Our Startups & Scaleups program secures your information system from the earliest stages of growth. We assess your IT environments and servers to define a security level tailored to your product roadmap. This approach includes a risk analysis to prioritize security measures and mitigate IT risk. We help you formalize a simple and operational IT security policy, easily understood by the CIO and the executive committee. Securing systems involves implementing strong authentication, MFA, and robust password management. Our recommendations cover information system security, network security, and the protection of sensitive data. Technical quick wins include data encryption, cryptography implementation, and server hardening. We conduct security audits and IT security assessments to verify your controls and detect security vulnerabilities. User awareness and the integration of best practices reduce security incidents related to human behavior. Our recommended security solutions include: EDR/antivirus, IAM, network segmentation, and encrypted backups. The service covers securing connected devices and cloud services used by your Dev and Ops teams. We map IT systems, identify sensitive data, and propose targeted security measures. Our experts help align your strategy with ANSSI standards and CNIL data protection requirements. Actions include penetration testing, IAM review, secrets management, and integration of DevSecOps controls to secure code. The action plan prioritizes risk management, vulnerability remediation, and reducing exposure to cyberattacks. We recommend operational security policies to protect system and information security. The framework includes incident playbooks and response procedures to limit the impact of security incidents. Our security consultants work with the CIO to industrialize system security and automate controls. The goal is to make your environments secure, resilient, and compliant with customer and investor expectations. We measure and improve security levels through KPIs, periodic testing, and regular audits. Encryption and cryptography measures ensure the confidentiality of communications and sensitive data. We adapt security policies to the evolving IT systems and information technologies used by your teams. Our recommendations guarantee secure systems, protected against hackers, cybercriminals, and other malicious actors. Request a security check for startups—receive a health check, an IT security audit, and a prioritized roadmap.
Concrete challenges at this stage of growth
Your growth dynamic is rapid, often unbalanced between technology and governance. Yet, as soon as you store data, access the cloud, recruit your first developers, or target a major account, cybersecurity becomes a lever for credibility as well as continuity.
Cloud and Dev access to be structured
Formalize MFA best practices, roles, secrets.
Product safety to be promoted
Anticipate customer audits, penetration tests and due diligence.
Prepare for regulatory scalability
Putting in place the building blocks of compliance without hindering innovation
A rapidly evolving tech stack
Maintaining security consistency despite agility.
Need for operational visibility
Gain in detection and monitoring without building everything from scratch.
Make the team an active participant in security
Establish good daily habits.
Structuring security in an agile way
Establish a simple framework, adapted to your pace
Known vulnerabilities that need to be addressed
Prioritize and track progress in each sprint.
What this course allows you to pilot
Strategy & Governance
Proposed actions
Mini-ISSP, security charter, Cloud/Government alignment
Business value
Structure a minimum security framework, shareable with the executive committee or investors
Risks & Compliance
Proposed actions
GDPR flash audit, IDD review / calls for tenders
Business value
Clarify your regulatory and short-term customer exposure
Architecture & SecOps
Proposed actions
IAM/Cloud review, backups, MVP/API pentest
Business value
Securing the cloud/product infrastructure with quick wins and key configurations
Cyber Defense Operations
Proposed actions
EDR/SOC starter on 3 to 10 stations
Business value
Gaining immediate detection capabilities adapted to the startup context
Incident & Crisis
Proposed actions
Incident response on demand (hotline)
Business value
Knowing who to call, how to react, without having to build everything from scratch
Resilience
Proposed actions
Assistance in formalizing a cloud business continuity plan
Business value
Prepare for a minimal recovery in case of an incident, strengthen credibility
Cyber culture
Proposed actions
Awareness-raising for founders and employees (sessions / e-learning)
Business value
Create a safety-conscious dynamic within your team from the very first months
This route is ideal for:
Startups in pre-funding or Series A/B funding
Startups in contact with industrial partners/clients or large accounts
Scaleups in the process of obtaining certification or developing security structures (ISO 27001, CyberScore)
Deeptech, data, medtech, fintech, trust-tech ventures…
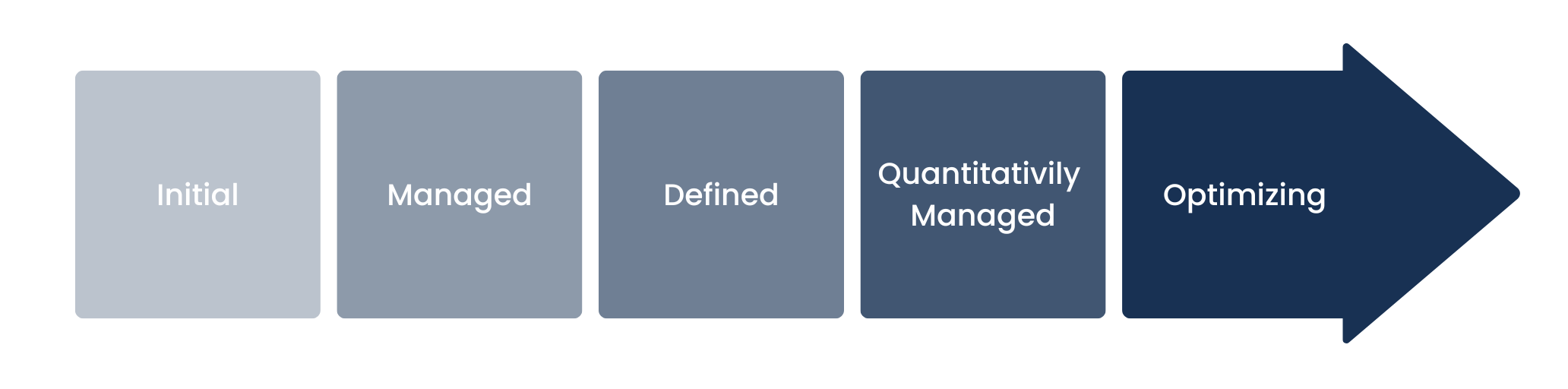
Target maturity level
Startup/Scaleup Course Content
Initial assessment and evaluation
- Healthcheck Flash: Current Practices and Exposure
- Identifying critical points and "quick wins""

Building blocks of security
External SOC "Foundation""
Cloud detection, bypassed MFA, shadow IT, risky logins
Agile security management
Identify the right piloting reflexes without overloading: roles, responsibilities, safety roadmap.
Code and chain security
Analysis of Dev practices and tools (Git, CI/CD, secrets management) to anticipate risks.
Product Pentest
In black box or grey box mode + remediation
Safety awareness upon arrival
MFA awareness / phishing / Slack and email leaks
COMEX Security Point
Strategic reporting focused on fundraising, client audit or internal governance
- To enhance your credibility with funds, prospects or partners
- Reducing GDPR & customer legal risks (VI, leaks)
- Integrating security into Dev and Cloud workflows
- Responding to security/due diligence questionnaires
- Start structuring your organization to achieve ISO 27001 or CyberScore certification.
A pragmatic approach, designed for your context
Situation encountered
- Security treated in a diffuse manner
- Measures implemented on a case-by-case basis
- Isolated technical inspection points
- Lack of transparency in governance
Our contribution
- A clear, structured direction, aligned with the real challenges.
- A gradual, prioritized, and managed trajectory
- Overall consistency: Cloud, Dev, workstation, access
- Concrete, planned and traceable actions
Practical details
Duration
3 to 12 months depending on modules activated + possibility of recurring support
Delivery method
packaged plans or tiered deferred activation
Areas covered
AWS, Azure, GCP, GitHub, GitLab, Auth0, Okta, etc.
Ready to Strengthen Your Cybersecurity?
Don't let threats catch you off guard. Discover how our program can secure your organization.