Drive your Threat Intelligence with a unified platform that is actionable and integrated with all your cyber functions.
Do you have a centralized, contextualized, and collaborative repository to leverage Threat Intelligence in all your security operations?
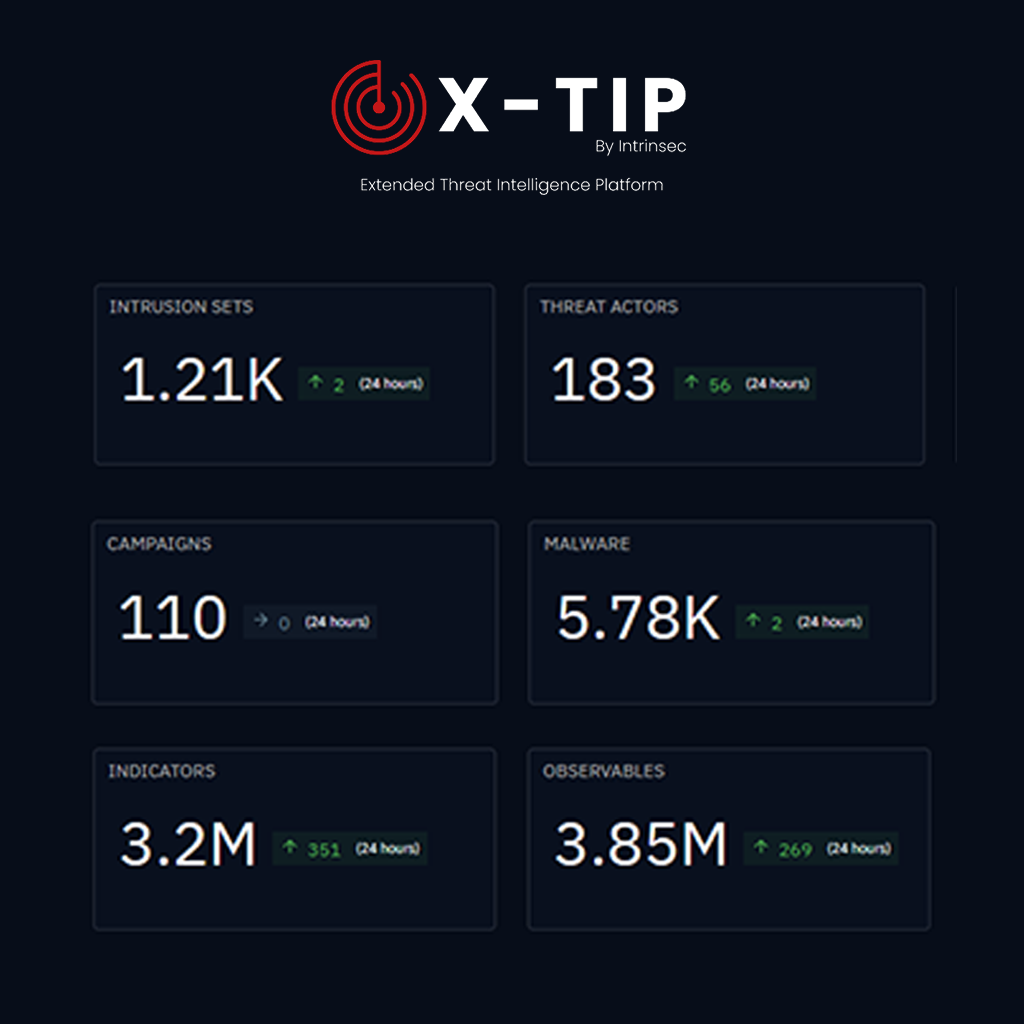
X-TIP centralizes intelligence to strengthen the IT security of your information system. The platform improves the security of IT environments and protects connected IT systems. It allows you to assess the security level and digital security of your information systems and guide your cybersecurity strategy. X-TIP correlates CTI and SIEM logs to detect cyberattacks and accelerate security incident management. Through risk analysis, you prioritize vulnerability remediation to reduce IT risk. Dashboards expose sensitive data and unsecured assets to secure your infrastructure and plan security measures. The solution provides encryption and cryptography recommendations to protect communications and data at rest. Native connectors integrate scanners, EDR, and CMDB to power IT system mapping. Actionable intelligence facilitates audits and security audits by producing traceable and usable evidence. X-TIP helps CIOs formalize IT security policies and appropriate operational policies. SOAR playbooks automate incident response to limit the impact of hacking and cybercriminals. The platform guides the selection of security solutions (SIEM, XDR, EDR) based on the business context and scope. Integration strengthens system security and the security of information systems in production. Scenarios replicate hacking attempts and malicious techniques to test your defenses. Indicators assess the security level, system security, and SOC maturity against sophisticated attacks. X-TIP supports ANSSI and CNIL compliance by providing tailored reports for regulatory audits. Risk management is simplified through a dynamic matrix linking threat, impact, and probability. Recommendations include concrete security measures: hardening, segmentation, and strong authentication. Our CTI analysts leverage active threats to reduce the attack surface of connected systems. The platform orchestrates system security by managing patches, patching campaigns, and post-remediation validations. X-TIP alerts on security incidents and documents attack chains to accelerate operational remediation. Reports demonstrate information security to steering committees and the CIO with metrics and evidence. By combining CTI and orchestration, the solution limits exposure to cybercrime and exfiltration scenarios. Request an X-TIP demo to assess your security posture, schedule audits, and define a security roadmap.
The full power of OpenCTI, boosted by our exclusive feeds and the expertise of our analysts


An integrated, collaborative, interoperable vision
X-TIP is based on the provision and management of a managed OpenCTI By Filigran platform, enhanced by actionable intelligence from Intrinsec: data structuring, cross-component exploitation, governance, and business-driven management.
Increasing complexity and evolving threats
From reaction to anticipation: Staying ahead in the cyber threat landscape
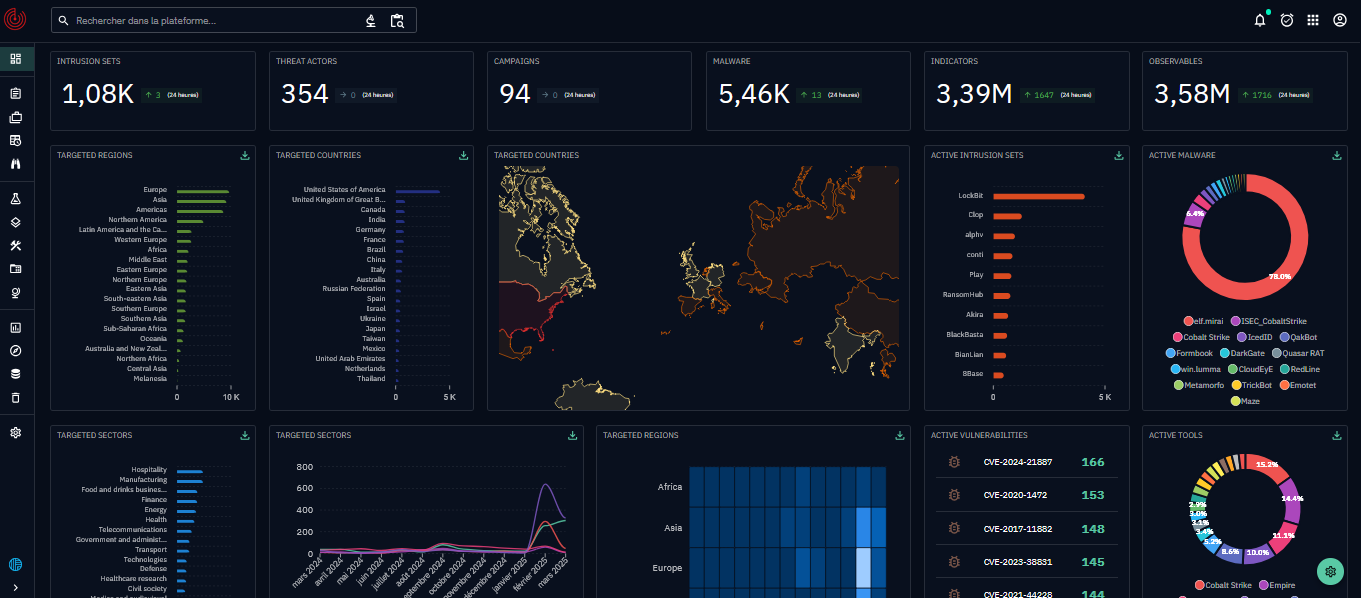
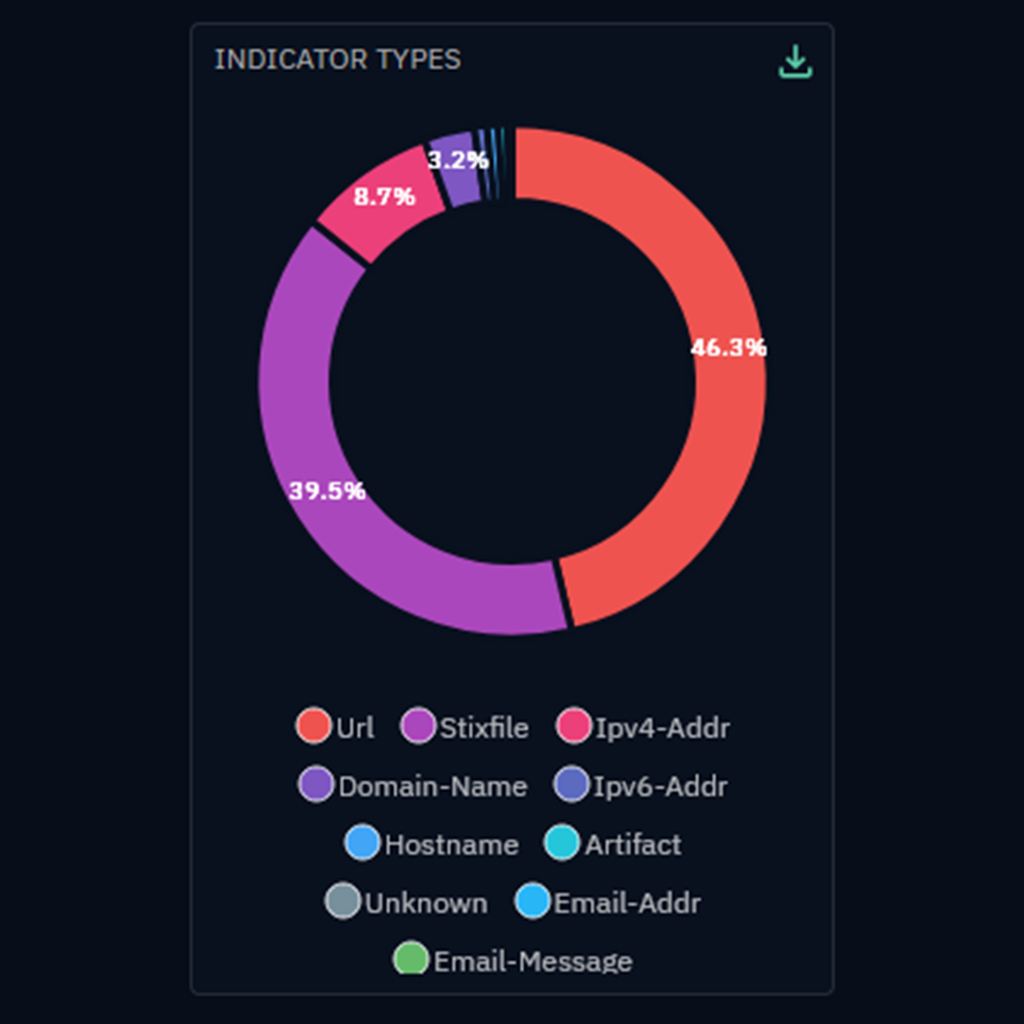
Visualize and gain a deep understanding of the threat landscape
Thanks to X-TIP, you can access:
- An enriched sector-specific knowledge base through Intrinsec's expertise, incorporating the latest trends, attack groups and observed techniques
- Dynamic and interactive dashboards to explore and map the threats relevant to your domain
- Analytical reports to inform your long-term cybersecurity strategy
Benefits:
- A clear view of the most active threats and adversaries in your sector
- Immediate understanding of the tactics and methods used
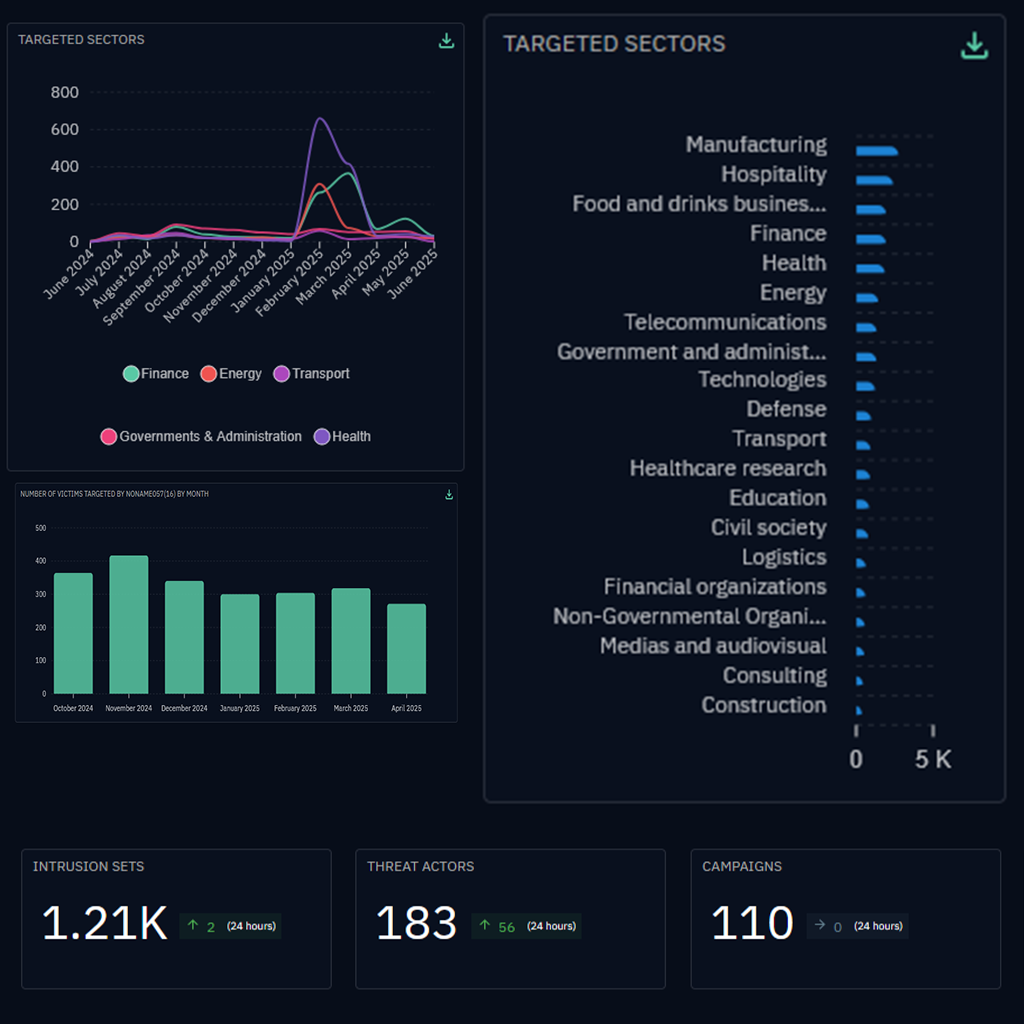
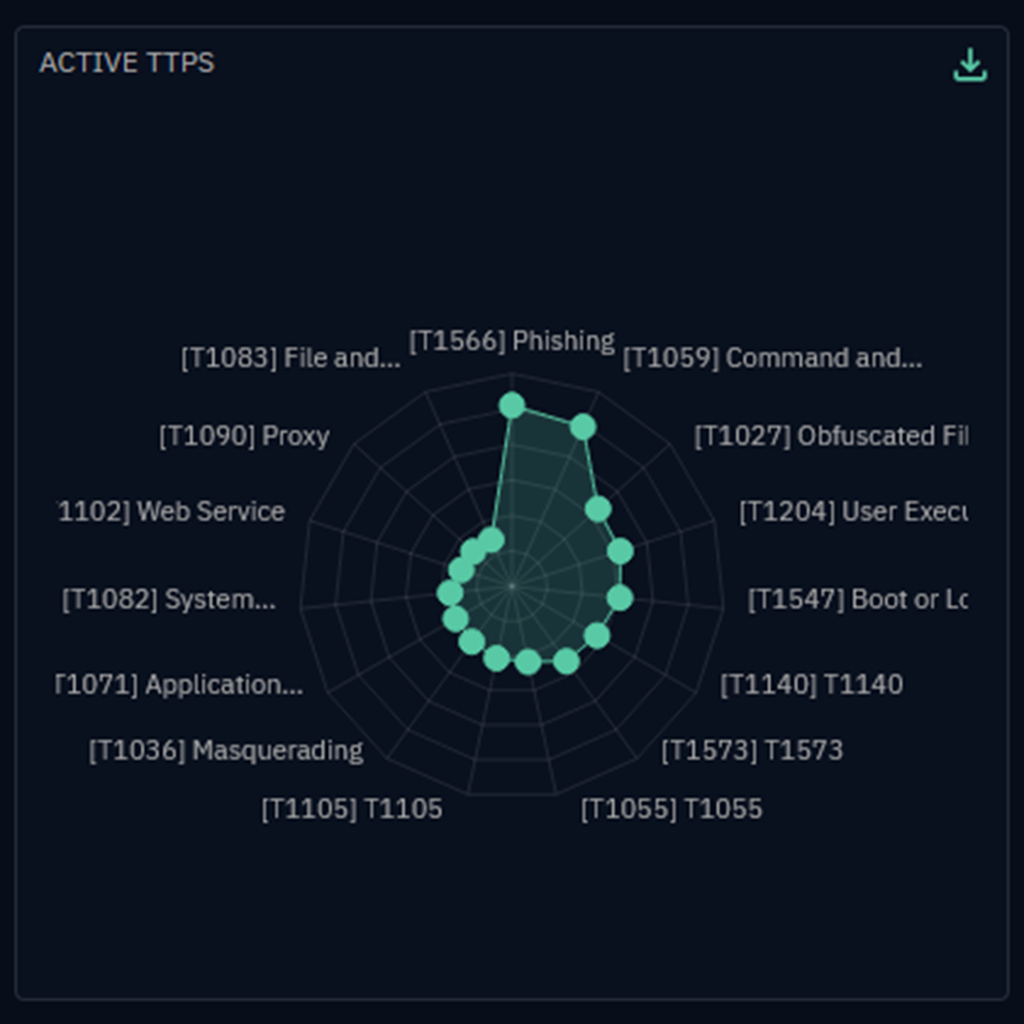
Access actionable CTI feeds that your teams can use.
X-TIP offers you:
- A continuous stream of qualified indicators of compromise (IoCs), directly derived from Intrinsec investigations (certified by our experts)
- Structured TTPs and technical markers according to market standards (MITRE ATT&CK, STIX2…)
- Ready-to-consume content: integration into your existing tools (via OpenCTI) or automated integration using our APIs
Our services include:
- Effective prioritization of your SOC treatments and advanced detection
- Noise reduction through selected and contextualized data by sector
Easily manage and enhance your cybersecurity posture
With X-TIP, equip yourself with:
- Custom dashboards for your steering committees or communication to management
- Ready-to-use monthly or sector-specific reports for your governance bodies
- With complete interoperability: exportable feeds and customized consumption (tables, APIs, files)
Benefits:
- Factual support for strategic decision-making
- Documented evidence for management, business units, or compliance
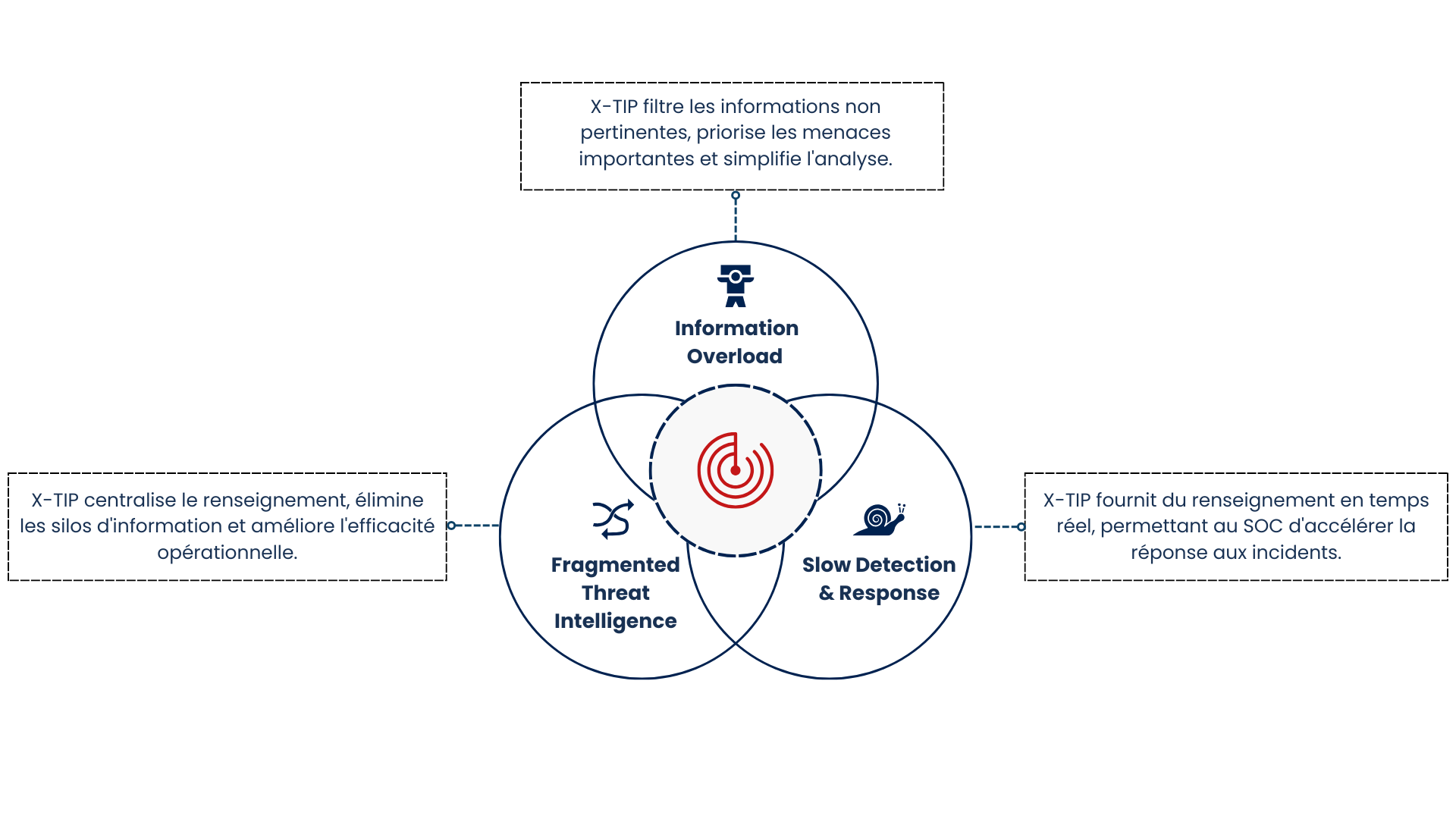
The challenges of cybersecurity?
Increasing complexity and evolving threats
We take a comprehensive approach to detecting external threats that typically elude traditional tools. By analyzing your industry-specific threat landscape, we identify early warning signs and indicators of compromise that conventional EDR/XDR/SIEM/SOAR solutions cannot detect on their own.
Lack of visibility on external threats
Using advanced threat intelligence, event correlation, and behavioral analysis technologies, we offer unparalleled visibility into external threats targeting your organization. Our approach goes beyond traditional perimeters to identify risks before they reach your infrastructure.
Strengthen your cyber posture
with the X-TIP Solution
Our mission is to transform threat intelligence into concrete and effective actions. We enable security teams to detect the threats that truly matter more quickly.
SIEM Integration
Automated correlation of SIEM logs with up-to-date threat intelligence feeds, significantly reducing excessive alerts and false positives.
EDR/XDR Enhancement
Extend the visibility of your EDR/XDR solutions through the integration of intelligence on external threats (dark web, APT, CVE, etc.).
SOAR Automation
Enrich your SOAR playbooks by directly adding indicators of compromise (IoC) or technical intelligence, to automate your response scenarios.
Rapid incident detection
Accelerating incident detection through the integration of early warning signals from external sources.
More details
Improved quality of alerts and responses through advanced contextualization of detected threats or risks.
Advanced features of the X-TIP offer
multi-source ingestion
Automated collection from numerous internal, external, open source, dark web, etc. sources.
Standard modeling (STIX 2.1)
Structuring and enriching threat data in international format.
Flexible querying and search
Advanced querying to find, cross-reference and pivot on critical entities or events.
Secure distribution and sharing
dissemination of relevant intelligence to your teams, business tools or partner ecosystems.
RFIs (Request For Information)
On-demand investigation service for any IoC, threat or campaign.
Sector notes and dedicated analyses
Production and integration of contextualized reports by sector and target audience.
PhishTrackr integration
Proactive monitoring of phishing infrastructure targeting your organization.
Interactive dashboards
Customizable dashboards to view real-time cyber exposures, trends, threats and KPIs.
Improve your SOC's detection capabilities with a Cyber Threat Intelligence-based strategy
Interested in discussing X-TIP activation?
Our all-in-one Threat Intelligence solution strengthens your SOC with actionable, real-time intelligence.