CTI FEEDS
Are your detection systems powered by continuous, relevant, and tailored Cyber Threat Intelligence for your business context?

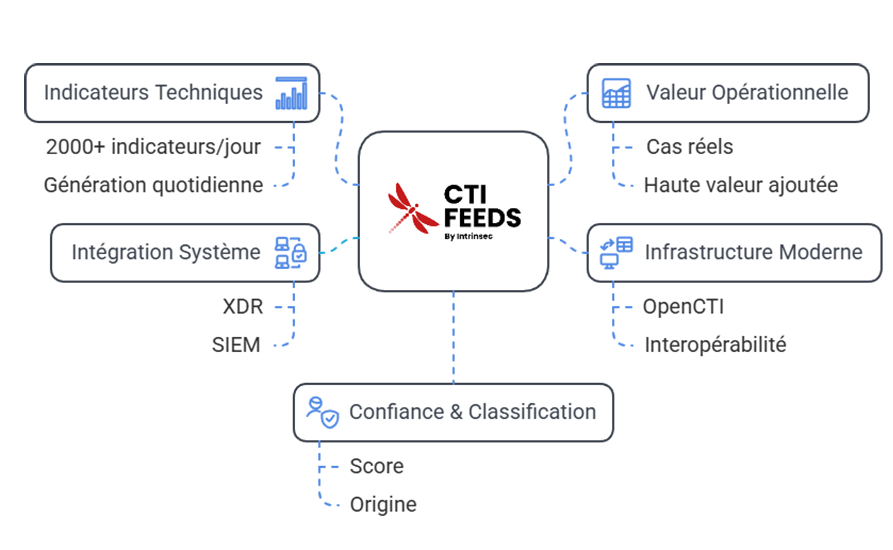
Contextualized Threat Intelligence feeds
THE CTI Feeds Intrinsec is a Cyber Threat Intelligence service that provides organizations with a continuous and up-to-date stream of indicators of compromise (IoCs), TTPs (Tactics, Techniques and Procedures) and contextual information on the threats most relevant to their industry.
Integrate enriched and contextualized technical intelligence into the heart of your cybersecurity system.
This service leverages consolidated data from CERT-Intrinsec activities (crisis management, threat hunting, malware reverse engineering, honeypots) and enriches it with the best international threat intelligence sources. Delivered in a standardized format (STIX2, TAXII, CSV, API), CTI Feeds integrates seamlessly with security solutions such as SIEM, SOAR, EDR, and XDR, enabling proactive detection, automated responses, and contextual risk prioritization.
Why rely on CTI Feeds?
Cyber threats are evolving rapidly: malware, targeted attacks, zero-day exploits. CTI Feeds allow you to anticipate and adjust your defenses and prioritize your actions, with the goal of improving threat detection and prevention while facilitating strategic decision-making.
Global visibility
- Impact on your business
Lack of context regarding emerging threats, sometimes resulting in reactions that are too late.
- How does the CTI help you?
Continuous access to open, private, or sector-specific sources enhanced with Intrinsec analysis


Improved responsiveness
- Impact on your business
Difficulty adapting your protections in real time in response to ongoing campaigns
- How does the CTI help you?
Contextualized alerts, up-to-date IOC/TTP data that can be injected into your tools (SIEM, NDR, EDR…)

Threat Prioritization
- Impact on your business
Risk of low-priority technical alerts for your business, information overload that is difficult to analyze.
- How does the CTI help you?
Prioritizing threat feeds to highlight the most relevant threats based on your key business challenges or critical assets. Support for integrating CTI into your vulnerability and incident management processes.


Guided decision
- Impact on your business
Little usable material in the security governance committees
- How does the CTI help you?
Decision-oriented summaries: trends, attacker groups, targeted sector threats.

Operational & strategic focus of CTI Feeds
Thanks to a rigorous review cycle, confidence scoring and systematic contextualization, Intrinsec's CTI Feeds accelerates incident detection, reduces false positives and aligns monitoring with business needs and the organization's actual attack surface.
The advantages of our CTI Feeds
Reliable, low-noise indicators
Our validation process reduces false positives: each IoC is qualified, tested and enhanced before dissemination.
European context and compliance
Our CTI Feeds are aligned with the requirements and sensitivities of the European context: GDPR, threats and local suppliers, relevant sector monitoring.
Editorial quality and rigor
Editorial production by our experienced analysts: avoids crude automation, adds context and real value to each alert.
Interoperable formats
Distribution in all essential market formats (STIX 2.1, TAXII, JSON, CSV, API, summary reports), for immediate integration into your SIEM, SOAR, EDR, management platforms.
Enrichment through real-life cases and publications
Indicators derived from field analyses, incidents dealt with, active campaigns, and recognized sector publications.
Intrinsec CTI FEEDS in your 360° Cybersecurity approach
Intrinsec CTI Feeds fit into your overall cybersecurity strategy
Managed service offering based on OpenCTI (Filigran), enhanced by our feeds (technical indicators, sector intelligence)
Why choose Intrinsec?
Contact our experts
Do you want to strengthen the security of your information system, ask a question or exchange information with an expert?
Intrinsec puts its expertise at the service of your cybersecurity.
Whether you are a company, a partner, or a public organization, Our team of experts is here to help you to address current cybersecurity challenges.
Send us your request using the form below.
Trusted partner:




