SMEs & Mid-Sized Companies
Structuring your cybersecurity sustainably and industrializing your practices without complexity

Our SME & Mid-Sized Company program assesses your information system and IT environments to define an appropriate level of security. We conduct a risk analysis to prioritize security measures and reduce overall IT risk. The approach includes regular IT security audits to identify vulnerabilities on servers, workstations, and applications. Securing information systems involves centralized authentication controls, password management, and MFA (Multi-Factor Authentication). We help the CIO formalize an operational IT security policy that is easily understood by the executive committee. Our recommendations cover system security, network security, and the protection of sensitive and confidential data. The plan includes encryption and cryptography measures to protect communications and data at rest. The security of connected systems (IoT, cloud, SaaS) is mapped to avoid operational weaknesses. We implement security solutions (EDR/antivirus, SIEM, IAM) and playbooks for security incidents. The framework includes the integration of ANSSI-compliant controls and consideration of CNIL requirements for data processing. Our audits and architecture reviews aim to reduce structural vulnerabilities and improve resilience against cyberattacks. We implement pragmatic information security governance to industrialize risk management and cross-functional oversight. The proposed managed or hybrid SOC ensures continuous detection and reduces response time to security incidents. Actions include server hardening, network segmentation, encrypted backups, and secrets management. We identify IT risks related to dependencies and infrastructure to prioritize remediation. Our experts advise on security policy, system security, and the protection of critical assets. Training and awareness programs for teams help reduce incidents caused by malicious behavior or human error. Deliverables include an IT infrastructure map, a risk matrix, and a prioritized action plan to secure systems. Our technical recommendations include encryption, cryptography, strong authentication, and application hardening. We support ISO 27001 / NIS2 compliance and prepare for client and regulatory audits. Our goal: to make your IT systems secure, resilient, and aligned with your business strategy and regulatory requirements. Request an IT security audit or an architecture workshop to develop an operational security roadmap.
Concrete challenges at this stage of growth
You are in a phase of structuring, industrialization, or expansion. Your information system has become critical, connected, and sometimes distributed. Your customers, partners, and regulators expect a clear security posture. It's time to lay solid, operational foundations while maintaining an efficient and appropriately scaled approach.
Structuring security governance
Clarify roles, responsibilities, and documentation.
Strengthen compliance
GDPR, ISO 27001, CyberScore, sector requirements.
Industrializing risk management
To have a formalized, prioritized, and shareable monitoring system.
Having an outsourced or hybrid SOC
Detect quickly, without overloading the teams.
Integrating security into IT & Cloud projects
To provide security expertise to project teams.
Raising awareness among the teams
Maintain a continuous safety culture throughout the company.
Improving incident response
To be prepared, structured, without relying solely on intuition.
What this course allows you to pilot
Strategy & Governance
Proposed actions
Mapping of IT security roles, Strategic Plan, Information Systems Security Policy, Cybersecurity Committee
Business value
Safety/management alignment; clear framework for ESG or audits
Risks & Compliance
Proposed actions
GDPR audit/projects, ISO 27001 or CyberScore action plan
Business value
Preparation for compliance; improved customer/partner relationships
Architecture & SecOps
Proposed actions
Cloud access review, AD/AAD hardening, Zero Trust policy
Business value
Mastery of hybrid architectures, secure cloud posture
Cyber Defense Operations
Proposed actions
Managed SOC tailored for next-generation EDR/antivirus
Business value
24/7 monitoring, detection capability and controlled scalability
Incident & Crisis
Proposed actions
Scenario mapping, exercises, response kit
Business value
Structuring a real, orchestrated, and actionable response plan
Resilience
Proposed actions
Formalized PCA/PRA, mapping of critical dependencies
Business value
Improved business continuity and customer assurance
Cyber culture
Proposed actions
Annual awareness cycle, targeted job kits
Business value
Security dynamics embedded in internal practices
This route is designed for:
SMEs with more than 50 employees, in growth or in the process of digitalization
SMEs organized by business unit/service area, with Cloud, SaaS or sensitive tools
Structures with key requirements in reporting SSI, steering committees or ESG
Organizations in joint ventures, subcontracting Or multi-site (Hybrid cloud, subsidiaries)
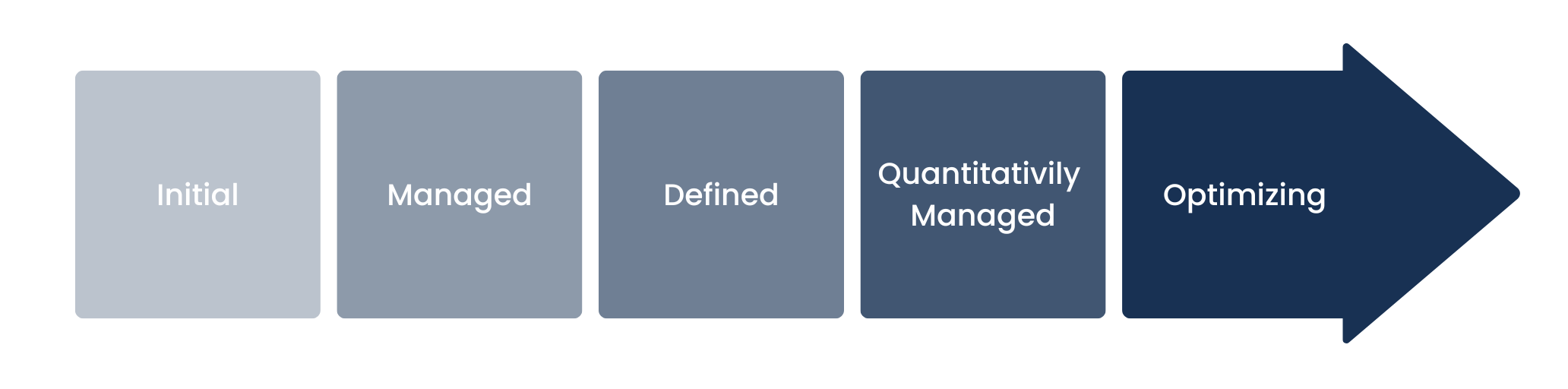
Target maturity level
Content of the SME/Mid-Sized Company course
Framework & Current Situation
- Mapping of practices and actors
- Identification of priority actions
- Strategic alignment (executive committee issues, compliance, customer expectations)

Activateable modules
progressively managed SOC
Integration of key logs, targeted detection, cross-cloud/workstation alerts
Information Systems Security Governance
Information Systems Security Policy (ISSP) kits, security committees, decision-making dashboards
GDPR Audit & Compliance
Data Protection Officer (DPO) analysis + information security measures, coordinated remediation plan
IT/Cloud Security Review
Access, backups, sensitive configurations, MFA, shadow IT
COMEX orientation table
Indicators, prioritized risks, investment projections
Annual awareness campaign
HR support / managers, personalized e-learning
- Structuring security without slowing down operational projects
- Responding effectively to audits (internal, client, regulatory)
- Streamlining security tools and practices within the company
- Improving responsiveness to operational incidents
- Establishing solid foundations for IT security governance, manageable by domain
A pragmatic approach, designed for your context
Situation encountered
- Security managed according to projects or emergencies
- Several tools or building blocks without coherence
- Risks identified but poorly formalized
- Compliance managed solely from a legal perspective
- Poor readability COMEX
Our contribution
- A consolidated vision driven by domain and role
- A harmonized and prioritized roadmap
- A traceable plan, with empowered internal stakeholders
- A security/GDPR coverage that is well-equipped and justifiable
- Clear indicators to arbitrate and unite around cybersecurity issues
Practical details
Duration
6 to 12 months depending on the areas activated
Delivery method
progressive packages or personalized pathways
Areas covered
Hybrid IT, Active Directory, SaaS, M365, Public Cloud (AWS, Azure)
Ready to Strengthen Your Cybersecurity?
Don't let threats catch you off guard. Discover how our program can secure your organization.