Cyber threats: a rise in the Middle East and North Africa region
[et_pb_section fb_built= »1″ admin_label= »section » _builder_version= »3.0.47″][et_pb_row admin_label= »row » _builder_version= »3.0.48″ background_size= »initial » background_position= »top_left » background_repeat= »repeat »][et_pb_column type= »4_4″ _builder_version= »3.0.47″ parallax= »off » parallax_method= »on »][et_pb_text admin_label= »Text » _builder_version= »3.0.74″ background_size= »initial » background_position= »top_left » background_repeat= »repeat »]
This article deals with the still little-known subject of... cyber threats within the’'Arabic-speaking ecosystem' They can take various forms (hacker groups, malware sales, tailored phishing campaigns, bank fraud, or counterfeiting) and originate from local actors motivated by diverse factors. This study aims to demonstrate that these threats can have a impact on companies located in the Middle East and North Africa (MENA) region.
With a total population of over 420 million and an economy exceeding €2.4 trillion, the Middle East and North Africa (MENA) region encompasses 22 [1] These countries share the same language, as well as ethnic, religious, and cultural similarities. However, they exhibit significant heterogeneity from a demographic, political, linguistic, and economic perspective, as well as considerable disparities both within the region itself and with other countries.
In general, companies operating in the Middle East and North Africa region are pleased with their operations; this region is driven by significant growth dynamics.The region's great growth potential is characterized by its economic diversification ongoing. Its development is driven by a strategy of modernizing traditional sectors and developing promising sectors for the future. This diversity is a major asset and a real draw for foreign companies.
By comparing the Internet infrastructure implementations as well as the importance of telecommunications companies [2], Significant disparities are observed within the’cyber space of the MENA region. In this respect, North Africa appears to have a much better network than the Middle East.
With the digitization With the increasing number of companies operating in the Middle East and North Africa region, they face a variety of cyber threats such as APT (advanced persistent threats) attacks, cyber-activism, THE cyber espionage, there digital fraud. Furthermore, we also observed some attacks of the type phishing or attacks using ransomware, of the spyware, etc. They seemed to be favored by attackers operating in this region.
After more than two years devoted to observing and analyzing the’Arabic-speaking ecosystem on the malicious web networks, our cell of Cyber Threat Intelligence decided to share its observations and report on the diversity of techniques, operating methods, motivations, and functions within this microcosm. In light of these elements, we will detail the risks faced by companies operating in the region (MENA).
OUR monitoring unit, and, as part of its daily support to clients, has detected threats from offensive actors originating in the Middle East involving all types of threats targeting European organizations, the main economic location of our unit: data breach collaborators, DDoS attack preparation (Denial of service attack), phishing, trademark infringement, damage to image And denigration, frauds, etc.
The APTs
The MENA region has historically been a sensitive area in all areas, including cybersecurity. Companies operating in the region, as well as local governments, are prime targets for many types of actors, including perpetrators of...’APT (Advanced Persistent Threat).
Political and military conflicts in the Middle East resonate in the region's cyberspace. For example, in 2010, Iran's nuclear program was the target of an unprecedented attack, aimed at its uranium enrichment centrifuges. This event is associated with the discovery of the first malware allowing the spying on and modification of industrial systems, including SCADA systems, used for industrial process control. Named Stuxnet, This malware has been described by experts as a "« cyber weapon »"possessing an unusual level of complexity.".
The Saudi-Iranian conflict in the Middle East is believed to be a catalyst for cyberattacks in the region. Indeed, Saudi Arabia is a frequent target of cyberattacks, as evidenced by malware. Shamoon, which notably targeted the energy sector in 2012, and the public and financial sectors in 2016. Furthermore, the latest analysis from the cybersecurity firm FireEye, dated September 2017, specifies that the hacking group behind Shamoon has alleged links to the Iranian government. Dubbed APT33, and active since 2013, the group is believed to be behind cyberattacks targeting the energy sector in Saudi Arabia. In July 2017, Qatar also accused the United Arab Emirates of being behind the hacking of its official news agency (QNA) in May 2017, which caused a deep diplomatic and commercial crisis in the Gulf region for over a year.
Finally, another group, known as "« Desert Falcons »", and active since 2011, reportedly targets numerous large companies and individuals in the Middle East. Experts consider this group to be the leading group developing and conducting operations of large-scale cyber espionage. Their activities have reportedly already claimed 3,000 victims in some fifty countries. The list of targeted institutions includes defense agencies and government bodies, particularly those responsible for combating money laundering, figures in the business and media sectors, research and educational institutions, energy networks, activists and political leaders, physical security companies, as well as other targets in possession of strategic information. The method used by Desert Falcon is said to be... spear phishing via emails and social media.
On a smaller scale, the cyber-malicious offers are diversifying through platforms where any individual can obtain the tools and advice useful for the attack they wish to carry out.
These malicious offers are intensifying daily, taking many forms, ranging from simple hacking service, passing through the spam distribution offers, there malware sales and feat, the selling and sharing bank cards, identity documents, and other documents, as well as the sale of counterfeit products. We will try to illustrate concrete examples of all these services.
Ideology: A catalyst for malicious actors
ALALAMIYA, Dev-Point or SOQOR, are the names of forums The most popular forums dedicated to hacking in the MENA region. Hacking activity characterized by a sense of camaraderie and cordiality in exchanges. These forums also contain ideological sections. [Figures 1 and 2].
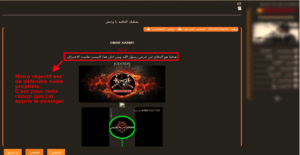 Figure 1: A message from a hacker explaining his motivations on the AlAlamiya forum
Figure 1: A message from a hacker explaining his motivations on the AlAlamiya forum
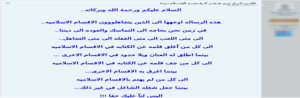
Figure 2: A message calling on members of the Soqor forum to enrich the forum's religion section
Selling malware: A business in its own right
Funding vectors
There selling malware is a very widespread activity within Arabic-speaking communities. Naturally, one can find presentations of all types of malware on Arabic-language forums, with download links, tutorials, and discussion forums for resolving potential technical problems. For example, the WannaCry ransomware, used during a global cyberattack massive in May 2017, and which affected more than 300,000 computers in over 150 countries, has been for sale on an Arabic-language forum since May 2017 [Figure 3].
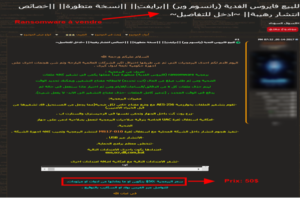
Figure 3: The WannaCry ransomware is for sale on the AlAlamiya forum
Within this same forum, members also offer farms for sale (programs that allow an individual or malware to exploit a computer security vulnerability). In our example, the seller also provides a video explaining how the kit works and demonstrating its validity. [Figure 4].
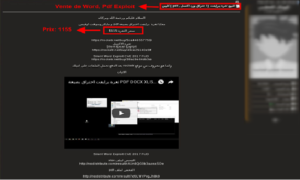
Figure 4: "Exploit" for sale on the Hack-int forum for 115$ on the AlAlamiya forum
Another member proposes a malware allowing’inject the hacker's bitcoin address in place of the legitimate payment address for the transaction. The author of this advertisement explains that his tool would detect bitcoin addresses in the clipboard at the time of the "copy" action, and replaces the "pasted" bitcoin address with that of the hacker. [Figure 5].
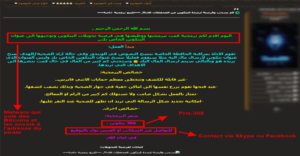
Figure 5: Malware to steal the Bitcoin cryptocurrency, for sale for 30$ on the AlAlamiya forum
We have also observed a new trend, becoming widespread in the Arabic-speaking community: the development of malicious tools by local actors, and their promotion within certain Arabic-speaking communities. This is the case of a Spyware (spyware), called Spynote and designed by the administrators of Iraqi forum IQ-Team, [Figure 6] Recently shut down, this local spyware became very popular thanks to its technical capabilities and the documentation publicly shared by its authors. Spynote, which doesn't require physical access to the victim's device and targets Android devices, is reportedly capable of viewing all messages on various social media applications (WhatsApp, Messenger, Viber, etc.), reading SMS messages, listening to conversations, accessing data, and installing applications. Its accessibility and ease of use (even for a non-technical user) explain its widespread distribution within Arabic-speaking cyber communities. The fifth version of this spyware was available on the Iraqi forum until its closure and remains available for free download on several Arabic and English-language forums. This malware is already well-known and has been the subject of several analyses. https://researchcenter.paloaltonetworks.com/2016/07/unit42-spynote-android-trojan-builder-leaked/
Figure 6: The Iraqi forum iq-team before its closure
Figure 7: The official YouTube channel of the Iraqi forum iq-team: a video explaining how the spyware works
Figure 8: Iraqi spyware being downloaded from an English-language website
On the digital marketplace, a choice between "Phishing as a Service" or "Tailor-made Phishing"«
THE phishing is another specialty of actors in the region. In the majority of e-commerce sections of malicious Arabic-language forums, sellers offer pages of custom phishing or targeting world-renowned sites, for a fee of approximately $30 [Figure 9].
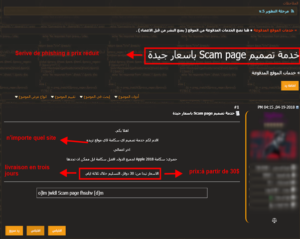
Figure 9: Phishing service on the AlAlamiya forum
Other actors have chosen to set up websites dedicated exclusively to phishing. These actors offer, through their sites, hundreds of phishing pages targeting major companies such as Facebook, PayPal, and Netflix, as well as French telecommunications companies. These pages are generated by malicious actors and made freely available to the public on their websites. [Figure 10]. Once registered on their site, any internet user can share the malicious page to reach more victims. The login credentials and information gathered through this channel are then sent via a command and control (C&C) server to the malicious actors. [Figure 11].
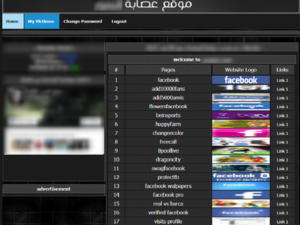
Figure 10: Phishing page generation service on Anomor
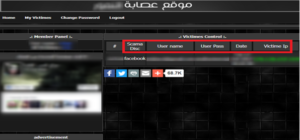
Figure 11: The (pirate) client area of the Anomor phishing page generation service
The Arabic-speaking ecosystem is also marked by cyber threats related to the fraud, like the provision of false documents, as well as the resale of personal data or bank cards. But Arabic-speaking players are not interested in bank cards or local forgeries. Indeed, the usual fraud schemes do not allow the use of stolen data in the MENA region because, in some Arab countries, electronic payment methods are not sufficiently developed for widespread use. This situation is reflected in the number of Arabic-language e-commerce sites, which remains disproportionate to the population.
Bank fraud: why hide it?
To meet this high demand, sections of malicious forums have been created to organize this trade. Some forums and communities are more audacious and are willing to sacrifice their anonymity to gain visibility on social media.
In this situation, the trade in bank cards and forged foreign documents has developed rapidly. The most common activity is...’purchase of computer equipment via stolen bank cards or the resale of these bank cards.
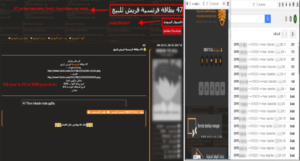
Figure 12: Sale of 47 French bank cards on the AlAlamiya forum
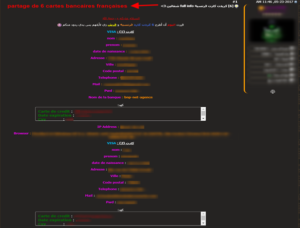
Figure 13: Sharing of 6 French bank cards on the AlAlamiya forum

Figure 14: Sale of four French identity cards
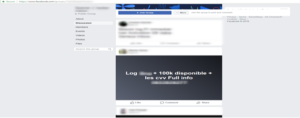
Figure 15: Sale of login credentials belonging to a customer of a French bank, on a Maghreb Facebook group
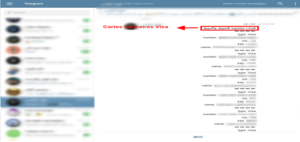
Figure 16: Sharing bank card data on an Arabic Telegram channel
Counterfeiting is rampant.
There counterfeit It is also found on platforms dedicated to Arabic-language classified ads, but it is difficult to obtain a precise and reliable assessment of its extent. By searching for the name of a well-known brand (in the luxury sector, for example) on one of these sites, one can observe a significant number of ads offering counterfeit products; the same result can be obtained simply by searching for the keywords "counterfeit" or "forgery" in Arabic. It should be noted that counterfeiting in Arabic-speaking communities affects all sectors.Counterfeiters primarily operate on an opportunistic and profit-driven strategy, targeting the most popular brands. We have also detected several groups on social media (Facebook, WhatsApp, Telegram, etc.), dedicated to the sale of counterfeit products.
Conclusion
Modern Standard Arabic is the official language in the MENA region, used particularly in administration, education, and the media. It is the most widely used and understood language in the region, even if it is not the native language of every Arabic speaker. However, each geographical area has a dialect, which can be considered the spoken language of the country: the North African or Maghrebi dialect, the Egyptian and Levantine dialects, and the Gulf dialect. Communication between people in Arab countries can also be in French (in countries where French is a second language, e.g., Morocco, Algeria, Tunisia), in English in the case of the’Egypt and the Gulf countries, or even in French and English as in Lebanon.
Each geographical area of the region (MENA) has its own dialect, as well as its own history and specific characteristics; it is therefore necessary to master them perfectly and independently of each other in order to have a comprehensive analysis and vision of the ecosystem and adapt the monitoring strategy depending on the stakes.
THE cyber threats Contrary to the limited number of companies established in the region in the civilian sector, we have observed a strong attachment to religion and ideology. The spaces for interaction between stakeholders reflect the nature of the society, where feelings of brotherhood, religious affiliation, and the common enemy take precedence over discussions. Companies based in the region must understand the characteristic of Arab societies Poor communication, for example, can have harmful repercussions.
[1] Morocco, Algeria, Tunisia, Libya, Mauritania, Egypt, Lebanon, Syria, Israel, Jordan, Palestine, Iraq, Saudi Arabia, Qatar, Yemen, United Arab Emirates, Kuwait, Oman, Sudan, Somalia, Djibouti, Iran
[/et_pb_text][/et_pb_column][/et_pb_row][/et_pb_section]







