BitLocker bypass: a simpler alternative to TPM sniffing
It is often mistakenly believed that Bitlocker encryption by default (without a password at startup) is a sufficient barrier against an attacker with physical access.
The most well-known exploitation remained "TPM sniffing", often perceived as too complex or unreasonable in real-life situations.
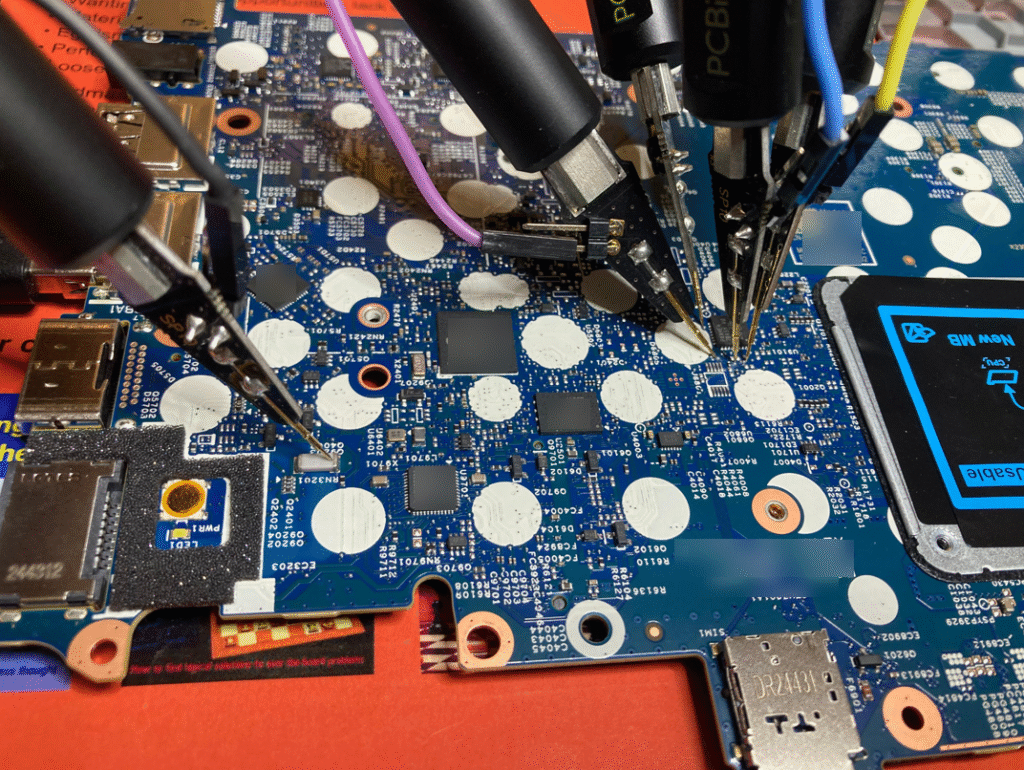
This is a technique we have already tested several times for our clients; however, it can take up to several hours depending on the motherboard model and configuration. It also poses a risk to the integrity of the audited hardware – it involves physically probing the TPM chip using a logic analyzer to retrieve the disk encryption key transmitted in clear text during system startup.
A more accessible, recent approach
In January 2025, a researcher published a brilliant article detailing a new mining technique (https://neodyme.io/en/blog/bitlocker_screwed_without_a_screwdriverThis alternative method does not require the same prerequisites and specific hardware knowledge as TPM bus sniffing, making the attack much more accessible and faster.
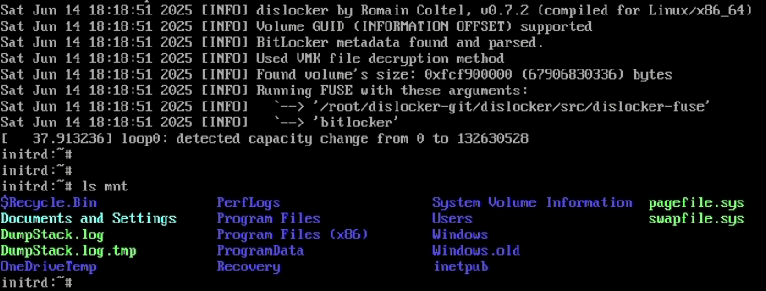
As early as February 2025, directly inspired by this work, one of our listeners developed a Proof of Concept to put this theory into practice.
He quickly had the opportunity to test and refine it during a client assignment whose goal was to compromise an encrypted Windows workstation and gain access to the network. The proof of concept allowed him to easily escalate his privileges on the otherwise up-to-date and hardened workstation and disable EDR, which subsequently facilitated network access.
How can we protect ourselves from it?
The most robust solution (and one that also protects against TPM sniffing) remains the activation of a Bitlocker PIN at startup.
The researcher's original article cites other hardening measures, legitimately considering them less effective or more restrictive, such as reverting to BitLocker's Legacy mode or applying a (fairly impactful) Microsoft patch. Based on our field experience, it's also possible to slow down the attacker to some extent by hardening the WinRE image to hinder BCD file retrieval, preventing booting via both PXE and USB, configuring Secure Boot to block third-party certificates, and protecting the BIOS/UEFI with a strong password.
It is important to note that no solution against these attacks can be perfect in terms of both security and user experience, like many other issues.
For awareness purposes, and for those who wish to study this technique, the auditor's PoC is available on GitHub: https://github.com/garatc/bitpixie







