From VPN Compromise to Ransomware: 5 Real-World Incident Response Scenarios
Context
Depending on the threat actor you are dealing with, the answer to that question might differ: Initial Access Brokers (IAB) will often step down in favor of other attackers as soon as they have achieved access theft. Ransomware operators would go straight to their goal: exfiltration and encryption. Advanced Persistent Threat on their side might answer as far as we can without being spotted.
As many VPN appliances, by their very nature exposed on the Internet, are subject to vulnerabilities and poor configuration (lack of MFA, legacy accounts, weak password policy, etc.), the challenge is to prevent threat actors from exploiting these flaws and, if they do, to prevent them from carrying out their attacks. It can be very complex due to number of factors: vulnerabilities being exploited well before publication, editors not releasing patches immediately, bypassing of these patches, lack of information related to the vulnerabilities, lack of monitoring of vulnerable devices, etc.
Besides, compromises of this nature do not only concern devices in production at the time vulnerabilities are published, but also all legacy devices that are often less or not monitored. For instance, when deploying a new instance, system updates must be applied as well as security patches. Otherwise, the new instance might be up-to-date but vulnerable.
We will present, in this paper, five cases encountered several times by CERT Intrinsec, during its incident response engagements, which highlight the weaknesses observed and potential solutions to prevent this type of situation.
CERT Intrinsic presentation
CERT Intrinsec is a French incident response team that performs its operation mainly on the French sector. The team deals with about 50 major incidents per year and works to help its customers to recover from cyber-attacks and strengthen their security. Since 2017, CERT Intrinsec has responded to of hundreds of security breaches involving companies and public entities. The majority of those incidents are related to cybercrime and ransomware attacks with financial objectives, hence, CERT Intrinsec follows those groups activities and generates comprehensive intelligence from the field. ANSSI (French National Security Agency) granted CERT Intrinsec PRIS (State-Certified Security Incident Response Service Providers) certification. The latter testify that CERT Intrinsec meets specific incident response requirements, using dedicated procedures, qualified people and appropriate infrastructures.
How far will the compromise take us?
As the patch cycle differs from a company to another, each of them may find themselves in different situations when it comes to VPN compromised. All of the scenarios below describe these situations.
Scenario 1 – Vulnerability monitoring and early compromised assessment
In the best-case scenario, the security team monitors vulnerabilities, especially on exposed devices, is able to Run update and patch quickly and is able to perform investigation on its own devices. Besides, it follows the editor's publications to monitor measures taken to mitigate the vulnerability.
Finally, it is able to conduct threat hunting on its information system to look for indicators of compromise related to vulnerabilities post exploitation. They ask from time to time a compromise assessment to its security service provider.
The key here is the ability to take action as fast as possible and deal with the three main locks when it comes to security: human (not enough people to monitor information system and vulnerabilities), budgetary (not enough money to conduct a compromised assessment or to replace a piece of device) and procedural (no clear division of tasks and roles).
Scenario 2 – Exploited appliance and early remediation
In this case, the vulnerability issue is handled but with a little delay. Thus, exploitation attempts might have been conducted on the device. When the security team realizes that the vulnerable appliance could be compromised, it would conduct compromised assessment not only on the device, but on the perimeter accessible from the appliance as well, to verify if any post exploitation actions are taking place.
It should look for multiple kinds of evidence, including system compromised, suspicious or malicious network flows, either internal or external, but also suspicious accounts used by or on the compromised appliance.
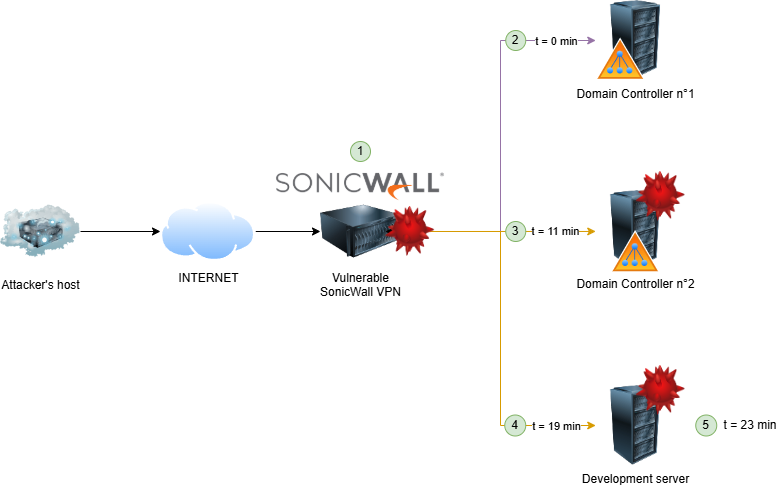
Scenario 3 – Discovery and lateral movement time
Post-exploitation is underway. The SonicWall VPN appliance affected by multiple vulnerabilities has been compromised and the attacker created two local accounts on it (1). He then tried to connect to multiple servers using compromised accounts (2), he used PsExec tool to test its access to a first domain controller (3). Later on, he moved laterally using Remote Desktop Protocol (RDP) to a development server (4). Finally, he used systeminfo command to gather information about that same server (5).
All the malicious actions were carried out in less than an hour. The compromise was discovered by detecting the use of PsExec tool on the domain controller. Containment actions were taken quickly and digital forensic investigations were undertaken to find out the extent of the compromise.
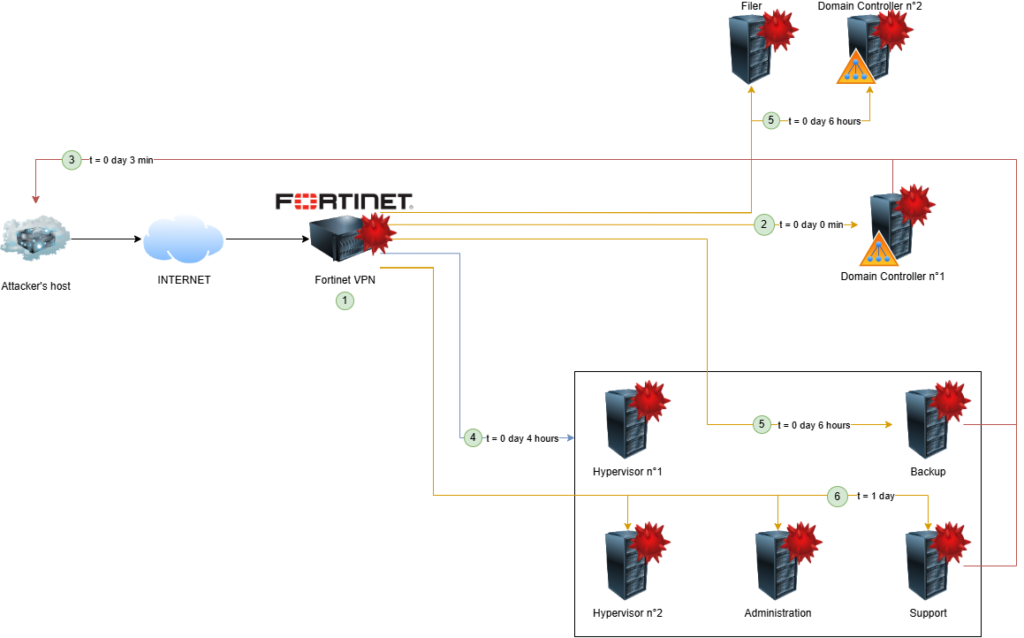
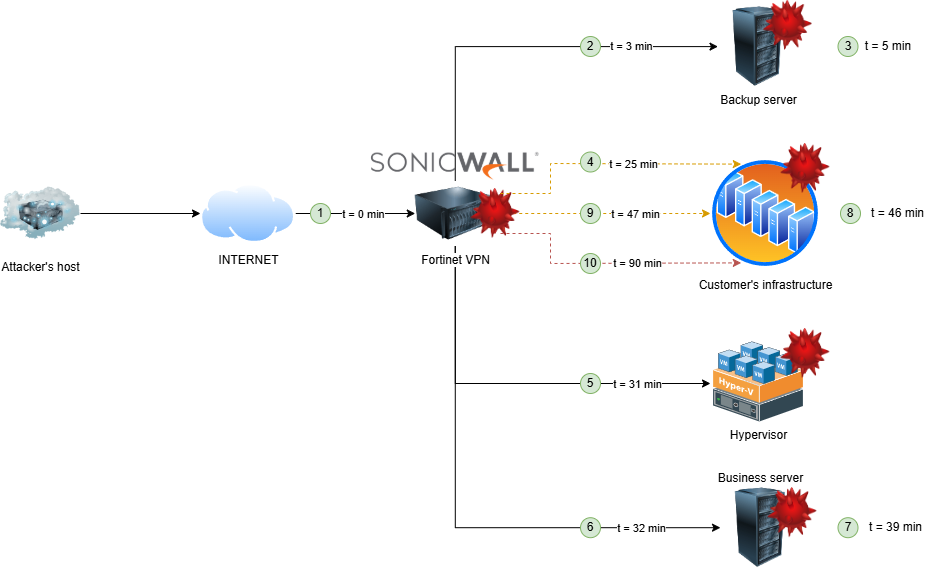
Scenario 4 – Credentials collection party
Can we go further? Here comes credentials harvesting and large-scale compromise.
In this very case, the threat actor first exploited the CVE-2024-55591 Fortinet vulnerability (1). This vulnerability allows an attacker to bypass authentication of FortiOS administration interface and to gain administrator privileges by sending crafted queries to the websocket module.
Three months later, as a Security Operation Center (SOC) was being deployed, multiple alerts were raised about potential data exfiltrations.
We found out that the attacker connected to the network using a compromised account through the Fortinet VPN and accessed to the primary domain controller (2) via Remote Desktop Protocol (RDP). Within 3 minutes, he dumped Active Directory NTDS database and exfiltrate it to his remote server (3). He then disconnected 6 minutes later.
Four hours later, the attacker came back and performed a ping scan on a specific network range from his VPN session (4). He then waited two more hours before starting to connect to multiple servers: domain controller, filer, backup, etc. (5). He collected registry hives on the backup server.
On the next day, the threat actor continues his credential harvesting process by repeating it on hypervisors, administration and support servers (6).
Two days after the start of post exploitation actions, the alert is raised and containment measures are applied on accounts, servers and networks.
Scenario 5 – From weak VPN to ransomware attack
The worst-case scenario is the compromised or use of the VPN appliance compromised leading to ransomware attacks.
In this case, the attacker was able to get a VPN session using a compromised account. (1) He then connected to a VEEAM backup server and exploited the CVE-2024-40711 deserialization vulnerability (2) and thus, created a local account on the server (3). After ensuring its persistence, he scanned network shares and devices from his VPN session (4), writing the results in text files.
He then decided to move laterally to two different servers: an hypervisor via Remote Desktop Protocol (RDP) using a compromised domain administrator account (5), and a business server where he not only added another persistence (6), installing AnyDesk solution, but also installed RClone cloud synchronization tool in order to exfiltrate data (7).
Finally, he browsed network shares and folders (8), before listing hypervisors and virtual machines (9) available on the information system and deploying his ransomware binary (10).
It is important to state that VPN compromises are not only due to vulnerability exploitation but also to weak configuration (authentication flow, password policies, multi-factor authentication, local accounts, etc.). For instance, we came across a case where an attacker was able to authenticate with any of VPN group names, as an identifier, without needing any password.
Insights about hardening and configuration
As we saw in these five cases, lack of security allows threat actors to go even further in their attacks. It is possible to increase the level of security to avoid or prevent these attacks. Regarding the exploitation of vulnerabilities on VPN appliance, it is possible to build an efficient patch management along with a monitoring process that enables the most critical vulnerabilities on the most important devices to be identified as quickly as possible. As editors might not release patches right away or the latter might be bypassed, it is important to monitor the evolution of interesting information related to critical vulnerabilities (editor's solutions, indicators of compromise, hunting opportunities and so on).
There are more common ways to reduce the attack surface. First, avoid exposing administration or management interfaces to the Internet prevents attackers from exploiting vulnerabilities leveraging these interfaces. Multi-factor authentication (MFA) is the cornerstone of remote access security. Indeed, some kind of vulnerabilities, like CVE-2019-13379, allows attackers to get access to credentials, but you can prevent them from accessing your network if MFA is implemented. Besides, threat actors can end up with stolen credentials, that they can use on VPN appliance, from several sources (leaks, credentials stealers, phishing, etc.).
If an attacker breaks into your network, you can make his job harder by reducing user privileges to what is strictly necessary and review accesses on a regular basis. You should delete as well local legacy accounts on VPN appliances that are not used anymore, to prevent an attacker from using it.
Finally, you can set up Geo IP restriction on your VPN appliances and set strong password policies, both locally and with all other authentication methods (Active Directory, etc.).
Insights about monitoring
When it comes to monitoring, we think first of indicators of compromise (IOC) available, either from the editor or from security research companies. These IOCs can be linked to the vulnerability exploitation itself or to intrusion sets operated once vulnerability has been exploited.
More specifically, by monitoring system logs, you will be able to detect suspicious account creation, group change, unusual connections and so on.
During few CERT Intrinsec incident response engagements, companies were in the process of migrating from one VPN solution to another. Sometimes, this process takes quite a long time and legacy instances remain up even if they are not used anymore. It is important to keep an up-to-date inventory of exposed equipment. Year external assets security monitoring (EASM) can be useful to identify overlooked devices or solutions that might be vulnerable.
Finally, it is essential to continue monitoring after patching, and to reset or rebuild appliances because patches may be subject to bypass.
Insights about investigation
When Security Operation Center (SOC) or local security team finds some evidence of VPN appliance compromised, it might request a compromise assessment on the impacted perimeter.
The incident response team should already be aware of that vulnerabilities and able to conduct forensic investigations. Tea knowledge is based on editor's publications, proof of concept, previous commitments related to the same vulnerability, indicators of compromise from post exploitation intrusion set, researches on forensic artifacts or specific logs and how to exploit them, closed sources, etc.
Not to forget that the assessment should not only rely on forensic data collection, but should take advantage of all the security and monitoring solutions available on the perimeter (SIEM, EDR, XDR, cloud consoles, etc.). The availability of the network logs is often a weak spot when conducting forensic investigations. That is why you should make sure that these elements are properly stored, accessible and usable.
When it comes to VPN appliances, resources available to investigate can vary a lot. You should then rely on editor's documentation, available command lines and diagnostic tools (Internal and External Integrity Checker (ICT) for Ivanti, Tech Support File (TSF) for Palo Alto, etc.). You should check as well configuration, users, groups, network rules and so on.
Finally, it is important to analyze areas of the information system that are accessible from a VPN session or from the device itself, depending on the incident, performing system and network analysis.
Insights about rebuilding
Finally, if post exploitation has been going on after vulnerable exploitation, some containment and remediation actions must be taken, sometimes quite substantial. It is possible to prepare these actions by having a new information system core ready for reconstruction with virtual machine templates, backups, spare domain controller and hypervisor.
In any case, it is very important to conduct forensic collection process before any remediation actions impacting evidences, otherwise the compromised assessment will not be possible.







