Large Groups & Multinationals
Structuring your cybersecurity from the early stages of growth

Our program for large organizations assesses the information system and all IT environments to ensure consistent cybersecurity. We map IT infrastructures and systems to identify both cross-functional and local vulnerabilities. The approach aims to secure information systems at the group level while respecting regional contexts. We conduct IT security audits and risk analyses to prioritize risk management at the group level. Recommendations cover IT security policy, security policy, and shared operational rules. The framework defines the expected security level for each subsidiary and proposes harmonized security measures. We evaluate system security, network security, and the robustness of authentication mechanisms. Our architectural designs include encryption and cryptography to protect sensitive and confidential data. The program strengthens digital security against cyberattacks and cybercrime targeting multi-regional environments. We test resilience against hacking and attacks by hackers through exercises and operational audits. The proposed information security governance helps the CIO coordinate policies, roles, and steering committees to reduce IT risk. Our security measures include server hardening, network segmentation, EDR/antivirus, and privileged access control. We help formalize a security policy to protect critical information and assets. Deliverables include IT system maps, vulnerability matrices, and remediation plans prioritized based on risk analysis. The global SOC and multi-region monitoring are designed to detect security incidents and malicious behavior. We assess ANSSI/CNIL compliance and adapt policies to local regulations and DORA/NIS2 requirements. The plan integrates the security of cloud services, APIs, and connected devices used by subsidiaries. Our technical recommendations cover strong authentication, password management, MFA, and IAM security solutions. The framework aims to make systems secure and securable by limiting the attack surface against cyberattacks. We implement indicators to measure the level of security and the effectiveness of security measures over time. The strategy includes incident playbooks, crisis procedures, and centralized coordination of inter-business unit escalations. Our experts recommend encryption, cryptography, and data flow protection measures to ensure confidentiality. The goal is to standardize information systems security, reduce cybercrime, and protect confidential data. Request a group workshop—receive an IT security audit, systems mapping, and a prioritized roadmap.
Specific challenges for international groups
In a large group or multinational corporation, cybersecurity must function like a global nervous system: strategic management from headquarters, local adaptation by entities, and consistency ensured across multiple regulatory or IT zones. In this context, security challenges are not solely technical: they are organizational, cultural, industrial and political.
Unifying heterogeneous security approaches
To provide a framework while respecting local contexts
Implementing effective multi-regional supervision
Global SOC, cross-regional detection, consolidated alerts
Managing security as a global cross-functional
Centrally controlled decentralized model
Industrializing global incident management
Harmonised procedures, IT/crisis communication/HR coordination
What this course allows you to pilot
Strategy & Governance
Proposed actions
Global IT security framework, decentralized accountability, network CISO structure
Business value
Coordinate IT security across the group, entities, geographies, and business lines.
Risks & Compliance
Proposed actions
Consolidation of risk maps, multi-country regulatory monitoring
Business value
Framing manageable compliance in complex environments
Architecture & SecOps
Proposed actions
Cloud/Data security reference model, standard policy, legacy model
Business value
Ensure consistent security across the entire hybrid/SaaS/API system
Cyber Defense Operations
Proposed actions
SOC group/regions, hierarchical detection, enriched context
Business value
Optimize the processing of weak/strong signals across the entire information system
Incident & Crisis
Proposed actions
Inter-site/BU/zone coordination, multilingual simulation
Business value
Shorten response times and unify alert systems
Resilience
Proposed actions
Macro-group business continuity/disaster recovery, cross-functional disruption management, critical dependencies
Business value
Ensuring continuity in the event of a major global event
Cyber culture
Proposed actions
Multilingual/functional/regional awareness strategy
Business value
Acculturating all key stakeholders, across all sectors and professions
This route is ideal for:
Companies with service/production centers spread across multiple continents
Multi-BU groups present in several regions or continents
Organizations subject to cross-regulations, with ISO/DORA/etc commitments.
Organizations wishing to unify their group cybersecurity without dispossessing the entities
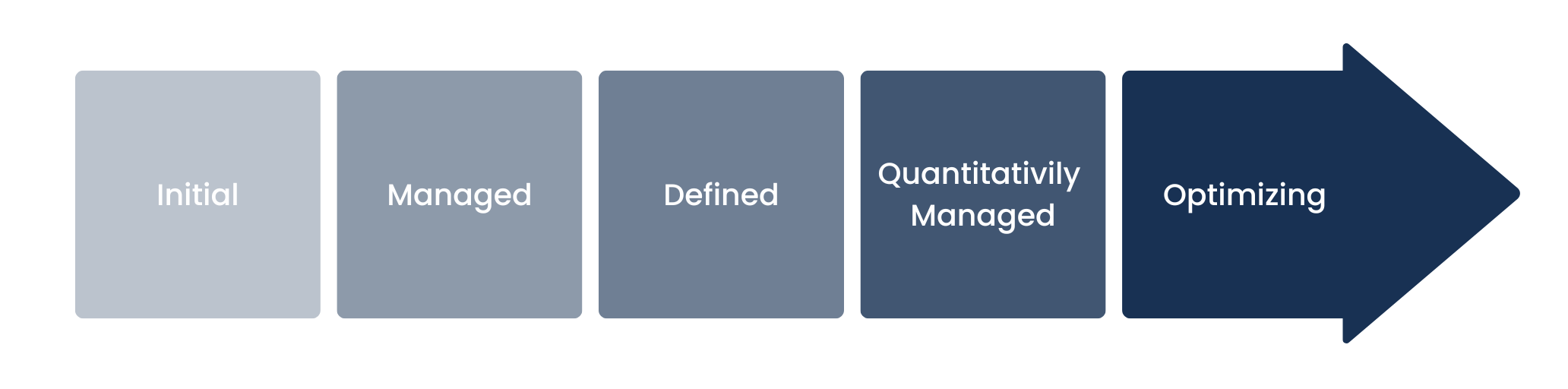
Target maturity level
Content of the Cyber Startup / Scaleup course
Preparatory phase – consolidated mapping
- Multi-level cyber governance model
- BU mapping / Zones / Subsidiaries / Maturity
- Compliance status by region or domain

Activateable strategic modules
Group security framework
Centralized & local framework, roles and levers for action
Multi-perimeter SOC
Integration of subsidiaries/regions, centralized event correlation
MCA / PCA / PRA multi-site
Coordination of inter-regional plans and dependencies
Group compliance strategy
Harmonization with ISO27001 / NIS2 / GDPR / local laws
Synchronized crisis simulations
Testing of leadership/profession/partner escalations
unifying cyber culture
Cyber ID/career path campaigns, globalized modules
- Monitoring global security without burdening subsidiaries
- Reduce costs / duplication / gaps in cybersecurity practices
- Ensuring responsiveness and unity in the event of a multi-zone crisis
- Having interoperable group dashboards
- Managing regional compliance within a coherent global framework
Our approach, multi-scale thinking
Situation encountered
- Siloed cyber governance
- Tools and SOCs are not homogeneous.
- Fragmented compliance
- Unsynchronized response plans
- Heterogeneous awareness
Our contribution
- An IT security architecture that takes local realities into account
- Interoperable, consistent, contextualized supervision
- Alignment of local requirements with central governance
- Controlled and coherent climbs at the group level
- Global planning, shared cybersecurity culture, localized tools
Practical details
Duration
9 to 18 months depending on density and scope
Delivery method
overall managed process with regional/BU variations
Areas covered
Multicloud, multi-directory, global SOC, heterogeneously deployed tools
Ready to Strengthen Your Cybersecurity?
Don't let threats catch you off guard. Discover how our program can secure your organization.