Cyboard
Central platform for collaboration between your teams and our services
Optimize your security management with a unified, actionable platform tailored to information systems protection.
Cyboard centralizes the governance of your information system to improve the security of your IT environments. The platform aggregates incidents, vulnerabilities, and IT system inventory to prioritize security measures. Through connectors, Cyboard integrates with your servers, cloud tools, and connected devices to map exposed assets. Dashboards assess the overall security level and quickly identify critical security vulnerabilities. Cyboard facilitates risk analysis by correlating operational events with business context to reduce IT risk. The platform helps the CIO formalize an IT security policy and clear operational procedures. Automated workflows enable the handling of security incidents and the orchestration of remediation actions. Cyboard enhances information system security through technical recommendations (hardening, segmentation, encryption). Vulnerability management features prioritize remediation to protect sensitive data and confidential information. The solution integrates authentication controls and indicators on the robustness of passwords and IAM policies. Cyboard strengthens digital security by recommending security solutions (EDR, SIEM, IAM) tailored to your IT system. Reporting modules facilitate audit evidence and ANSSI/CNIL compliance for your governance cycles. The platform provides cryptographic and encryption recommendations to secure data flows in transit and data at rest. Cyboard supports risk management by providing an impact matrix and KPIs to track security levels over time. Integration with the SOC improves cyberattack detection and accelerates response to security incidents. Our standardized playbooks transform analysis results into operational and controllable security measures. Cyboard enables the industrialization of system security and the automation of patch and fix tracking. The platform helps protect the security of exposed networks and services through segmentation and controlled exposure rules. The IT security audit modules support periodic checks and external audits requested by clients. Cyboard identifies exposure to cybercriminal actors and proposes remediation scenarios against malicious attacks. The solution consolidates information security and demonstrates compliance with security measures to decision-makers. Cyboard helps secure the entire system, from the workstation to cloud and microservices architectures. Dashboards highlight unsecured assets to reduce the attack surface for hackers and cybercriminals. Request a Cyboard demo to see how the platform transforms vulnerability management into an operational lever for cybersecurity.
Your major challenges
Centralize security management within a single platform.
Facilitating collaboration between operational teams (SOC/CTI, etc.)
Automate and optimize the management of your organization's security services.

Manage your security services from a single interface
CyBoard centralizes your detection and response operations to transform technical data into strategic decisions. Gain visibility, accelerate remediation, and optimize the performance of your protection.
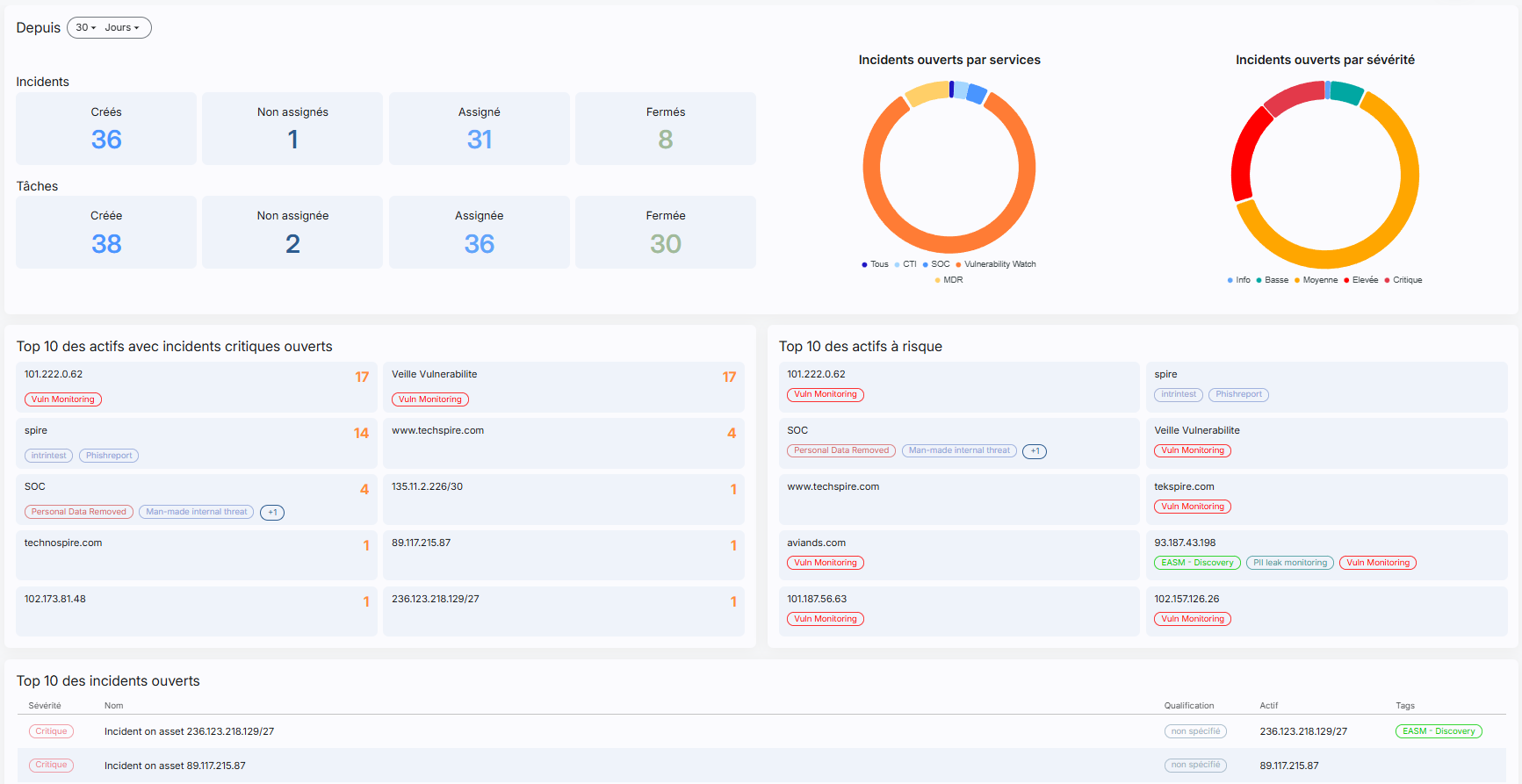
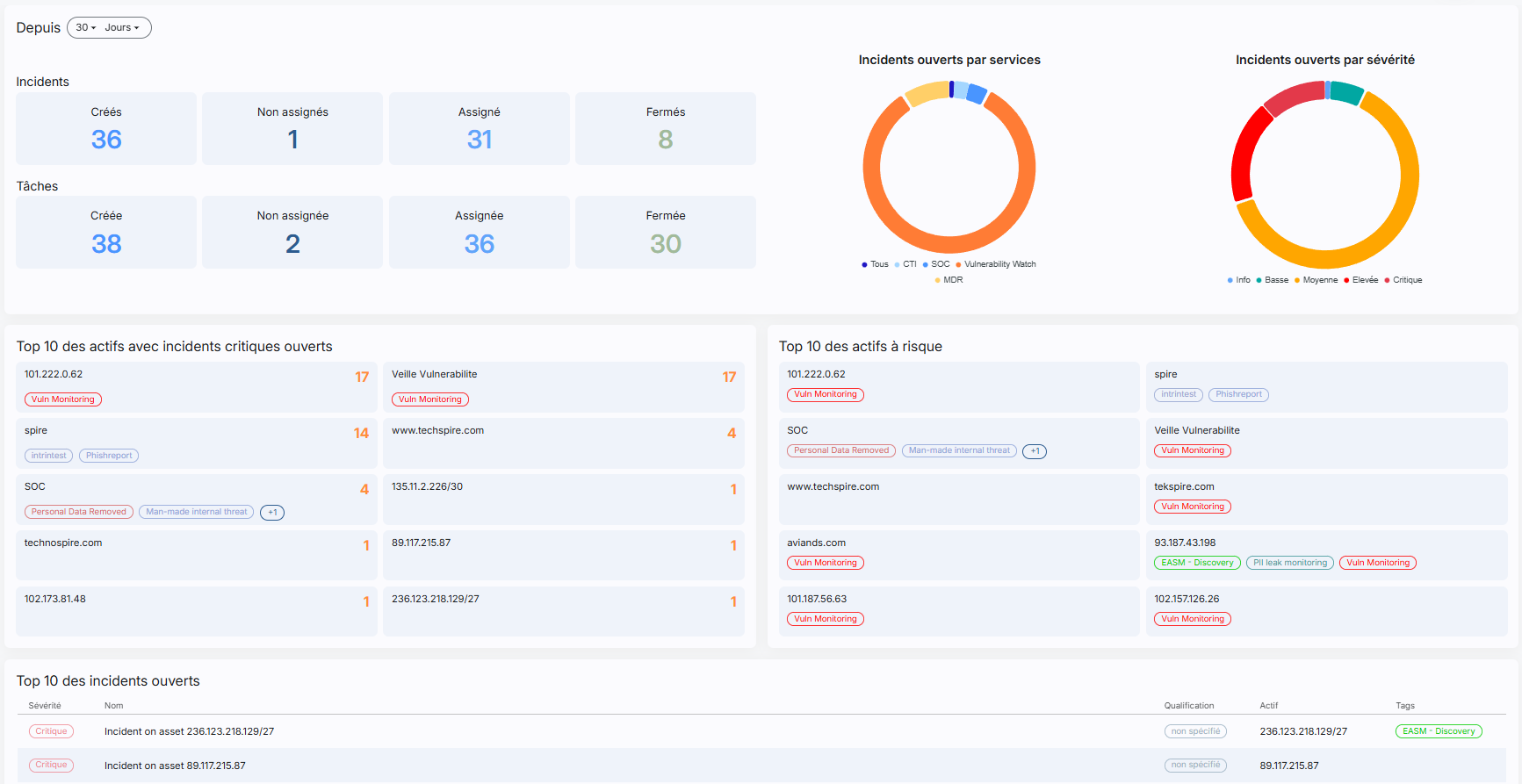
Immediate visibility, piloting mastered
The CyBoard dashboard unifies all your alerts, incidents, and monitoring activities into a single, actionable view. At a glance, you can:
- Follow your key performance indicators (KPIs) in real time.
- Identify the assets most exposed to critical threats.
- Pilot remediation plans and measuring their effectiveness.
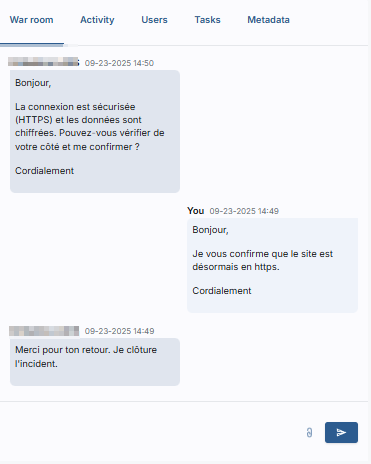
Space War Room collaborative
Each alert corresponds to an integrated warroom: you can therefore interact with a CTI analyst in real time and receive all the details necessary to resolve the incident.
Service alerting
Our dedicated analysts closely monitor your scope and produce an analysis report detailing compromised data and personalized recommendations.
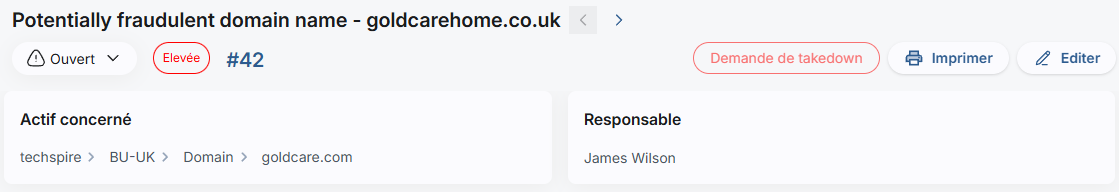
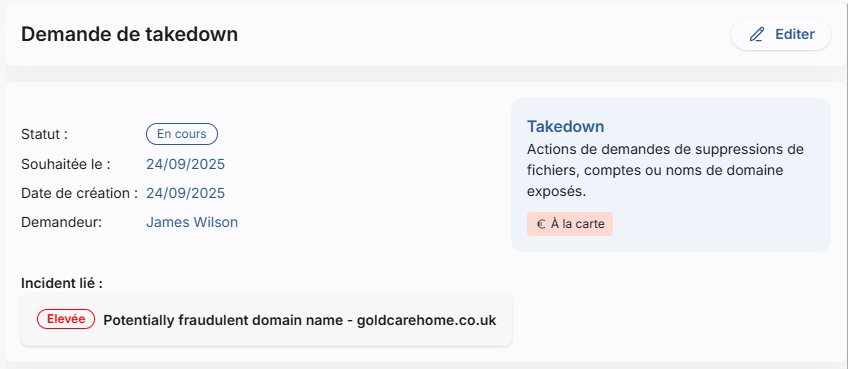
Request for Takedown
To quickly counter phishing campaigns, the CTI service integrates the ability to request the removal of suspicious domain names from the Cyboard platform.
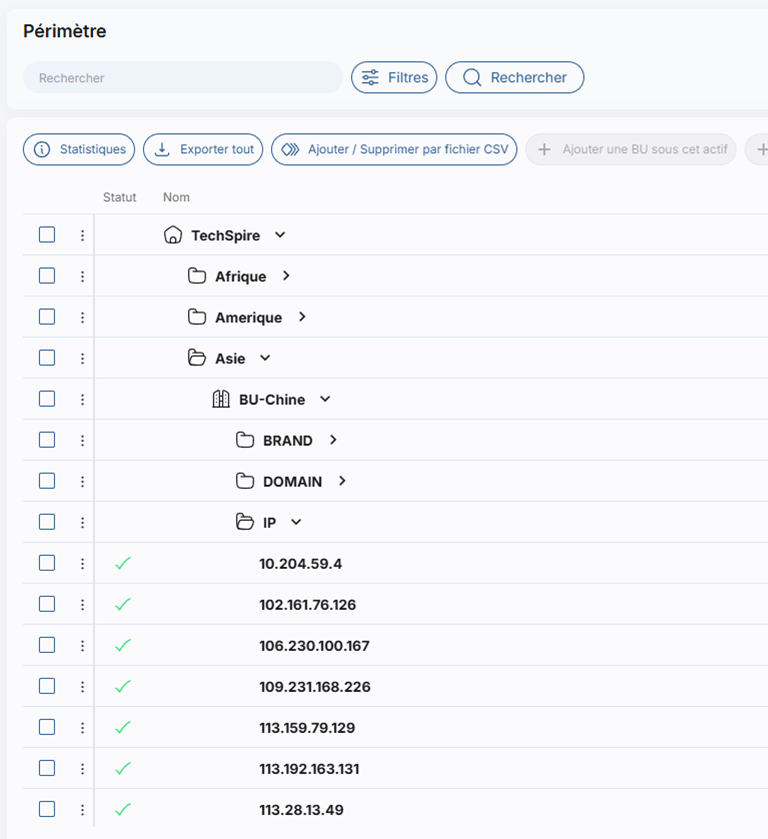
Management of perimeter
The monitoring scope communicated to our teams is centralized and accessible directly from Cyboard. Users can view and modify it at any time, thus ensuring appropriate and scalable coverage of their sensitive assets.
Cyboard, for effective risk management
Cyboard combines technology, CTI monitoring and expert advice to transform your vulnerability management into a strategic lever.
Cyboard at the heart of your 360° cybersecurity strategy
With Cyboard, security management becomes part of your company's DNA and goes beyond traditional operations:
Asset Management
Monitoring and prioritization of critical vulnerabilities.
Planning and advice
Strategic analysis of trends and impacts.
Test Cyboard
Cyboard is more than a platform: it is a trusted partner that guides management and steering towards concrete actions and tangible results.