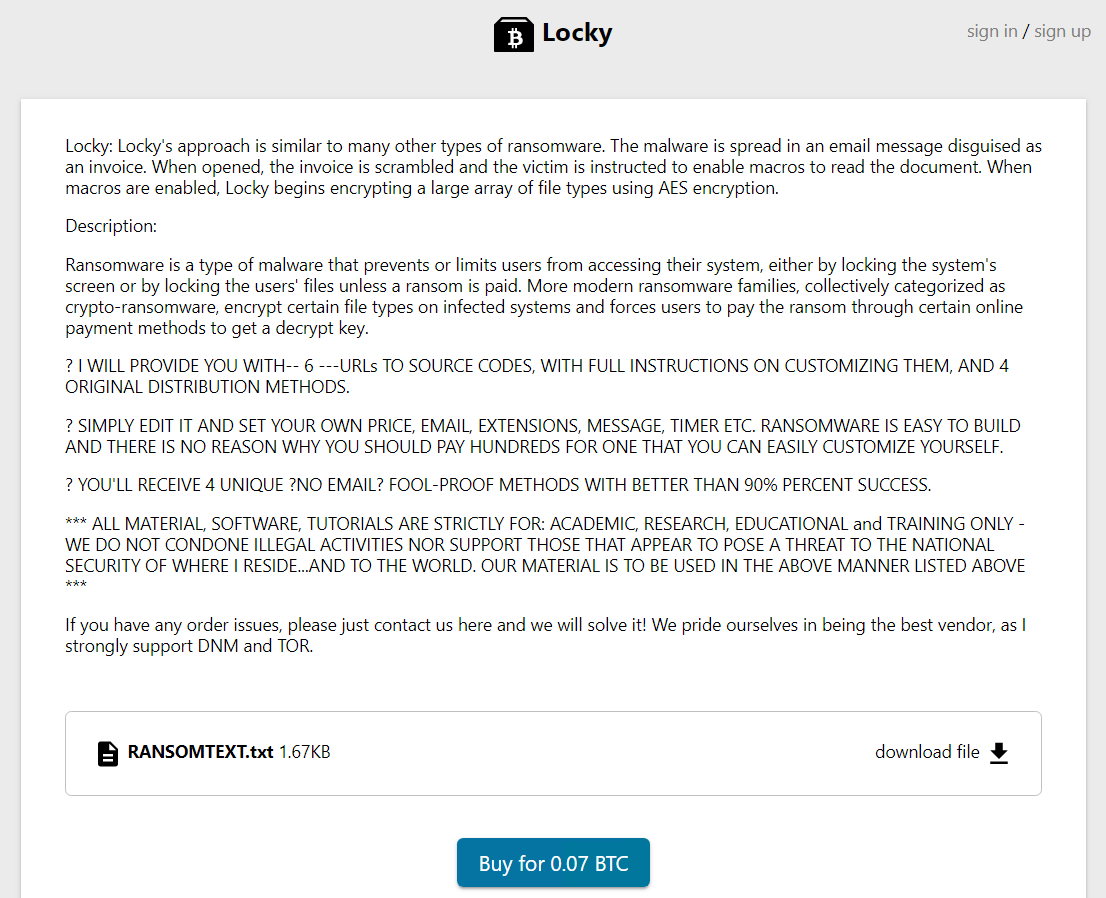
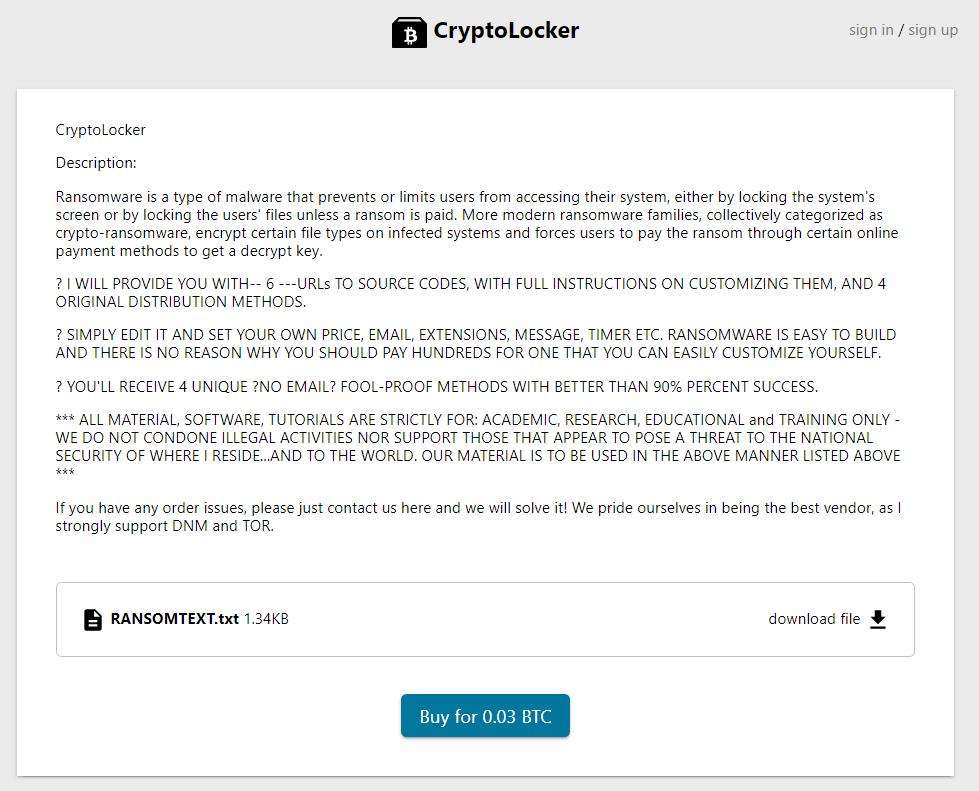
Cryptomers and ransomware are also highly sought after by attackers. Telegram is a pool in which it is easy for attackers to find what they are looking for, whether by downloading malware available free of charge or by financing actors who offer it for sale. It only takes a few researches to get cryptometers:
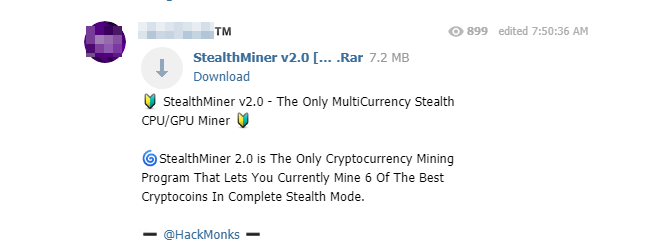
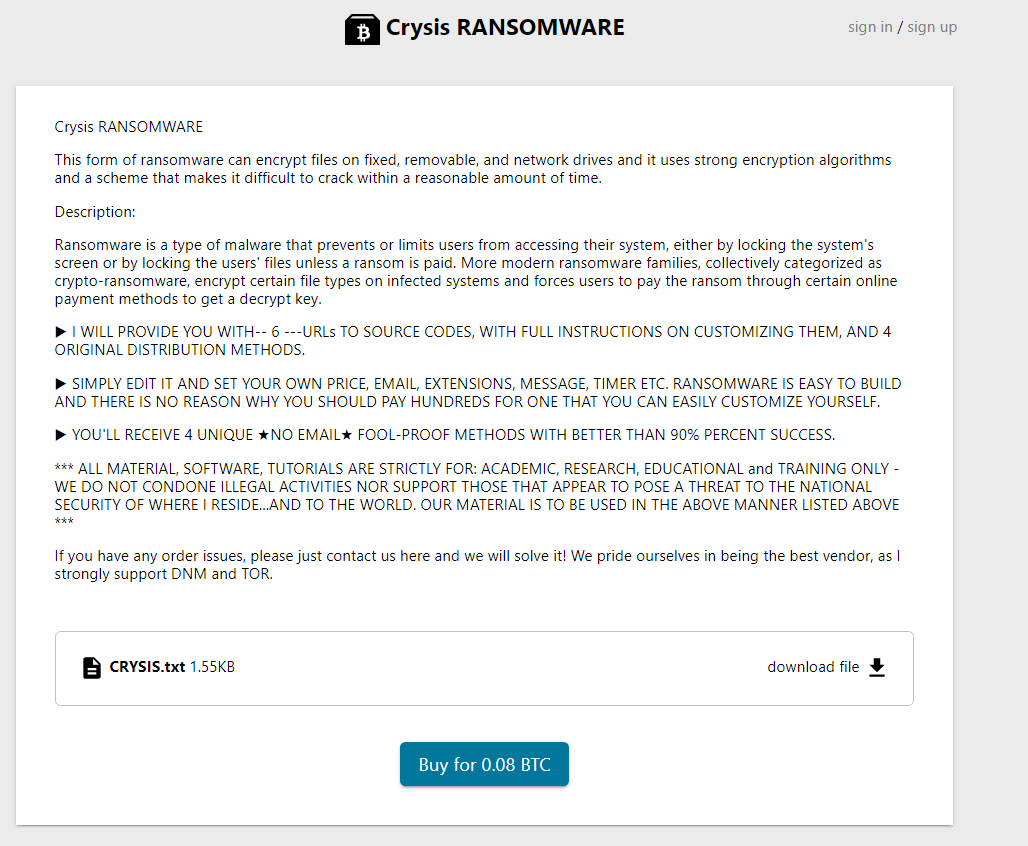
For example, another user offers four known ransomwares (Cerber, Crysis, Locky and Cryptolocker) for only a few Bitcoin (respectively 0.05 ; 0.08 ; 0.03 and 0.07 BTC). Discovered in September 2013, CryptoLocker (screenshot below) is a malware capable of encrypting the files present on the victim’s computer in order to demand a ransom in exchange for their decryption. For a commission of about 20%, some hackers even offer their customers to take care of the attack and pay them the profits. The other three malware also belong to the ransomware family, which underlines another feature of the Telegram network: the lucrative nature of attacks. From our observations, although the range of malicious options is extremely wide, it seems that the content of the channels is used primarily by individuals and serves their money needs.
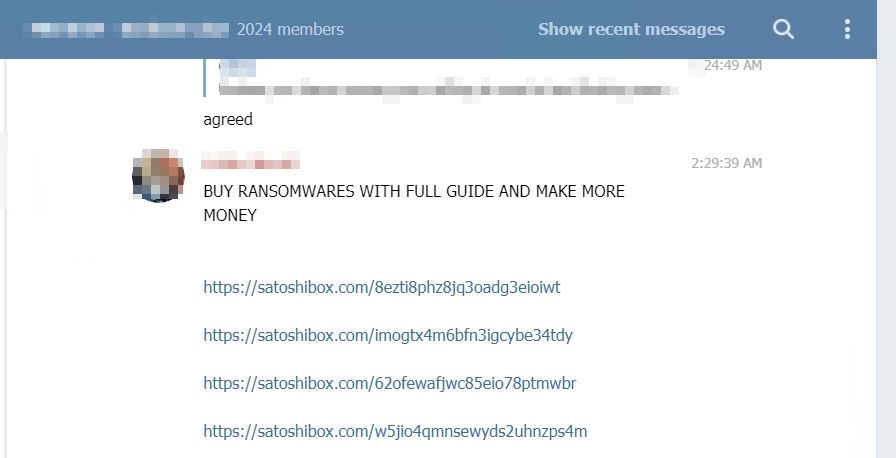
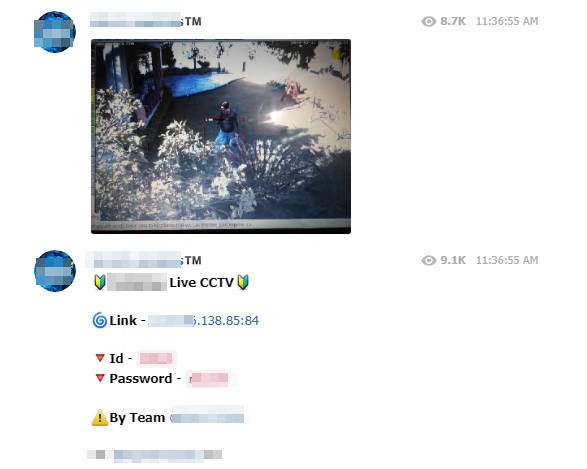
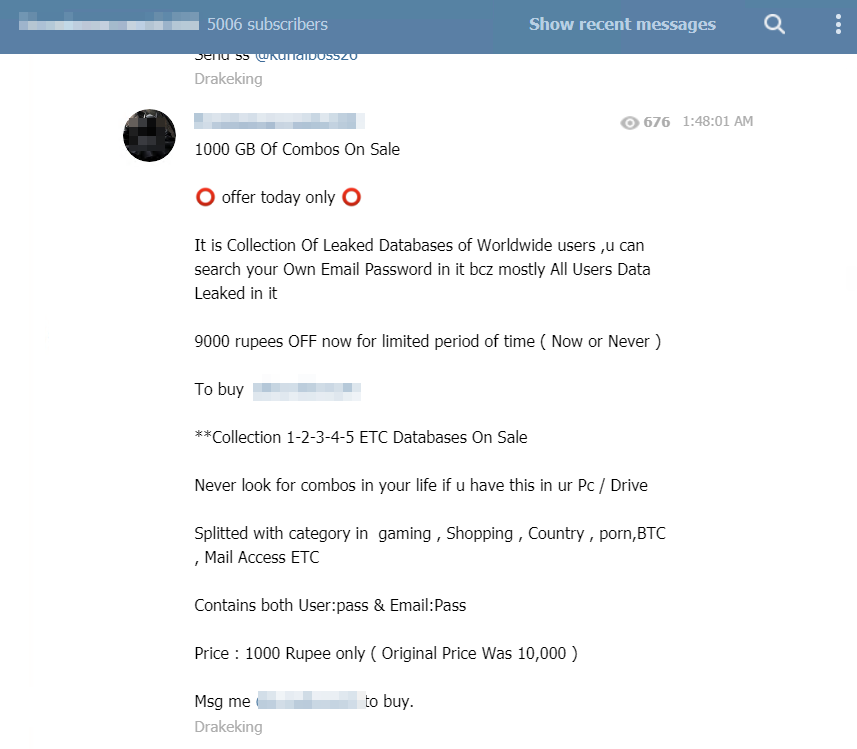
Finally, other users share the results of their own piracy – or those they find interesting – in order to share their discoveries with the community. Among the few examples that punctuated our immersion: , a stock of nearly 1TB of leaked data available for sale for about a hundred euros (including the recent databases “Collection 1# to 5#”):
Conclusion
The observations we made allowed us to deduce the following observation: the Telegram application is a threat vector because of its ability to offer a summary of all fraud schemes and piracy techniques available on the Web. The volume of information available coupled with the accessibility of this network inevitably promotes the spread of risk: a telephone number, Internet access, some basic research and it becomes possible for anyone to access several malicious conversation groups. These changes in the parameters of access to harmful information considerably reinforce the challenge facing companies.
On the one hand, companies face increasing threat vectors: as we mentioned in the introduction, the weakening of forums hosted on the Tor network (until recently [4]) leads to a displacement of malicious actors on networks like Telegram but not only; WhatsApp and Discord are also invested by attackers. On the other hand, they face new expectations, both in economic terms (if a paid service is systematically bypassed by malicious users, its sustainability could be compromised) and in terms of image (how to maintain the trust of its customers if user data circulates freely?). The need to preserve the integrity of their systems, including those containing customer data, is therefore essential. Compliance and ethics objectives also reinforce the need to put in place a strategy to detect and respond to these threats.
However, the task can be complex because Telegram is a means of communication that requires rigorous monitoring due to the immediacy of exchanges, channel volatility and exponential growth in content. One of the possible means of action to overcome this problem is to carry out a dedicated recurrent monitoring. Through its team of watchmen/linguists and on the condition of an adapted sourcing phase, Intrinsec is able to set up this type of specific monitoring, in order to regularly observe the evolutions of the various networks and to identify, in a short time, the latest fraud schemes or shared piracy techniques that are likely to represent a risk for an entity. These detections then allow the companies concerned to launch investigation procedures that we supervise in order to apply appropriate countermeasures eventually Thus, if illegal content is detected, it is then possible to submit takedown requests [5] to Telegram to request the closure of a channel. Other moderation tools are reportedly being developed, but Telegram still seems to be a poorly monitored network. According to a channel owner interviewed by Outline media [6], there would be very few Telegram group closures. One of the creators, Pavel Durov, also presents Telegram as a network based on libertarianism, within which “we cannot have more freedom”.
[1] SINGH Manish. In The Outline, « Telegram is the hot new source for pirated content », 21/04/2018 https://theoutline.com/post/4143/telegram-is-the-hot-new-source-for-illegal-downloads?zd=1&zi=2okrhvvs.
[2] CARDONA François. “Brésil: quand des soutiens de Bolsonaro utilisent WhatsApp pour des «fake-news»”, 25/10/2018, http://www.rfi.fr/ameriques/20181025-bresil-soutiens-bolsonaro-whatsapp-fake-news.
[3] KISELYOVA Maria, STUBBS Jack. “Russia starts blocking Telegram messenger”, 16/04/2018, https://www.reuters.com/article/us-russia-telegram-blocking/russia-starts-blocking-telegram-messenger-idUSKBN1HN13J.
[4] EUROPOL. “Global law enforcement action against vendors and buyers on the Dark Web”, 26/03/2019, https://www.europol.europa.eu/newsroom/news/global-law-enforcement-action-against-vendors-and-buyers-dark-web
[5] « Wait! 0_o Do you process take-down requests from third parties? ». In Telegram Faq. https://telegram.org/faq#q-there-39s-illegal-content-on-telegram-how-do-i-take-it-down
[6] SINGH Manish. In The Outline, « Telegram is the hot new source for pirated content », 21/04/2018 https://theoutline.com/post/4143/telegram-is-the-hot-new-source-for-illegal-downloads?zd=1&zi=2okrhvvs.



As the admin of this web site is working, no uncertainty very soon it will be
famous, due to its quality contents.