OIV & Ministries
Cybersecurity of national interest: rigor, coordination and sovereignty

Our approach for Operators of Vital Importance (OIVs) and government ministries assesses the entire information system and critical IT environments. Securing infrastructure aims to reduce vulnerabilities and mitigate IT risk nationwide. We conduct IT security audits and assessments to verify compliance and operational security levels. Risk analysis maps attack scenarios and aligns risk management with business priorities. Our measures strengthen system security and the security of information systems exposed to advanced threats. Our technical recommendations include encryption and cryptography to protect sensitive data and communications. We test authentication mechanisms, password strength, and Identity and Access Management (IAM) policies to secure access. The program integrates the security of servers, workstations, and connected services to limit the attack surface. This approach evaluates digital security and resilience against cyberattacks and cybercrime. We define a clear IT security policy and operational security measures tailored to OIVs. The proposed security solutions (EDR, SIEM, network segmentation) improve the detection and response to security incidents. The plan prioritizes actions to make your IT systems secure and your confidential information protected. Our experts measure the level of security expected by the authorities and translate ANSSI requirements into auditable deliverables. The framework includes playbooks, procedures, and exercises to improve security incident management in operational mode. We assess network and system security to guarantee the continuity of essential public services. The security audit identifies technical vulnerabilities, configuration flaws, and exfiltration scenarios. Our system security recommendations cover encryption at rest, encryption in transit, and cryptographic best practices. Information systems security governance consolidates security policy, CIO responsibilities, and inter-entity coordination. Security measures include server hardening, segmentation, encrypted backups, and centralized monitoring. The project aims to protect the security of sensitive information processed by government agencies and public services. We help data controllers reconcile CNIL compliance, NIS2/LPM requirements, and auditable evidence. Our interventions reduce exposure to malicious actors, hackers, and targeted hacking scenarios. The final deliverable includes an IT mapping, a risk matrix, and a prioritized roadmap for long-term system security. Request an OIV audit—obtain an operational security roadmap and actionable recommendations.
Specific challenges for operators of vital importance and institutions
Critical infrastructure operators, sensitive operators, government ministries: you are subject to targeted attacks, critical resilience criteria, and strict compliance obligations. Every vulnerability is a potential breach of national security. Every incident can bring down an entire sector.
Meeting LPM/NIS2 requirements
Production of verifiable and auditable deliverables
Working with qualified/trusted service providers
Outsourced services compliant with SecNumCloud or HDS
Orchestrating security between entities, departments, and partners
Integrated multi-level cyber governance
A rapidly evolving tech stack
Maintaining security consistency despite agility.
Responding to targeted attacks
Activation of alert, detection, and analysis systems
Auditable at any time by the State / sectoral authority
Documented, managed ISO/ANSSI approach
Strengthening national resilience
critical business continuity/disaster recovery, supply chain monitoring
What this course allows you to pilot
Strategy & Governance
Proposed actions
LPM file, ministerial cybersecurity policy, cybersecurity master plan
Business value
Managing security as a national strategic lever
Risks & Compliance
Proposed actions
Critical IT mapping, LPM compliance plan, NIS2, GDPR
Business value
Provide the regulator with complete, enforceable visibility
Architecture & SecOps
Proposed actions
Cloud perimeter management / sovereignty / network segmentation
Business value
Align the architecture with the ANSSI & SGDSN doctrines
Cyber Defense Operations
Proposed actions
Sovereign SOC, sector supervision, SCADA/OT
Business value
Managing advanced, consistent, and sector-specific detection
Incident & Crisis
Proposed actions
National crisis procedures, CERT/CSIRT/Business Crisis Unit management
Business value
Managing crises both in and out of the heat of the moment in sensitive contexts
Resilience
Proposed actions
Critical asset business continuity/disaster recovery, multi-year simulations, dependency management
Business value
Ensuring the continuity of public/vital services
Cyber culture
Proposed actions
Raising awareness among managers, policymakers, and agents subject to clearance
Business value
Aligning behaviors with the strategic criticality of the IS
This route is ideal for:
Operators of Vital Importance (OIVs) as defined by the State
Ministries and central or decentralized government departments
Public health facilities with critical information systems (LPM/HDS)
Sovereign bodies subject to the LPM, NIS2 or sectoral doctrines (energy, transport, defense…)
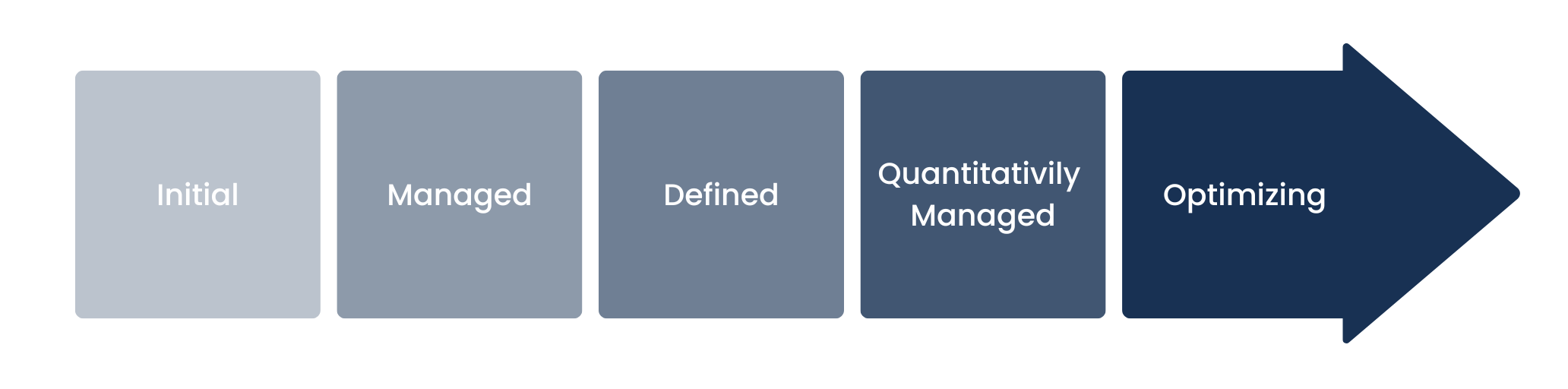
Target maturity level
OIV & Ministries Course Content
Structuring phase
- Sector compliance audit
- Mapping of vital systems
- LPM/NIS2/DORA Compliance Plan
- Development or update of the SSI master plan

Activateable strategic modules
State-level cybersecurity governance
Information Systems Security Policy (ISSP), steering committee, national plan, steering unit
Sovereign SOC 24/7
Cloud/public/OT coverage + dedicated QoS/FOU/ANSSI alerting
Feedback on the incident
Incident follow-up management and audit documentation
Multi-level business continuity/drafting plan
Sectoral dependencies, impersonal variations
Crisis simulations
Role-playing games involving all stakeholders
Hierarchical awareness
Training for managers, sensitive personnel, elected officials or relevant authorities
- To provide auditable guarantees to the State or authorities
- Securing critical systems effectively
- Strengthening crisis management and post-incident analysis capabilities
- Driving national resilience through your business
- Start structuring your organization to achieve ISO 27001 or CyberScore certification.
An approach based on sovereignty, compliance and anticipation
Situation encountered
- SI critical little mapped
- Partial documentation
- "Hot" risks that have not been simulated for a long time
- Imposed conformity without a project vision
- Awareness perceived as complex
Our contribution
- Identification of assets & sector dependencies
- Generation of an updated and enforceable foundation
- Realistic crisis scenarios involving all levels
- A concrete plan, broken down into smaller steps, adapted to internal capabilities
- Functional and strategic targeting of the cybersecurity culture
Practical details
Duration
12 to 24 months depending on the scope and national requirements
Delivery method
progressive or in support of the current IT security manager
Areas covered
OT, Public/Sovereign Cloud, Administrative Business Systems
Ready to Strengthen Your Cybersecurity?
Don't let threats catch you off guard. Discover how our program can secure your organization.