Threat Intelligence against online payment fraud
According to a report by the Bank of France[1], Payment fraud in France is estimated to have represented 1.182 billion euros in 2019, This represents an increase of 13% compared to the previous year. This fraud is largely perpetrated via payment cards, which account for 39% of the total fraud, corresponding to an amount of 470 million euros. Only fraud via The checks represent a larger volume of 46%.
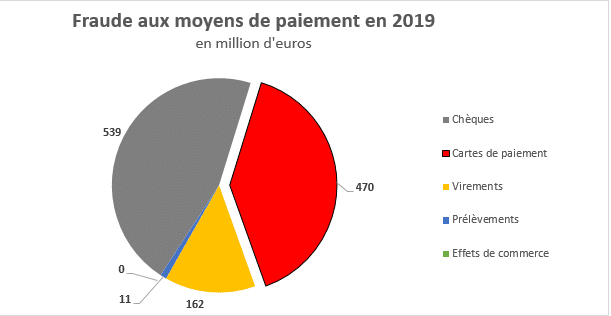
While unpleasant for individuals, fraudulent payments are usually reimbursed by banks. As for merchants, they do not bear losses related to fraud as long as they act in good faith towards their bank. Indeed, the law mandates that the payment service provider reimburse the victim.[2]. Thus, they are essentially the banks that bear the losses.
There Intrinsec Cyber Threat Intelligence invites you to discover how cyber intelligence is an essential specialty in a world where the digital universe plays a growing role, and particularly helps to combat fraud, especially in the field of payments.
This is the type of fraud, via Payment cards, which we invite you to explore in this article, offer a unique glimpse into the networks involved in illegal activities. During this article, we will examine several key points:
- How fraudsters specialize to facilitate the success of an unauthorized payment.
- The commercialization of bank fraud and the normalization of the use of stolen payment cards.
- What Cyber Threat Intelligence can contribute to effectively combat online payment fraud.
- New two-factor authentication systems and ways to bypass them.
How does Cyber Threat Intelligence gain access to the organized world of bank fraud?
The specialization of fraud perpetrators
The world of online banking fraud is a market composed of independent actors specializing in specific tasks. Indeed, this type of fraud is relatively complex, as numerous actions must be carried out to complete a fraudulent payment. These tasks can be divided into four main categories of activities, each corresponding to a specific area of expertise:
- Bank data theft
- Bank data trafficking
- The fraudulent use of bank data
- The creation of false documents
There are many techniques used to steal information stored on payment cards:
- THE phishing or phishing
- THE SMiShing which is the SMS version of phishing
- THE web skimming[3]
- THE skimming classic
- The compromise of a website storing payment card numbers
- Misappropriation by dishonest telesales agents
- The collection of numbers by cashiers or shopkeepers
- Etc.
Accomplished via these various techniques, the theft of banking data by malicious actors constitutes the first step in bank fraud. More specifically, the phishing This involves making the victim believe they are communicating with a trusted third party in order to trick them into transmitting sensitive data, for example through a fake website that mimics the visual identity of a legitimate site. web of well-known e-commerce. As for the skimming, This technique refers to a method that duplicates card data by hijacking a card reader or ATM. The version web This method involves compromising a legitimate e-commerce site so that it transmits a copy of the bank details entered by users during the payment phases.
Some internet users, and even e-commerce platforms, also offer to the sale of stolen data (see below).
L'’fraudulent use of information from a stolen payment card, also called carding, Furthermore, it requires the use of various techniques, which may lead to the use of suppliers of counterfeit or stolen documents. A false identity or the impersonation of a real identity can thus allow someone to open an account on a cryptocurrency exchange. More generally, withdrawing money from a payment card is commonly called « Cashout ».
These document vendors promote their products on various forums on the Surface or Dark Web, as well as on social media. These providers typically offer real or fake identity documents, selfies, and proof of address.
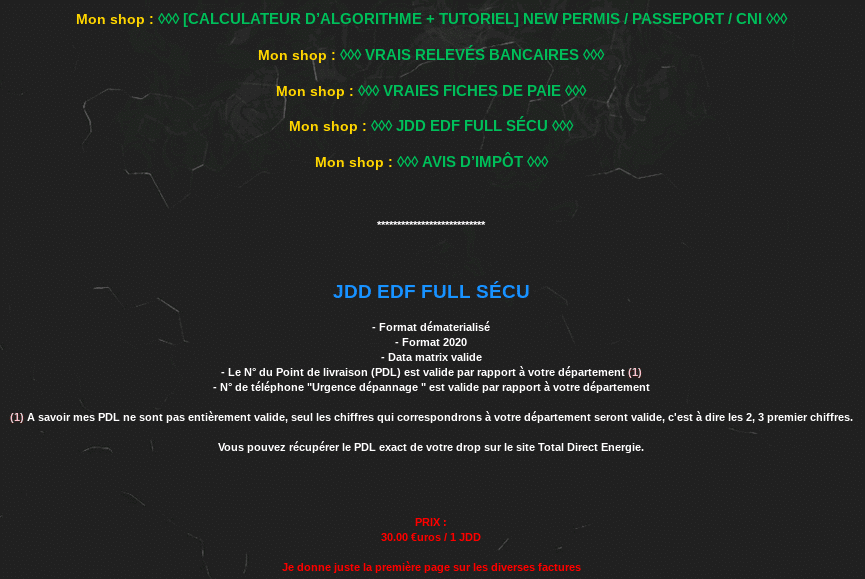

The most sophisticated vendors even offer to use their own fake document generators.
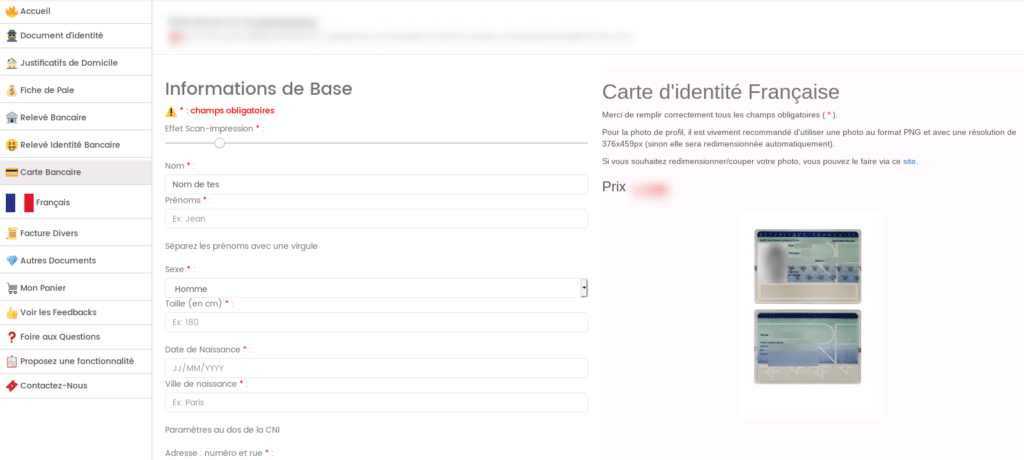
Finally, it is worth mentioning the "« users » purchasing these services and products in order to carry out fraudulent transactions. The law provides up to 7 years imprisonment and a fine of 750,000 euros for anyone participating in online banking fraud[4]. However, those who carry out fraudulent transactions take the most risks because they are the most exposed and can be unmasked.
Just as cosmetics sellers share makeup tutorials, banking data sellers offer tutorials on "« carding »", an unlawful use of a payment card, in order to incite fraud.
There are mainly two methods for recovering money with stolen banking data. Either by buying products that can be easily resold, by having them delivered via dead mailboxes, for example. Either by using platforms that allow depositing funds, before withdrawing them or buying... cryptocurrencies. Once these cryptocurrencies Once purchased, the holder of these currencies anonymizes themselves through the use of mixers, or numerous transactions between several wallets allowing identities to be obscured.
An international trade in French banking data
In 2018, the amount of payment card fraud in France reached €470 million, compared to €430 million in 2017. This surge is largely due to development of the trade in stolen banking data. These cards are easily accessible; knowing a few websites makes it easy to buy them using bitcoins or other cryptocurrencies as payment. This data often includes the payment card number, expiration date, security code, the victim's name, address, phone number, and bank name. It can be sold for between €10 and €60 per victim.
For example, consider this Russian Surface Web site called "Cardhouse." Bank cards are for sale and available in over 30 countries. Among the cards for sale are more than 5,000 French cards containing the victim's personal information, such as their contact details, payment card number, expiration date, and security code.
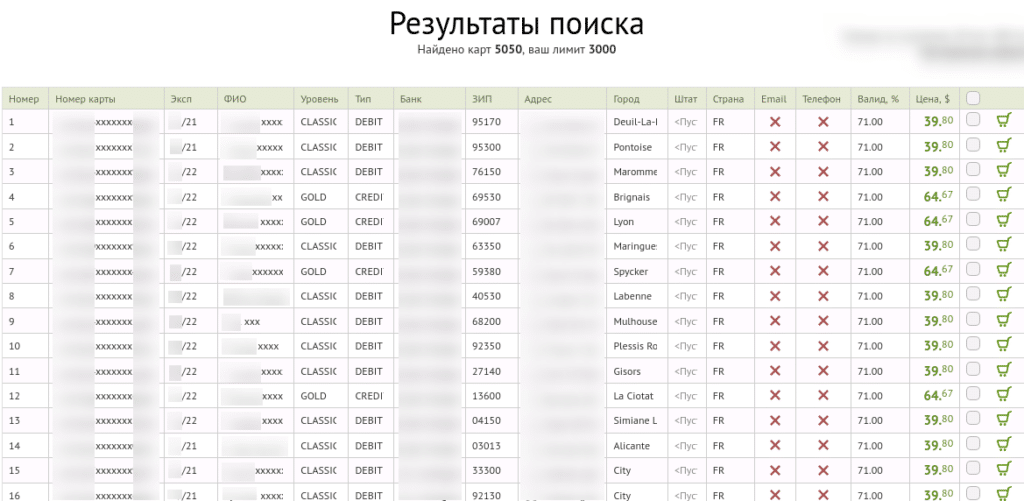
On Cardhouse, partial display of sales data, Providing the first and last digits of the payment card, the expiration dates, and the cardholder's contact information as a sign of good faith builds trust with buyers. Indeed, whether on the Dark Web or the Surface Web, many sellers try to scam internet users by providing them with fake information. The Cardhouse website also indicates the likelihood of payment cards being valid.
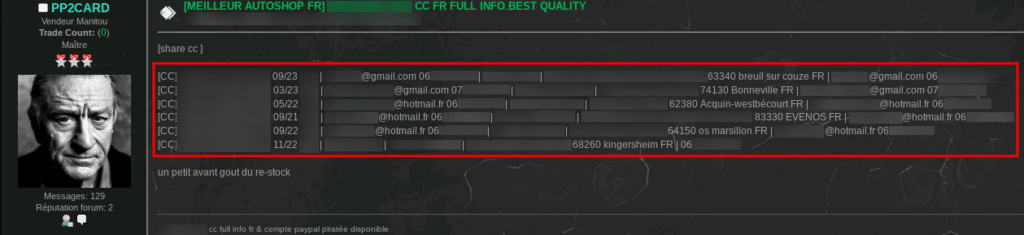
Other internet users, such as "PP2CARD", offer free samples on Dark Web forums to promote their sales sites. The sample below contains six lines of credit card numbers along with expiration dates, security codes, and victim contact information. The idea is to invite forum members to try these credit cards by making transactions in order to obtain positive reviews and build a good reputation in this area.
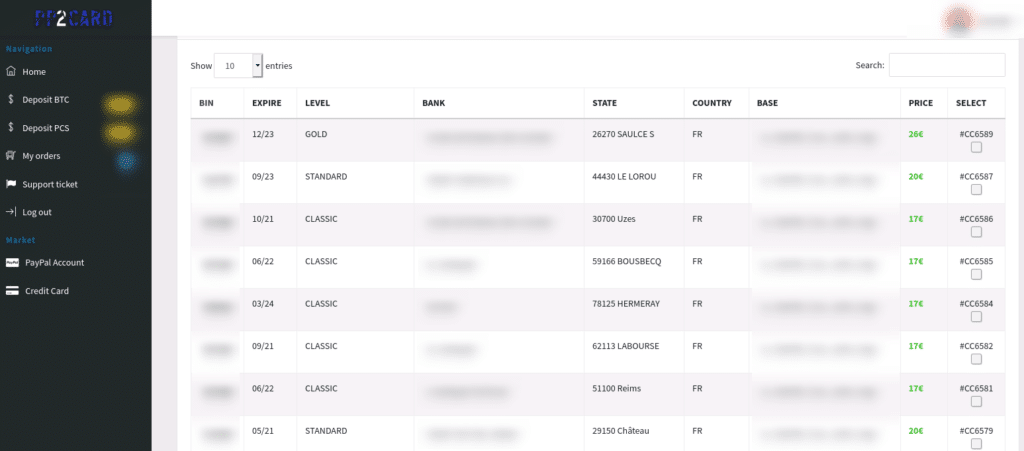
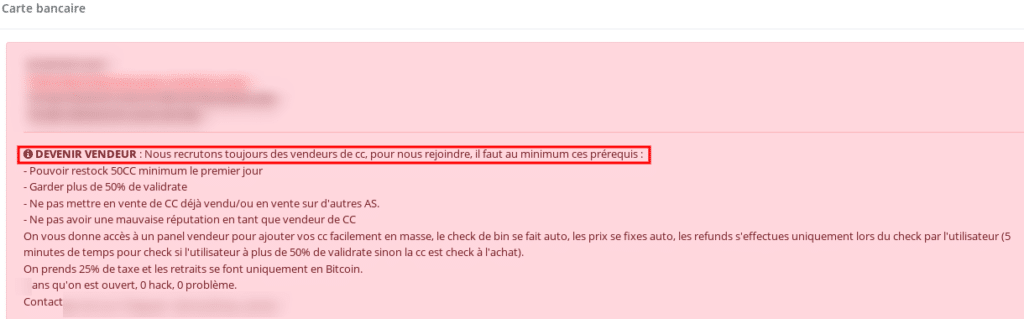
Finally, a relatively famous site in the sale of logs and stolen credentials, Hookshop, seems to have the ambition to become a true marketplace specializing in the sale of payment cards. Hookshop states that it is looking for sellers of bank cards and would take a commission of 25% on each sale. Like other marketplaces, the quality of the products sold would be guaranteed by the sales platform..
These few examples are not the only channels for selling bank data. In reality, there are hundreds, even thousands, in most languages. Regularly, sellers of varying sizes appear on different fraud forums and promote their new sales websites.
According to observations made by Intrinsec's Cyber Threat Intelligence service, this commercial phenomenon appears difficult to counter by simply shutting down sales websites. Indeed, once closed, these sites very often reopen quickly with a new domain name, using a different TLD (.fr, .com, .net, .cc, etc.). This was notably the case with the Wolfshop website, which later became Hookshop. They may also have a mirror site on the Dark Web, a copy of the site accessible via the Tor network.
What additional measures are needed to combat fraud?
Identifying stolen banking data
Because sales are anonymous, and scams are rife in the illegal resale market, credit card sellers constantly try to reassure buyers by partially displaying the data being sold, which allows services such as [service name] to [access the card].’Intrinsec to fight against this type of fraud. Indeed, the displayed extracts may render It is possible to identify stolen banking data., and especially that of the victims, from the moment they are placed on the market. These elements are often sufficient to allow for’alert banking stakeholders of the ongoing fraud attempt. It is also possible to track the status of sales, thanks to an internal identification number provided to visitors on the sales site.
While retrieving data from sales may seem simple, these websites and their owners are far from being as stable over time as legitimate product sales platforms. Indeed, it regularly happens that sites or forums dedicated to this type of fraud are forced to shut down or change their URLs. The lifespan of these fraudulent businesses is relatively short, hence the need to practice a regular monitoring and activity sourcing.
The monitoring team of the service Intrinsec's Cyber Threat Intelligence team is constantly exploring new websites and forums. of the Surface and the Dark Web. These are then regularly monitored as long as they are available. Our monitors also check activity on social networks, such as Telegram.[5], where fraud thrives. Thus, Our service has a relatively comprehensive view of fraud activities, including those related to stolen and resold banking data. Furthermore, Intrinsec's Cyber Threat Intelligence has tools enabling the rapid and widespread identification of stolen data, based on an internally compiled list of sources.
Combating bank fraud by searching for data on sale is a a method to avoid significant financial losses for banks, This is because it's possible to deactivate stolen cards before they can be used illegally. In France, €470 million was stolen through fraudulent payments made using 1.4 million stolen cards in 2019. This represents an average cost to banks of €335 per stolen card. For example, a site like Cardhouse, with 5,000 payment cards available, could... representing up to 1.5 million euros in losses at any given time for banks. However, it's important to note that this calculation assumes all payment cards are valid, which isn't always the case. Card traffickers, on the other hand, are regularly supplied with new data.
Bypassing conventional security measures
THE visual cryptogram The security code on the back of the card is supposed to provide protection against fraudulent use. However, this protection is completely ineffective against data theft using the techniques mentioned above (the phishing or the web skimming (for example). Indeed, in the context of these two techniques, malicious actors retrieve all banking data entered by the victim, including the visual cryptogram.
In order to strengthen the security of this data, the 3D Secure technology was developed to strengthen user authentication. It is a two-factor authentication allowing confirmation of a card payment, which can take the form of a password, date of birth, code sent by SMS, validation from a mobile application, etc. Although supported by banks, the 3D Secure system is not systematically deployed on merchant websites and used by e-commerce merchants and payment processing providers. Indeed, if the European directive DSP2 imposed since 1er January 2021: the near-systematic use of this strong authentication for online payments[6], It only applies to European websites and payment providers. Therefore, online retailers like AliExpress are not included. abandon the use of this security method 3D Secure is required due to the risk of shopping cart abandonment. fraudulent payments, via the lack of strong authentication on non-European websites, are therefore still possible.
Moreover, exceptions are provided for by the directive, similar to payments under 30 euros or trusted beneficiaries, such as a long-standing e-commerce merchant[7]. These exceptions can be exploited. for malicious purposes. Furthermore, New methods of fraud are regularly identified and shared. on forums. For example, a "bible" of the carding 2020, capitalizing on various methods of this type valid for a set of sites, was shared on the Selkis forum.
Finally, strong authentication is not foolproof: fraudulent payments are still possible despite two-factor authentication. This is the case when the strong authentication method is fixed, for example, with the use of an unchanged password. If it is implemented with a code sent by SMS, it can be bypassed using a technique of SIM swapping. This method involves stealing the victim's identity in order to order a new SIM card and receive the one-time codes to carry out the transactions, in place of the victim.
For this reason, the European PSD2 directive aims to make banks more responsible by lowering their lending criteria. the 50 euro deductible in case of fraud instead of the previous €150. This new deductible amount does not apply when 3D Secure is not implemented. In other words, when two-factor authentication is successfully completed during a fraudulent payment, only the first €50 stolen is not reimbursed by the bank.
Conclusion
Analysis of the card payment fraud market and the responses implemented to combat it leads to the following observations:
- The fraudulent use of payment cards is a real threat because it represents ever-increasing financial losses, primarily for banks. The growth of online commerce inevitably leads to an increase in this type of fraud. This is made possible in particular by the diversity of techniques used to steal data payment cards and the specialization of fraud actors.
- The strengthening of authentication during payments, as mandated by the European PSD2 directive, does not appear to put an end to payment fraud. While it makes the task more difficult, However, it is still possible to make payments with stolen cards., in particular thanks to exceptions that allow double authentication to be avoided.
- Cyber Threat Intelligence plays a complementary role to other methods of combating bank fraud, particularly through the identification of stolen data as it is being put on the market. Thus, Cyber Threat Intelligence helps strengthen the fight against payment fraud by preventing the use of stolen payment cards.. Ultimately, it is simply a matter of responding to the specialization of fraudsters with a new specialty: cyber intelligence.
- The actors and methods of online payment fraud are constantly evolving. Under these conditions, a service having excellent knowledge and broad capacity to monitor fraud networks is able to help businesses, and more specifically banks, in this area.
[1] https://www.banque-france.fr/evenement/rapport-annuel-de-lobservatoire-de-la-securite-des-moyens-de-paiement-2019
[2] Article L133-18 of the Monetary and Financial Code
[3] https://www.phonandroid.com/fraude-a-la-carte-bancaire-le-skimming-debarque-sur-le-web.html
[4] Article L163-4 of the Monetary and Financial Code
[5] https://www.intrinsec.com/telegram/
[6] https://eur-lex.europa.eu/legal-content/FR/TXT/?uri=CELEX:32015L2366
[7] https://ec.europa.eu/commission/presscorner/detail/fr/QANDA_19_5555







