Security Operation Center (SOC)
Intrinsec offers an outsourced SOC in France guaranteeing real-time detection of cyber threats.
Our Security Operations Center leverages cutting-edge SIEM technologies and a SOAR tool to automate incident response. This SOC as a Service offering provides 24/7 security monitoring with certified analysts.
This Security Operations Center (SOC) is dedicated to monitoring and managing security incidents. Also known as the operations center, it coordinates security operations and incident management across the entire organization. The center leverages advanced tools such as SIEM, SOAR, EDR, and other solutions to orchestrate incident processing, detection, and response. This approach strengthens the company's security posture through continuous monitoring and proactive threat management. The SOC function is now critical, with clearly defined roles for each member of the SOC team, including managers, analysts, and engineers. SOC teams possess diverse skills to ensure the security, compliance, and effective management of cybersecurity processes. This structure inspires customer confidence by guaranteeing security and regulatory compliance. The SOC manages and protects a wide range of resources, including databases, the network, websites, and the company's intellectual property. It collects and analyzes information from various elements of the information system to quickly detect incidents. The scope of the SOC includes monitoring critical systems, applications, and infrastructure. In the event of an incident, the SOC aims to limit damage by controlling access to systems and resetting credentials if necessary. It constitutes the first line of defense against cyber threats. Note that some SOC tools, resources, or documentation may be available in English. Even in the absence of concrete evidence, it is important to report anything suspicious to allow for a thorough investigation.
Our Security Operations Center leverages cutting-edge SIEM technologies and a SOAR tool to automate incident response. This SOC as a Service offering provides 24/7 security monitoring with certified analysts.
Your major challenges
Strengthen your SOC's detection and response capabilities against a targeted attack (APT)
Improving the responsiveness of my SOC to an intrusion, from detection to containment, in real-world conditions.
Understanding and addressing security incidents in a structured manner
Ensure continuous monitoring in accordance with your security strategy


From identified risk to active and contextualized detection
Intrinsec's outsourced SOC is based on dual expertise: technological and business. It is custom-built according to your identified risks, constraints, and environment.
Why does your company need a SOC?
Anticipate, detect, and respond effectively to cyber threats with our risk-oriented SOC. Our experts support you in improving your overall security posture through continuous monitoring and proactive incident management.
Continuous detection
- Impact on your business
Increased visibility into suspicious activities and risky behavior, regardless of the technical environment.
Continuous detection relies on network monitoring, information gathering from logs and events, and database analysis to quickly identify any potential threats.
- Our approach
Implementation of hybrid or fully outsourced supervision, based on your actual risks, your organization and your reference frameworks.

Relevant and actionable alerts
- Impact on your business
Fewer unnecessary alerts, more actionable insights for your technical teams and CISO
- Our approach
Alert handling is the first line of defense in your security operations center, relying on automated processes to respond quickly and effectively to threats.
Building business scenarios, integrating Threat Intelligence, prioritizing by criticality

Structured reaction
- Impact on your business
A clear framework for each incident: who decides, who acts, how to track and document it.
- Our approach
Deployment of automated workflows (SOAR), coordination with your crisis, PRA/PCA and GRC teams.

Our technical building blocks for a complete operational defense

Vulnerability management
We detect, prioritize and support the remediation of vulnerabilities on your critical assets through continuous monitoring.

Endpoint Security
Centralized deployment and management of EPP/EDR to counter threats targeting user terminals and servers.

Cloud Security
Visibility into configurations, anomaly detection and native integration with platforms (AWS, Azure, GCP).

SOC & 24/7 Detection
Our outsourced SOC continuously monitors your environments to detect threats, respond to incidents, and ensure your resilience.
Our SOC services to orchestrate detection & response
Each SOC mission includes a detailed correction plan and remediation assistance.
Automation and enrichment
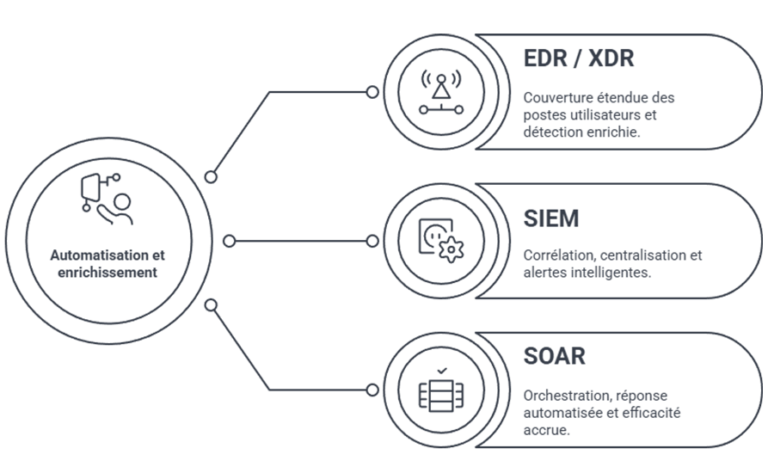
Best of Breed: Synergy for Enhanced Security
At Intrinsec, we believe the best defense against cyber threats lies in a combination of cutting-edge technologies and diverse expertise. That's why we partner with leading technology providers to offer our clients unparalleled detection solutions.







Our cover
Why choose an outsourced or hybrid Intrinsec SOC?
Challenges
Continuous operational maintenance, rapid detection & response
Challenges
NIS2, Zero Trust, sovereignty, Patch Management
Risks covered
Ransomware, external hacking, phishing, internal compromise
Methods of intervention
Managed Service / Fixed Price / 24/7 Managed Service
SOC & 360° Cybersecurity
The SOC is the operational backbone of your proactive posture
Why choose Intrinsec?
Frequently Asked Questions
An outsourced SOC (Security Operations Center) is an operational security center managed by an external cybersecurity provider. Unlike an in-house SOC, an outsourced SOC allows companies to benefit from 24/7 monitoring without recruiting in-house cybersecurity experts. Our SOC as a Service offers real-time threat detection, incident response, and compliance with French standards (ANSSI, NIS2, DORA).
Outsourcing your SOC offers several major advantages: cost reductions of 40 to 601 TEPs by pooling resources, access to significantly enhanced expertise thanks to analysts experienced in diverse environments, and cutting-edge technologies (SIEM, SOAR, EDR) without any initial investment. An outsourced SOC also guarantees 24/7 availability and enhanced threat intelligence.
Our real-time detection relies on a centralized SIEM platform that aggregates and correlates logs from across your entire infrastructure. SOAR tools automate the response to detected incidents, while our SOC analysts continuously monitor anomalies and suspicious behavior. Real-time intrusion detection combines artificial intelligence and human expertise to identify advanced threats (APTs, ransomware, data exfiltration).
A Security Information and Event Management (SIEM) system is the central platform of a Security Operations Center. It collects, normalizes, and analyzes security events from across the entire information system. Our managed SIEM enables anomaly detection, event correlation, and real-time alert generation. It is the essential tool for security monitoring and regulatory compliance.
The Security Operations Center (SOC) is the operational hub that brings together teams, processes, and technologies. The Security Information and Event Management (SIEM) platform is the platform for monitoring and analyzing security events. The Security Orchestration, Automation, and Response (SOAR) system automates incident response and orchestrates the various security tools. Our outsourced SOC integrates these three components for optimal protection.
Our outsourced SOC guarantees real-time detection with alerts generated in less than 5 minutes. Critical incidents are handled within a maximum of 15 minutes, 24/7/365. For major incidents, our forensic and incident response team can be mobilized within 2 hours. These commitments are formalized in our SLA (Service Level Agreement).
Any organization handling sensitive data should have a Security Operations Center (SOC): SMEs subject to NIS2, financial sector companies (DORA), e-commerce, healthcare, industry, and public authorities. Our Security Operations Center adapts to SMEs/Mid-sized companies, public entities, large corporations and multinationals with modular offerings. Even small businesses can benefit from an outsourced SOC thanks to our scalable SOC as a Service packages.
Ready to Strengthen Your Cybersecurity?
Protect what really matters to your business. Our experts
cybersecurity experts will assist you in securing your
digital assets.

