POV: A pentester at SSTIC 2023 – Part 2
[et_pb_section fb_built= »1″ _builder_version= »4.21.0″ _module_preset= »default » global_colors_info= »{} » theme_builder_area= »post_content »][et_pb_row _builder_version= »4.21.0″ _module_preset= »default » global_colors_info= »{} » theme_builder_area= »post_content » custom_padding= »12px|0px||0px|| » custom_margin= »-2px|-108px||1px|| » min_height= »3262.1px » hover_enabled= »0″ sticky_enabled= »0″ width= »85.7% »][et_pb_column type= »4_4″ _builder_version= »4.21.0″ _module_preset= »default » global_colors_info= »{} » theme_builder_area= »post_content »][et_pb_text content_last_edited= »off|desktop » _builder_version= »4.21.0″ _module_preset= »default » header_2_font_size= »16px » header_3_font_size= »18px » header_4_font= »|||||||| » custom_margin= »|||7px|| » global_colors_info= »{} » content__hover_enabled= »off|desktop » theme_builder_area= »post_content » hover_enabled= »0″ sticky_enabled= »0″ custom_padding= »|0px|||| » width= »99.9% »]
This article constitutes the second part of POV: A pentester at SSTIC 2023, and follows the feedback from SSTIC presentations related to the pentester profession.
Top 3 – Favorites
Among the high-quality programming at this year's event, three presentations particularly caught my attention, both for the topics covered and the delivery. This is a subjective opinion, and I encourage you to watch them now. replay of these presentations.
Deep Attack Surfaces, Shallow Bugs
Presented by Valentina Palmiotti @Chompie1337, this conference echoes a tweet published last December about a critical vulnerability found in a Windows authentication protocol (https://twitter.com/chompie1337/status/1602757336908660736).
The first part is dedicated to the path of discovering a vulnerability. Several steps are systematically included:
-
- Target selection
- The discovery of the bug
- Its exploitation
- Success or failure
The author highlights the rarity of publications by researchers who recount their failures, even though this is the most common outcome. She describes these failures as inherent to the profession and also essential. It is by following a methodical approach that researchers find vulnerabilities, and the complexity lies primarily in identifying where a flaw is located rather than in identifying the vulnerability itself. She also points out that most of the flaws found are often the same, which can become tedious.
She thus distinguishes between two research approaches. One is for a "monogamous" researcher profile: the researcher focuses on a single project to master its code as much as possible, which avoids wasting time switching topics. The other is for a researcher less loyal to their targets, who tires more quickly and therefore regularly changes their scope. This is the case for the author, who has already obtained results for different operating systems or kernel components, for example. The choice of targets is based on various criteria such as their development history, source code accessibility, architecture, etc.
Secondly, the application of this method was used to illustrate the search process. The objective was to find a critical vulnerability in a component for which few or no such vulnerabilities had been discovered in the past. The intended attack surface therefore had to meet the following criteria:
- «"High Severity": The bug found must have a major impact in a broad sense.
- «"Ubiquitous": The attack surface must be present on many systems with a default configuration
- «"Complex": The target must have complex features with unreliable user input, with components added over time.
- «"Unpopular" (optional): The project should not have been audited too extensively by researchers so that trivial vulnerabilities have not yet been discovered.
She therefore examined the Windows environment and, after listing the protocols and servers of major interest according to the stated criteria, selected SMB. Next, she listed and categorized the different components of SMB to distinguish the following: "NetBIOS," "Dialect/Capability Negotiation," "Session Setup/User Authentication," "Client File Ops & other." After evaluating each, authentication was selected. Here is the chronology of the selection process:
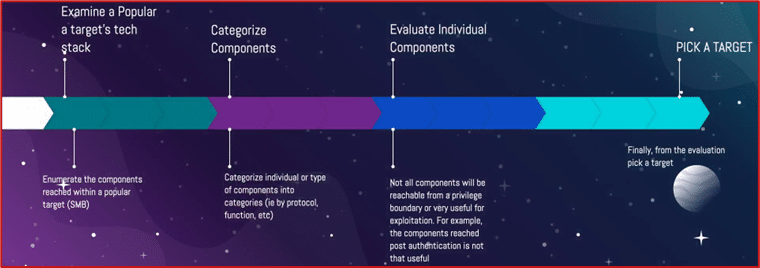
Figure 1 – Target selection process (Excerpt from the SSTIC presentation, slide 41)
Windows authentication relies on the Security Support Provider Interface (SSPI) and uses Security Support Providers (SSPs) in the form of DLLs. The main SSPs are Keberos, NTLM, PKU2U, CredSSP, SPNEGO, and NEGOEXTS. Since the latter two have very few known vulnerabilities (one for SPNEGO and none for NEGOEXTS), they were the natural choice.
Once the target was determined, the code analysis phase could begin, starting by finding the implementation of NEGOEXT (loaded at startup in LSA) and then reverse engineering this protocol. After reading the protocol documentation, the goal was then to find the function of parsing of messages. Once identified and after several analysis passes, a race condition can be exploited following the sending of multiple Negoex Session Setup requests. Its exploitation can allow an attacker to execute arbitrary code remotely.
Finally, to the problem of "Finding a bug with a major impact in a widely used and complex technology," Chompie responds with CVE-2022-37958, a vulnerability in SPNego NegoEx leading to a critical failure escape (CFE). And to conclude, attack surface analysis is just as much an art as vulnerability research.
CERTA/CERT-FR: A look back at 20+ years of CERTs at ANSSI
The deputy director of operations at ANSSI, Mathieu Feuillet, intervened to the closing presentation by reviewing the history of the ANSSI CERT and its main activities.
From CERT-A, created in anticipation of the Y2K bug, to the CERT-FR we know today, the organization has grown progressively in response to cyber threats, evolving both structurally and in terms of the resources deployed. In parallel, CERT-FR also contributes to the development of the CSIRT ecosystem by supporting the various stakeholders. Today, the operations conducted at the heart of the agency address espionage, destabilization, and cybercrime attacks.
The 2011 Bercy breach was a pivotal moment in the agency's operational activity. Indeed, the detection of this incident, a campaign "linked to China through open sources," represented the first large-scale operation that allowed for the establishment of principles subsequently applied numerous times. This event marked the beginning of the consistent targeting of France for political, diplomatic, economic, and industrial purposes. A timeline of attacks suffered by a key government sector was presented, highlighting the omnipresence of attacks that systematically involved at least four simultaneous malicious activities:
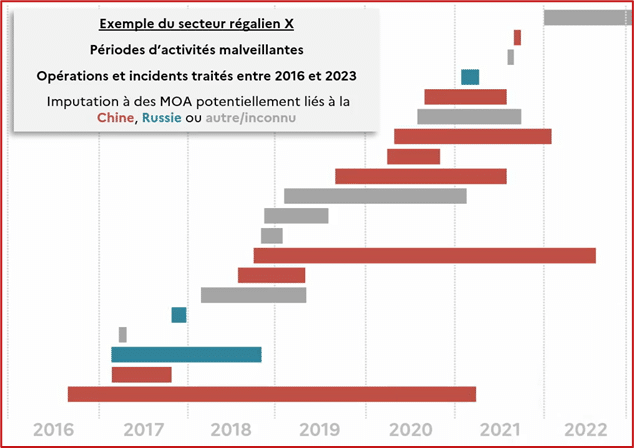
Figure 2 – Periods of malicious activity for a sovereign sector X (Extract from the SSTIC presentation, slide 21)
For the next three years, the attacks were persistent, large-scale, and targeted both government agencies and critical infrastructure. The latter were then included in the scope of the operation. Starting in 2017, these attacks returned, more discreet than before, and increasingly targeted IT services companies and other downstream entities, before rebounding on the targets themselves. Finally, since 2021, and still with the same rebound strategy, the targeted organizations are increasingly smaller and generally lack adequate security measures. In addition to the aforementioned targeted entities, embedded equipment such as routers, firewalls, and Wi-Fi access points are also being targeted.
2021 has seen the most mass data breaches to date. New techniques have been deployed, including the publication of certain attacker indicators and methods to hinder attacks. 2021 was also the year of Pegasus, the spying on high-profile individuals through the compromise of their phones, as well as Solarwinds and Log4j, for which proactive measures were developed to better protect potential victims.
Furthermore, regarding destabilization, the agency has notably had to combat hacktivism, which emerged significantly following the 2015 attacks and the 2022 war in Ukraine. These malicious actions are politically motivated and primarily involve denial-of-service attacks and defacement (for example, the sabotage operation of TV5 Monde in 2015, or Ka-Sat in 2022).
As for cybercrime, the emergence of ransomware began in 2018 with the targeting of large entities ("big game hunting"), less precise and more opportunistic than before. The victims are generally companies with the least security compared to the average ("In cybercrime, it's like when you're being chased by a lion: you shouldn't outrun the lion, you should outrun someone else"). The impacts of this type of attack vary and materialize in concrete ways. For example, for healthcare facilities, the consequences directly affect patients.
In conclusion, defensive actions are essential and effective in the face of an increasing threat.
Bug hunting in Steam: a journey into the Remote Play protocol
Another presentation A vulnerability search, this time with Valentino Ricotta (@face0xff), has been exposed, concerning a protocol on the Steam platform. The author targeted this Valve studio platform due to its popularity—it's the most used by online gamers—as well as the wide range of features it offers. The attack surface for targeting a player includes game components, the Source engine common to Valve games, the Steamworks API, and the Steam client. The latter has fewer known vulnerabilities and was therefore chosen by the author.
During his analysis of the client, Valentino encountered the undocumented "Remote Play" protocol, allowing a player who does not own the game to play through another player who does, combining streaming and remote control (which echoes his presentation from last year on RDP).
More specifically, he explains how this protocol works: to start a session, the host sends an invitation link to the guest, and then a direct connection is established between them (P2P / transparent relay). The client can then attack the host and vice versa. The most impactful scenario is an attack on the guest (the client): the only requirement for the guest is to have a Steam client. By exploiting the "steam://" wrapper, which can be hidden on a web page, an attacker (the host) could establish a connection with users.
Once the protocol's behavior was determined, its implementation was studied. A phase of reverse This made it possible to determine the logical path of network flows that pass successively through:
- Network reception, the interface for exchanging data
- The processing of packet headers, which introduces the concept of channel
- The distribution of packets according to their channel.
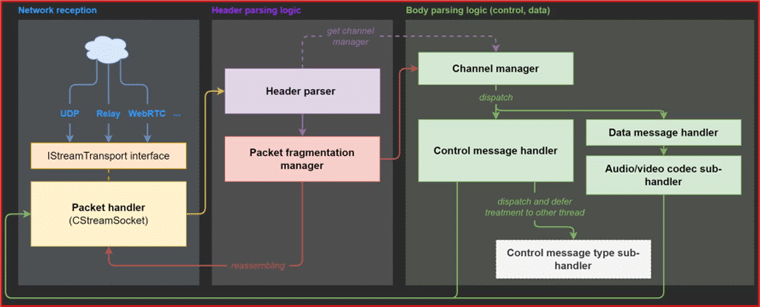
Figure 3 – Logical representation of network flows (Extract from the SSTIC presentation, slide 31)
The author explains that channels are layers of abstraction used to parallelize data transmission depending on whether it involves audio, video, control streams, etc. He chose to focus on three of them (control, statistics, and data) and defined his target surface in this way:
-
- Control messages (about a hundred types of messages)
- The remote HID that adds control messages processed with higher priority
- Audio and video codecs
To find vulnerabilities, the first step in his approach was to reimplement Remote Play, including both the client and server, with the aim of efficiently performing proof-of-concept tests. This approach evolved into a fuzzer, rpfuzz, which offers the ability to interact directly with the client (guest) or server (host), maintain a history of packets, replay and modify them, and organize packets to play a specific scenario. Modifying packets is done using another tool developed by the author, pbfuzz. Here is the architecture of the test environment:
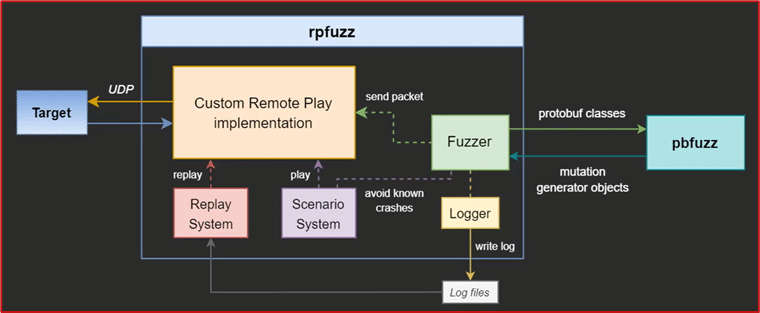
Figure 4 – Diagram of the test environment (Extract from the SSTIC presentation, slide 62)
Ultimately, this led to the discovery of about ten vulnerabilities affecting all platforms. The two main ones that have been fixed and presented affect control messages and are of the following types:
-
- «"String format": its exploitation allows for the leakage of client memory information: breaking the ASLR and scanning the memory, for example.
- «"Request Forgery": the attack can lead to a leak of local resources or a scan of the internal network, for example.
[/et_pb_text][/et_pb_column][/et_pb_row][/et_pb_section]







