Cyberattack detection: the importance of adopting a qualitative approach
In macroeconomics, it is sometimes said that a crisis at least offers the advantage of putting an end to structural imbalances; while it seems complicated to call the current increase in cyberattacks a "crisis," given that this development has been predicted for years, this trend has at least led to a genuine paradigm shift:
No organization dares to doubt its vulnerability to cyberattacks anymore.
No executive would be confident anymore about the risk of ransomware being deployed on their company's information system.
For those who remember the days when cybersecurity specialists were all considered paranoid, the current situation is undoubtedly better. Yet, this phase of denial regarding cyber risk is followed by a new one: an inflation of services, providers, technologies… and contracts. Does this make sense from an operational standpoint? Are we better protected simply by being (quantitatively) more protected? An attempt at an answer.
Multifaceted threats, innovative attackers… but anticipated scenarios
In December 2020, the SolarWinds affair was making headlines ; not only that of the specialized media, such as Stuxnet in its time, but also that of general practitioners. We will not go into the details of this attack: an American software publisher, SolarWinds, had been compromised, and revealed that’a diseased version of one of its "flagship" products, Orion, had allowed the attackers to compromise a plethora of clients in a cascading fashion of society worldwide.
While the cyberattack, now bearing its eponymous name, is impressive due to the potentially immense scope of its compromise and some of its victims (such as US government agencies), is it truly unprecedented? Was its unfolding scenario unusual?
No. In fact, it has been known for years by specialists in the field as...’attack on the« supply chain », and rests on a relatively simple assumption: it is often easier to compromising a supplier of one or more end targets, the latter benefiting from privileged access, rather than attacking head-on structures that are sometimes extremely well defended.
So, The offensive scenario on which the SolarWinds case is based is not inherently original.. Would SolarWinds' customers have avoided a compromise if they had used multiple security solutions, providers, and services? It's highly doubtful.
However, many risk analyses have made it possible to identify the risk posed by an offensive scenario "like SolarWinds", and potentially to take measures to deal with it.
Managing by risk, rather than reacting to the latest news
For a customer, it is sometimes tempting to give in to the temptation of always wanting more, as this offers a certain intellectual comfort: for a Security Operations Center (SOC), this has historically resulted in a voracious appetite for detection rules deployed in a SIEM.
A new cyberattack? A new detection rule. A publisher's report on a new modus operandi? A new detection rule. The same key for every new lock. But while this may be reassuring, while it gives the impression of action, the customer is actually no better protected.
In the case of SolarWinds, a "classic" approach responds as follows:

If reacting only allows us to deal with the incident in question, what about similar scenarios, but targeting another service provider and/or presenting different technical characteristics?
Some actions within the quantitative approach to cyberattack detection may, potentially, detect and perhaps block these other incidents, but this is far from certain, because what is being addressed is less the risks of a comprehensive offensive scenario than its latest manifestation after its emergence. Even worse: Piling up detection rules developed hastily and based on current events risks saturating the detection capabilities of a SOC. (more alerts, more false positives, less time for analysis).
A qualitative approach to cyberattack detection, such as the one practiced daily by Intrinsec, does not present this operational hemiplegia; indeed, by leveraging existing methodological tools, such as’EBIOS Risk Manager, The system ensures that cyberattack detection is based on offensive scenarios, which are translated into feared technical events. Once these are defined and prioritized, it is possible to answer the question "Am I adequately protected?" by assessing the coverage of the associated risk.
In the case of SolarWinds, a qualitative approach provides the following answer:
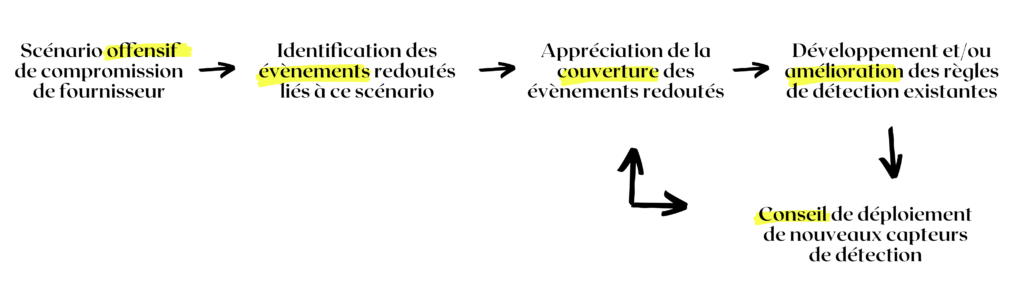
Offensive vendor compromise scenario: Identification of related feared events (e.g., malicious use of existing access, dissemination of malicious code); Assessment of feared event coverage; Development or improvement of existing detection rules and/or advice on integrating new detection sensors
The advantages of this qualitative approach to cyberattack detection are that it does not depend on the irruption of news to ensure that the right questions are asked, and that it allows the strategic to feed the operational, and the detection to anticipation.
And now ?
It is clear that decision-makers with a global vision, and/or CISOs, faced with this risk-based approach to cyberattack detection, very quickly perceive its benefits, if they have not already adopted it.
However, the temptation remains significant to see a new technology or solution monopolize the attention of even the most seasoned cybersecurity experts. A taste for tools (especially new!) combined with a certain technological solutionism is almost inherent to the cybersecurity sector!
This bias, combined with the tendency to compartmentalize activities, both operationally and strategically, undermines cybersecurity.
However, many fictitious boundaries between professions tend to disappear,Qualitative analysis is gradually replacing quantitative analysis, and anticipation improves detection, which in turn enables a rapid response.. So, while the future is certainly not rosy, at least it looks exciting!







