Red Team
Push the boundaries of penetration testing with Red Team:
Evaluate your company’s level of security and the effectiveness of your cybersecurity strategy!
The aim of our Red Team service is to simulate the real impact of a cyber attack by recovering trophies defined by you (sensitive corporate assets, personal data, damage to image, etc.).
How do we proceed ?
- Testing your detection skills (Blue Team)
- By simulating the real impact of a cyber attack
- Evaluating incident response processes
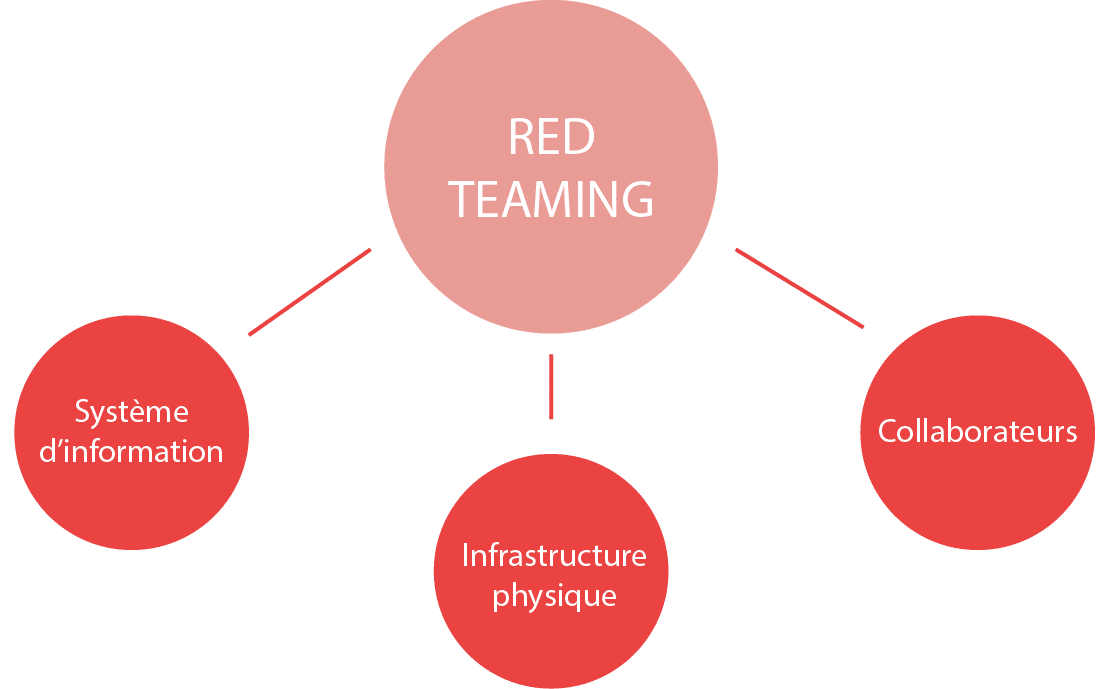
The objectives
⇒ Evaluate your company’s overall safety:
Information systems
applications, servers, networks…
Physics
Offices, premises, data centers…
Employees
: employees, service providers…
⇒ Evaluate your Blue Team’s detection capability.
⇒ Assess your responsiveness and ability to respond to incidents.
External recognition and intrusion attempts:
- Targeted phishing
- Physical intrusion
- External application compromise
Assume Breach mode
Purple Team’s complementary approach
Our complementary services
Full-time support
– Our security experts can provide full-time support for your Red Teaming projects
– A flexible approach to skills development, thanks to an experienced consultant.
Threat Intelligence
– Our Cyber Threat Intelligence unit enhances the Red Team’s actions by providing key intelligence throughout the mission:
– Compromised accounts
– Data leakage
– Sensitive services temporarily exposed…
SOC and CERT
Our strengths
Our Team
A team dedicated to the Red Team.
Our consultants
Certified and specialized consultants (offensive and defensive areas).
Fusion Center
Our various departments constantly feed and improve our Red Team.
Our approach
A unique intelligence-led Red Team approach.
Our feedback
Sensitive data: Social engineering
Discover potential targets on social networks
Product recipes: Intrusion Logic
Identifying a vulnerable web application
Production chain: Physical intrusion
Retrieving and cloning a visitor badge
The Red Team works for mature companies who want to challenge their defense teams. The strength of our approach lies in the complementary nature of our different divisions. Training exercises (Purple Teaming) are carried out internally between our defense teams (SOC, CERT) and Red Team. Each team benefits from the attack, defense and support expertise of the different teams, to constantly improve detection patterns and the effectiveness of intrusion and evasion techniques.
I want more information!
Leave us a message describing your security needs, or contact us if you’d like information about our activities.
Don’t forget to enter your e-mail address or telephone number so that we can contact you as soon as possible.

